Search the Community
Showing results for 'Quick Launch Keyboard'.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Environment: Citrix Virtual Apps and Desktops (Citrix XenApp and XenDesktop) with enabled option Citrix UPL (User Personalization Layer) Citrix App Layer Non-English Operation System localization. After installation of KSV LA 5.2, you can face the error "The specified path does not exist" which appears by launching any executable file. Possible root cause Both Citrix technologies use separate vhd files for creating VMs by using Citrix App Layer and for roaming profiles used by Citrix UPL. As the result, the merge of vhd files processes and Citrix driver returns incorrect path of where the executable files are. Workaround Install Kaspersky Light Agent 5.2 and ensure it does not connect to SVM. Disable Self Defense and exit LA. Add registry file from this archive. Launch installation of the latest cumulative patch from the archive (all further released Cumulative PFs will contain the fix as well). As soon as LA informs the restart is needed, restart VMs. Connect LA to SVM. Problem should be solved.
-
From time to time my keyboard (not the virtual keyboard) freezes and I have to restart Kaspersky to fix the problem. This problem has been happening for more than a year. Windows 10 x64 build 19044 Kaspersky Security Cloud 21.3.10.391
-
Operating sysyem: Windows 11 but it was happening on Windows 10 as well Name: Kaspersky Internet Security Version: 21.3.10.391(i) Ever since I installed Kaspersky I'm having trouble launching Modern Warfare/Warzone. When I somehow get in after fiddling within Kaspersky exceptions and whatnot it doesn't let my game save, so it's blocking the game making changes on my PC I guess, and every time I restart PC I start having trouble again. Today it didn't even let me download an update for Warzone from Battle.net. No idea what to do anymore, I've put Warzone into exceptions or something, marked it as trustworthy, but none of it helped, and I'm stuck. Thank you for your replies in advance, hopefully someone else can find your information useful down the line.
-
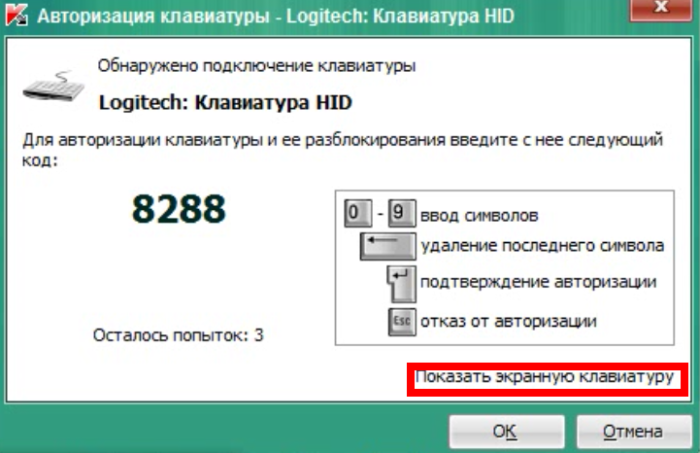
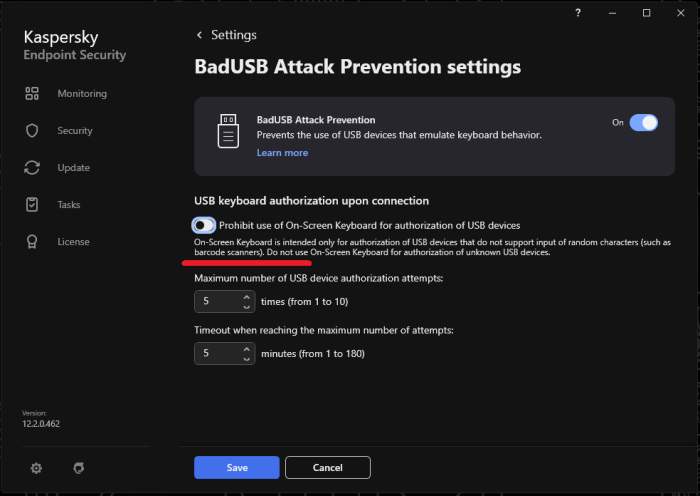
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Some devices do not have keyboards, but still are detected with BadUSB. Step-by-step guide In order to allow them work properly use BadUSB on-screen keyboard, using other onscreen keyboards or physical ones is not recommended. To open BadUSB on-screen keyboard click on the highlighted text (example for Russian localization). Note that Prohibit use of On-Screen Keyboard for authorization of USB devices option should be turned off.
-
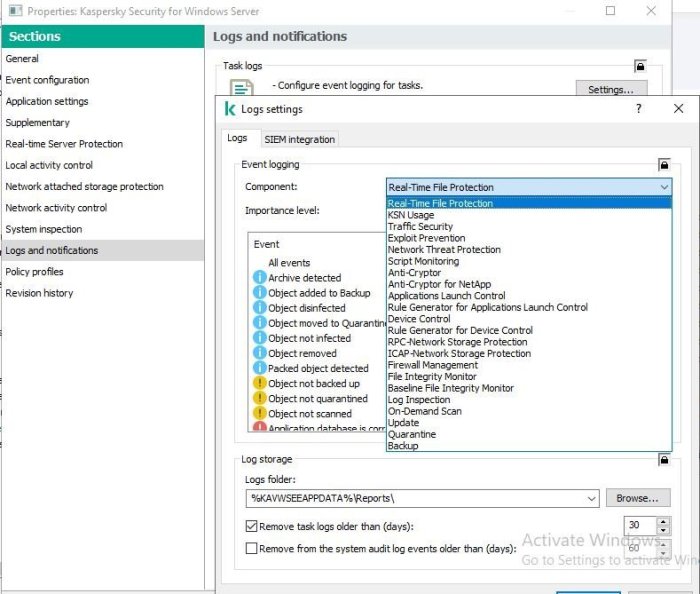
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Environment/Preconditions KSC - 12 KSWS - 11.0.1.897 You may find a massive increase in disk usage from the folder report under the Kaspersky folder. The size of the report folder will increase from around 2GB to 12GB, the files in the report folder have random name (like 340a13d9-2a50-4c4e-94d6-82a79d80da4b), which rapidly grows and consumes disk space. The file can be deleted to resolve the disk space full issue, which itself can cause many issues (can't log in to the server, KSWS stop, etc) To delete the file: Stop KSWS. Add permission/owner for the login account. Right-click and delete file. This issue is caused by the Task log setting under Log and Notification tab in the KSWS policy. To avoid the detailed events issue: Ensure that there are no Informational events in the Importance level option in each Component. Remove task logs older than (days) is selected. In case you do the above step and the random file is still keep growing rapidly (100 MB per hour), it may be causes by the flooding event. You can check the event flooding by using "DB Browser for SQLite". For example, the log above is generated by the Application launch control component. You may solve this issue by disabling Application launch control log.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. The article is giving a working configuration instructions for domain authentication by using NTLM and Kerberos protocols. NOTE: Domain authentication in OpenAPI over Kerberos protocol has the following restrictions: Administration Server address must be specified exactly as the address for which the Service Principal Name (SPN) is registered for domain account name. In the domain, you need to set the Service Principal Name (SPN) to publish the OpenAPI service on port 13299 for the machine with the Administration Server, the service of which is running under the name of the domain user <domain-user>. Kaspersky Security Center 13 Web Console user must be authenticated in Active Directory by using Kerberos protocol. Kerberos authentication should be allowed in web-browser. For details, refer to documentation of used web-browser. Details SPN - Service Principal Name Log in Domain Controller as Domain administrator. Open powershell as admin and run the following commands: Powershell setspn.exe -A HTTP/hostname-node-1.domain.local -u domain\user-ksc-service setspn.exe -A HTTP/hostname-node-2.domain.local -u domain\user-ksc-service Example setspn.exe -A HTTP/kscw-node-1.sales.lab -u sales\ksc setspn.exe -A HTTP/kscw-node-2.sales.lab -u sales\ksc setspn.exe -L -u sales\ksc #command for check spn records #Response Registered ServicePrincipalNames for CN=KSC Service,CN=Users,DC=sales,DC=lab: HTTP/kscw-node-1.sales.lab HTTP/kscw-node-2.sales.lab Enable Kerberos/NTLM authentication in web browsers Microsoft Edge \ Internet Explorer win + r => inetcpl.cpl Activate the Security tab. Select Local intranet and click Sites. In the opened dialog box click Advanced. Add the host name of Adaxes Web interface (e.g. host.company.com). Click Close and then click OK. Click Custom level. Navigate to Scripting and enable Active scripting. Navigate to User Authentication \ Logon. Select Automatic logon only in Intranet zone and click OK. Activate the Advanced tab. In the Settings list, navigate to the Security section. Select Enable Integrated Windows Authentication and click OK. Mozilla Firefox - https://developer.mozilla.org/en-US/docs/Mozilla/Integrated_authentication Launch Mozilla Firefox In the URL window, enter about:config and press Enter. In the filter text box, enter network.negotiate. Double-click the network.negotiate-auth.trusted-uris option and enter the host name of Adaxes Web interface (e.g. host.company.com). Repeat previous step for the network.negotiate-auth.delegation-uris option. Google Chrome Add the Software\Policies\Google\Chrome\AuthServerWhitelist key equal to *.<domain-name>.local to the registry Add the Software\Policies\Google\Chrome\AuthNegotiateDelegateWhitelist key equal to *.<domain-name>.local to the registry
-

Предложения к Kaspersky Password Manager
Августин Берендеев replied to supportIV's topic in Kaspersky Password Manager
Добавьте пожалуйста шорт каты https://ru.wikipedia.org/wiki/Сочетание_клавиш keyboard shortcut, quick key, access key, hot key Сворачивание программы в трей, сворачивание программы в панель задач, закрытие (выход из программы, с завершением процесса и службы), блокировку базы, создание новой карточки, редактирование уже существующей карточки, листание разных учёток в одной карточке, создание новой "группы", открытие настроек, синхронизацию, копирование значений из полей user name, password,переход к определенной группе "аккаунты/банковские карты/заметки/документы/" Раздельные горячие клавиши для копирование значения из поля "логин" в буфер обмена и отдельной клавиши для копирования значения из поля "пароль" (не ctrl+c) в буфер обмена. Нужно для того чтобы можно было alt+tab'абаться между программой и менеджером паролей. И копировать конкретное поле сразу, а не водить мышкой. например открыл steam чтобы залогиниться atl+tab, появилось окно менеджера ctrl+f, вод пары символов для поиска, из активной карточки (если нужная карточка не активна, "активируешь её стрелочками") нажимаешь ctrl+z (копировал в буфер логин), alt+tab открылось окно ввода в стим ctrl+v, alt+tab ctrl+x (копировал в буфер пароль) alt+tab ctrl+v. можете даже их за хардкодить, без возможности что-то настроить не нужно отвечать на моё предложение формулировкой "функция мало востребованная, маловероятно добавим", это нужно было сделать много лет назад ещё до запроса от пользователей, простите меня конечно, но программе больше 12 лет, и в ней всё ещё нету базовых вещей. За двенадцать лет можно было уже и с дистрибутивом под линукса определиться, и обеспечивать работу только на одном конкретном дистрибутиве. Почему такие простые вещие нужно выпрашивать у разработчика который претендует на место среди лидеров рынка? -
Quick startup keeps disabling some of my preferred startup items, I turn them back on thru the Kaspersky UI, It tells me to reboot. System then allows them all to run, but then Kaspersky Standard disables them again. How do I permanently turn OFF this **** and unwanted "Quick Startup" Lenovo kaptop, UEFI System AMD Ryzen cpu, 32gb ram, 2 x 512gb ssd, win 11 ver 2000.856
-
Quick fix: You can use OpenVPN Connect with configuration for router. https://my.kaspersky.com/VPN#/portal/pages/ksec
-
hello You 5.02.2024 23:13 How may i assist you today? Operator 5.02.2024 23:13 i was recently told to make a chat for a problem whit kapersky Threat Intelligence Portal You 5.02.2024 23:13 by a forum master You 5.02.2024 23:13 Okay, let me check on the issue details for you Operator 5.02.2024 23:14 ok You 5.02.2024 23:14 If you could please hold on for 1-3 minutes and I will check for you. Operator 5.02.2024 23:14 ok ill hold You 5.02.2024 23:15 Thank you, please wait Operator 5.02.2024 23:16 Thank you for waiting patiently Operator 5.02.2024 23:18 We are just trying to get more details on this, is that will be okay if I update you with an email within 24hours? Operator 5.02.2024 23:19 ok You 5.02.2024 23:19 We are just trying to get more details on this, is that will be okay if I update you with an email within 24hours? Operator 5.02.2024 23:19 like for messeges? You 5.02.2024 23:19 we will update you on email Operator 5.02.2024 23:19 well yes its okay You 5.02.2024 23:20 Sorry for the inconvenience caused. Operator 5.02.2024 23:20 Is there anything else I can help with before we end the chat? Operator 5.02.2024 23:20 no thats it thank you for the help You 5.02.2024 23:20 No worries. Please take note of the reference number for this chat: INC000016171813 If that is all for now, I will end this chat here and I would appreciate it if you could complete a quick survey about the support that I have provided. 😊 Thank you for contacting Kaspersky and have a nice day. 😉 Operator 5.02.2024 23:21 The conversation has been completed. Please feel free
-
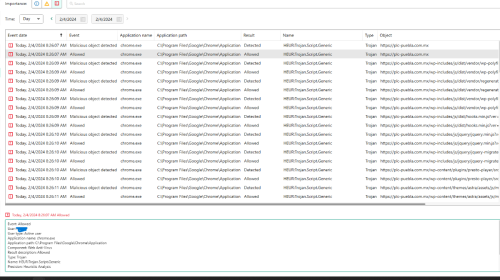
was doing some research for work, which involved visiting different companies websites. I was using Google Chrome when I was doing my research and when I was viewing this website I received 11 notifications in a row saying Malicious Object Detected from chrome.exe, unluckily all of them were allowed by Kaspersky. I performed a quick scan, restarted my computer, and did a full scan and all came out cleaned. . Since the results of all my scans are clean I was wondering if I have to be worried about anything. I'm not sure how to send reports, but I've attached screenshots of my Kaspersky reports:
- 3 replies
-
- windows 10
- chrome
-
(and 2 more)
Tagged with:
-
I've been using Total Security for at least 10 years and never had an issue until recently. I have a 2.5 year old PC HP laptop running Windows 10 and a 2 year old Android phone running whatever the latest update is. I extended my Kaspersky licence to my phone. I use the Chrome browser on both devices. Over the past 2 to 3 months (it's sept. 4, 2022), both devices have suddenly shut off while I was in the middle of something. Re: my phone, it's happened in the middle of me writing a text and in the middle of a phone call. On my laptop, it has happened while I was working in an excel document and while I was shopping online and about to hit the checkout button. Those are just the examples I can remember. I have been able to restart my phone afterwards but my laptop doesn't want to power on afterwards. I sometimes can't use it for hours. Once it was about 2 days before it would start again. At the moment, I'm not able to power it up and I don't know how to resolve that. Perhaps this is just coincidence but lately, I've been getting the occasional pop-up that tells me I've exceeded my 300 MBs of VON protection and offers a button for extended protection. I followed it once to find out it's trying to sell me an add-on. I've told it to get lost every other time. Has anyone else experienced any of the above? Does Kaspersky know about it? When I'm able to get back into my laptop, is there anything I can do so that it won't happen again? Thanks
-

How fast does Kaspersky truly start?
Guest replied to a topic in Kaspersky: Basic, Standard, Plus, Premium
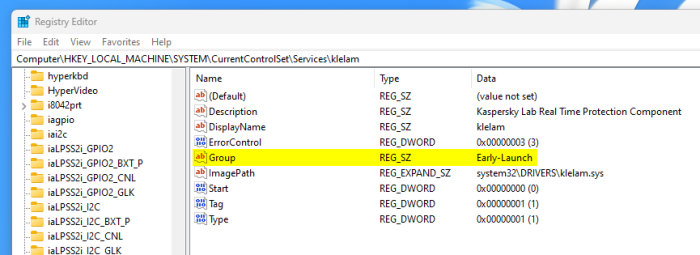
Once again I answer my own questions because I am too quick to post. After literally 5 minutes of research, I was able to find out that Kaspersky's drivers are indeed running as ELAM (Early Launch Anti-Malware) drivers: Probably obvious, but I wanted to make sure. And now anyone with the same question knows as well. -
Mouse/keyboard issues
fdavidl replied to George 44's topic in Kaspersky: Basic, Standard, Plus, Premium
I recently purchased a Crumar Performer that has some keyboard issues. The bottom C is completely dead and the other 4 C's have a very long sustain, regardless of where the slider is positioned in the Strings section. All the other keys are fine. I've taken it apart and cleaned the contacts but that hasn't helped at all. Any ideas? Thanks! -
Hello, I recently replaced Kaspersky Internet Security with Plus and I'm still getting my bearings in the new application. I have 2 questions about it: 1. How can I change the interface language from what came by default from the installer? The application installed in my region's language but I prefer it to be in English. So far I can't find a setting for changing that. 2. In KIS I was able to open the On-Screen Keyboard via the application's interface - either through the main window or via the context menu after right-clicking on the tray icon. I can't find how I can do this in Plus. I'm aware there is a keyboard shortcut but sometimes I have issues with my hardware keyboard so that shortcut is not always available to me. How can I bring the virtual one up using the mouse? I'm on Windows 10, app version is 21.14.5.462. Thanks!
- 1 reply
-
- 1
-

-
VPN Secure Connection fails to connect
Washand replied to Washand's topic in Kaspersky VPN Secure Connection
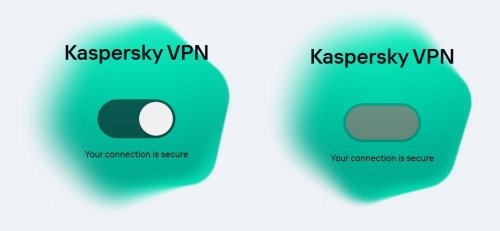
Well, it didn't last long... After a couple of days working, I'm now back with the same problem. This time, I can access the list of country servers, but if I select a different one, it does not change. If I click on the on/off toggle switch, the button disappears and the switch background turns green-red and it hangs forever until I quite with the "close" (X) icon. It states underneath that "Your connection is secure". A quick check of my IP address shows that the VPN is not working. I attach before click (left) and after click photos. -
Hello im using kaspersky endpoint security , I habe just upgraded my application and deployed to pc s but now the pc s are unusable due to kaspersky has blocked the keyboard and I cant press control alt delete. Can anyone help me please
-
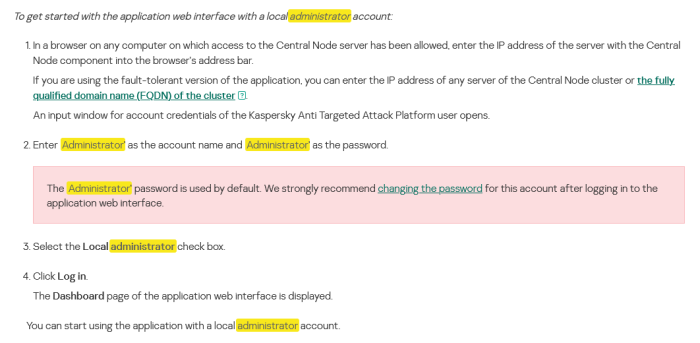
During installation, you had to set a password for the admin account, and after the first launch, log in under it and pre-configure the solution (in terms of performance) If this stage is passed, then to enter Administrator mode, enter your credentials login - Administrator password - Administrator Also, don’t forget to check the local login checkbox. After logging in, you can change this password to the one you need https://support.kaspersky.ru/KATA/6.0/en-US/247449.htm
-
Kaspersky Virus Removal Tool (KVRT) does not have a command line interface that allows fine-grained control over certain scanning components such as system memory, startup items, and boot sectors. However, you can influence the behavior of KVRT by adjusting settings through the interface. If you want to perform a targeted scan of specific folders and exclude other components, try the following steps: 1. Open Kaspersky Virus Removal Tool: – Kaspersky Launch the virus removal tool. Applications on your computer. 2. Configure scan settings:- Look for options that allow you to customize scan settings. This is usually available in the application's settings or preferences section. 3. Exclude system memory, startup items, and boot sectors: - Check your settings to see if there is an option to exclude specific components from scanning. Look for a checkbox or setting to scan system memory, startup items, and boot sector. Disable or disable these options if available. 4. Set scan destination: - Set the scan destination to the specific folder you want to scan. Most antivirus tools allow you to specify a custom scan path. 5. Start scan: - After adjusting settings to exclude unnecessary components and specifying folders to scan, start the scan. Please note that the exact steps and options may vary depending on the version of the Kaspersky Virus Removal Tool you are using. We recommend that you refer to your product documentation or help resources for detailed instructions specific to your version. If you're looking for a lightweight and customizable command-line antivirus tool, consider checking out other antivirus solutions that offer command-line options for targeted scanning. Please note that the specific features and options available may vary depending on your antivirus product.
-
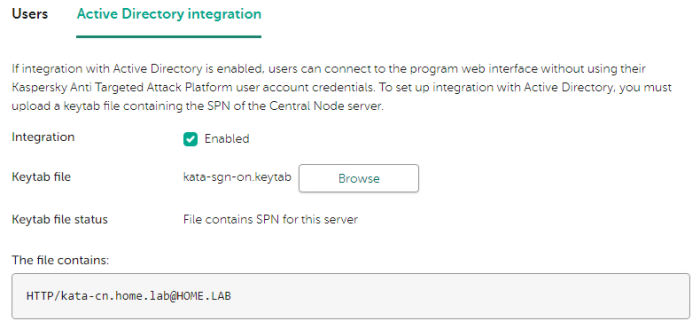
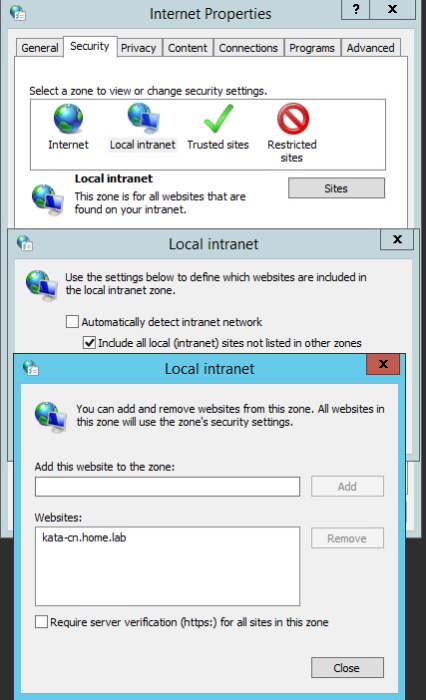
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. There is an example of a step-by-step instruction to configure Single-Sign-On (SSO) for KATA 4.1/5.0 into HOME.LAB domain. Prerequisites Deployed Central Node Server Name should be FQDN. (In current case FQDN name of Central Node - kata-cn.home.lab) It can be checked via Settings/Network Settings of Central Node. A and PTR record should be set for Central Node in DNS. Domain User Account should be created to set up Kerberos authentication by means of keytab file (in current case Domain User Account is kata-sign-on). AES256-SHA1 encryption algorithm should be enabled into created Domain User Account. Step-by-step guide to create keytab file On Domain Controller: Launch CMD As Administrator Execute the following command to create keytab file C:\Windows\system32\ktpass.exe -princ HTTP/kata-cn.home.lab@HOME.LAB -mapuser kata-sing-on@HOME.LAB -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass * +dumpsalt -out C:\TEMP\kata-sgn-on.keytab The utility requests the kata-sign-on user password when executing the command. The SPN of the selected server is added to the created keytab file. The generated salt is displayed on the screen: Hashing password with salt "<hash value>" For multiple Central Node servers you need to save "<hash value>" of hashing password to add an SPN for each subsequent Central Node servers further using ktpass.exe utility. On Central Node Web Interface Move to Settings/Users/Active Directory Integration Add the created keytab file: Keytab file status section contains File which contains SPN for this server The file contains section HTTP/*****@*****.tld Under Users tab click Add and select Domain user account. Set domain user as <username>@<domain> On client machine Host should be joined to the same domain. Domain user should be logged in with account added into the Central Node. Open Control Panel/Internet Options Click on Security and select Local Intranet Click on Sites and then on Advanced Add FQDN of central node - kata-cn.home.lab Close windows: Launch Web Browser and access to Web Interface of the Central Node https://kata-cn.home.lab:8443 and it should be opened without asking any Login/Password.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This instruction is relevant only in case of troubleshooting incorrect loading or rendering of a web page. In order to troubleshoot issues KES network traffic related issues traffic dump is required. It is easier to analyze and does not require third-party software installation. If reproduction of the issue requires the web browser to open web pages(such as web control non-working as expected, web page not loading, and so on), the tests should be performed in Incognito mode(also known as private browsing). Chrome browser: Ctrl+Shift+N or you can start browser from terminal: & "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" -incognito . Starting application from terminal will make launch key visible in traces and make diagnostic easier. Firefox browser: Ctrl+Shift+P or you can start browser from terminal: & "C:\Program Files\Mozilla Firefox\firefox.exe" -private-window . Starting application from terminal will make launch key visible in traces and make diagnostic easier. Microsoft Edge: Ctrl+Shift+P Opera browser: Ctrl+Shift+N KES11 Instructions Disable KES11 Self-defense Navigate to the following registry key: x86: HKLM\SOFTWARE\KasperskyLab\protected\KES\environment\ x64: HKLM\SOFTWARE\Wow6432Node\KasperskyLab\protected\KES\environment\ Create a string type value named DumpNetworkTraffic : DumpNetworkTraffic = (REG_SZ)"1" Restart the product or reboot the host Traffic dump files will be saved to %ProgramData%\Kaspersky Lab\KES\Data\traffic Once the issue is reproduced compress the whole traffic directory Do not forget to disable traffic dump collection. To do so delete DumpNetworkTraffic value.
-
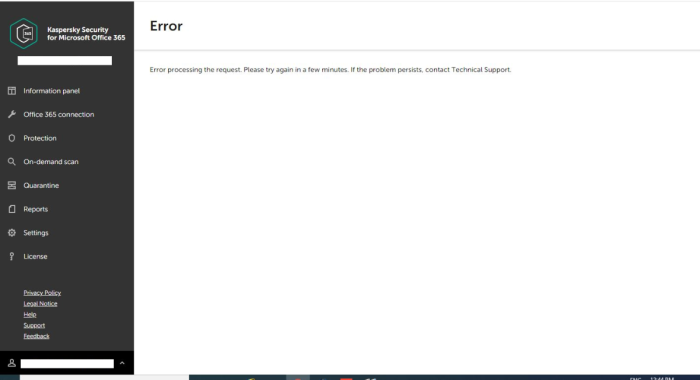
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. When administrator attempts to establish a connection between KS4O365 workspace and their Exchange online organization by doing the following in the administration console: Office 365 connection → Exchange Online connection → Grant Access → passes the consent validation algorithm but in the end gets the Error processing the request error: This error is usually triggered by the browser settings on the client host that is performing the consent validation. Upon executing consent validation algorithm we get the access token from Microsoft. Then we redirect browser to our web site's URL and attach access token as a cookie. Upon redirecting, cookie with access token is lost/blocked somehow, usually this is caused by one of the following reasons: Browser filters cookies on its own. For instance due to some extensions, browser settings, or due to some beta version of browser with paranoid default security settings. Some 3rd party program, for example a file anti-virus, is blocking access to the file with the browser's cookies on the local hard drive. Thus, the following action plan is suggested. Step-by-step guide Clear all history, cache and cookie in the web-browser, restart it and check the reproduction. If it doesn’t help, then please make sure that the same error occurs if you try to do the same operation in another web-browser supported by the product (https://support.kaspersky.com/KS4MO365/1.2/en-US/141858.htm) or in incognito mode of the browser. Also, temporarily disabling anti-malware solutions or any 3-rd party products that might be blocking/locking/inspecting browser's cookie files is called for. If the issue will persist, then please do the following: 1. Open Google Chrome web-browser. 2. Press F12 keyboard button. 3. Enable Preserve log option in Network tab. 4. Reproduce the whole scenario from the begging (log into business hub account) and the issue itself. 5. Make an error screenshot with time stamp. 6. Export Network debugging results to HAR-file. 7. Provide HAR-file + screenshot to the Kaspersky Support. Also we will be interested in the URL that will be shown when the error will pop-up in the browser.