Search the Community
Showing results for 'Secure Keyboard Input is enabled'.
-
Hello Jean, this is a normal confirmation popup when you try to change settings in KES. You can just limit the time for duration until it will be asking you again. Same would be happen when you set a password for KES in your policy. For any changes in local UI or disabling the policy by the tray icon you will be asked for confirmation. This is by design and need to make changes to KES more secure. If you think this is a problem open a ticket with technical support team Thank you in advance Best Regards
-
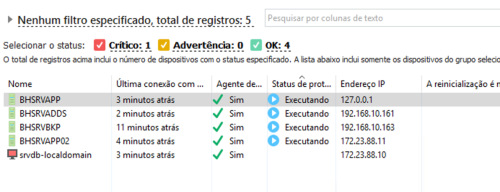
Hi Dear, I facing a problem to Install and configure Kaspersky Security for Linux on my Oracle Linux 8; I've installed the network Agent on my server, so what i did: 1. Copy the folder from KSC with the instalation package of network Agent to my Oracle Linux; 2. Add the repository with rpm -i agent<version> 3. Execute the installation script in /opt/kaspersky/agent The intalarion seems work well; in the same Second, I did able to visualize my server on the KSC (look to srvdb-localdomain); So I've tryed do the same process with the Kaspersky Security for Linux, to start the protection: 1. Copy the folder from the KSC with the kels package installion to my Oracle Linux 2. Add the RPM repository 3. Execute the installation script; And now my problems start The first Problem, when the instalation wizard finished, it return with the follow error Error: Job for kesl-supervisor.service failed because the control process exited with error code. See "systemctl status kesl-supervisor.service" and "journalctl -xe" fordetails. kesl not started So, I tried Install using the KSC, and I have the error: Event Name: Failed Severity: Functional Failure Application: Kaspersky Security Center Administration Server Version Number: 14.0.0.10902 Task Name: Deploy Kaspersky Endpoint Security 11 for Linux_11.0.0.2706 Device: srvdb-localdomain Group: Servers Time: Saturday, May 4, 2024 09:35:09 Name of Virtual Administration Server: N/A Description: Kaspersky Endpoint Security 11 for Linux (11.0.0.2706): Remote installation was completed with an error on this device: Installation script error So, i Back to my Oracle Linux tryng to troubleshoot the issue, and check the Services (systemctl status kesl-supervisor.service) and i get the error ● kesl-supervisor.service - kesl Loaded: loaded (/usr/lib/systemd/system/kesl-supervisor.service; enabled; vendor preset: disabled) Active: failed (Result: exit-code) since Sat 2024-05-04 09:58:50 -03; 2min 11s ago Process: 1895360 ExecStart=/var/opt/kaspersky/kesl/install-current/etc/init.d/kesl-supervisor start (cod> mai 04 09:58:50 srvdb-localdomain systemd[1]: Starting kesl... mai 04 09:58:50 srvdb-localdomain systemd[1]: kesl-supervisor.service: Control process exited, code=exited> mai 04 09:58:50 srvdb-localdomain systemd[1]: kesl-supervisor.service: Failed with result 'exit-code'. mai 04 09:58:50 srvdb-localdomain systemd[1]: Failed to start kesl. Someone can help to troubleshoot it, please? Thanks for the time.
-
В главном окне продукта красуется название продукта — «Kaspersky VPN»: При этом, иконка на рабочем столе называется «Kaspersky VPN Secure Connection»: Может, унифицировать название и сократить его? В чем польза этих километровых названий? Кто-нибудь реально использует полное название продукта? Чем короче, тем проще! Даже MSFT давно отказались от длинного «Microsoft Windows Internet Explorer» в пользу емкого и лаконичного «Microsoft Edge». P.S. Этот тикет был на eap.kaspersky.com, но не уверен, что он сохранился.
-
Kaspersky Auto-install apps enabled by default, why? It killed my installation of TeamViewer, needs to be repaired and meanwhile can't access my machine! Why would you have this enabled by default if you can't rely on it for updates? This is a very big no for me. Please can this setting be disabled by default?
-

Safe money doesn't block screenshots.
Flood and Flood's wife replied to cesarD's topic in Kaspersky Internet Security
Hello @cesarD, You're most welcome! Thank you for posting back & the extra question! And - it's wonderful to read - The screenshot is now black, so I guess it works! - that's a very good outcome - well done!! We first raised the issue with HQ experts in 2022, their final resolution came thru Feb 29th 2024, as follows: "You may find the SM documentation below in the section "About protection against screenshots" mentioning that screen capture with spyware is not possible: About protection of financial transactions and online purchases. In this case, only software based screen capture activities are blocked. The ability to take a screenshot is only possible by physically pressing the "PrtScr" key when it is needed by the user at the computer. It is also mentioned elsewhere in the "On-Screen Keyboard" section that screen capture using the "PrtScr" key cannot be prevented: About On-Screen Keyboard." We checked, the same information is also documented for v21.3 & the function worked as per design (for us), for that version too. Thank you🙏 Flood🐳+🐋 -
Ich hatte bis jetzt den Kaspersky Total Security (5 Geräte) und parallel den VPN Secure Connect (5 Geräte) aktiv. Nun habe ich ein Upgrade auf das neue Kaspersky Premium (5 Geräte) gemacht, dass ja den VPN als unlimitierte Version enthält. Das gesonderte VPN Abo läuft noch weiter. Nach meinen Verständnis habe ich dann 5 VPN Geräte aus Premium und 5 VPN Geräte aus dem VPN Abo - also in Summe 10. Sobald ich nun ein 6 Geräte bei VPN anmelden will, bekomme ich die Meldung, dass alle 5 Geräte schon vergeben sind und bekomme keine unlimitierte Lizenz. In der Abo-Übersicht sind alle Geräte bei den VPN Secure Connect aufgeführt. Ein Löschen des VPN Programms auf dem Gerät und VPN Neuinstallation über das Premium Programm hat auch keine Änderung gebracht. Das Gerät meldet sich trotzdem wieder über VPN Secure Connect an. Nun habe ich mal VPN Secure Connect komplett im Account deaktiviert. Jetzt wurden alle VPN Geräte unter Premium hinterlegt und funktionieren auch 5 unlimitiert und 1 begrenzt. Aktivere ich nun die Lizenz von VPN Secure Connect wieder im Account, dann werden alle Geräte automatisch wieder der VPN Secure Connect Lizenz zugeordnet. Gibt es eine Lösung wie ich die Geräte bzgl. VPN gezielt den Lizenzen Premium und VPN Secure Connect zuordnen kann, so dass ich dann auch die beiden gekauften Lizenzen vollständig nutzen kann? So wie es jetzt ist, ist die zusätzliche VPN Secure Connect Lizenz ja dann überflüssig. VG Wolfgang
-

Safe money doesn't block screenshots.
Flood and Flood's wife replied to cesarD's topic in Kaspersky Internet Security
Hello @cesarD, Thank you for posting back & the information! IF (you) are taking screenprints with the Safe Money browser open & pressing the Print-Screen Key on the Keyboard - according to the experts from HQ this is working exactly as per design = it's working properly in all elements, however, IF (you're) using a *print-screen* function from a third-party application & the Safe Money browser & the images shows an image(s), i.e., the screen is not black - according to the HQ experts - this is *not* working as designed. This information is also documented for v21.3, v21.6, v21.7 etc, etc.... Thank you🙏 Flood🐳+🐋 -

Safe money doesn't block screenshots.
Flood and Flood's wife replied to cesarD's topic in Kaspersky Internet Security
Hello @cesarD & @nexon, We've discussed this issue in a logged case - in the past with HQ: SafeMoney & PrintScreen do work & SafeMoney, On-Screen Keyboard & PrintScreen also do work, i.e. screen-prints are not *black*. HQ experts advised: "software-based screen capture activities are blocked. The ability to take a screenshot is only possible by physically pressing the "PrtScr" key when it is needed by the user at the computer." @cesarD, we agree with @nexon, IF Kaspersky Standand is available in (your) region, it's advisable to upgrade. The software is available to download from this link: https://www.kaspersky.com/downloads#update-product. Kaspersky has replaced KIS & with Kaspersky Standard, there's no information available atm as to when KIS will be withdrawn; information about the *new* software range can be read here: Kaspersky: Basic, Standard, Plus, Premium - info & FAQ, by Danila T. Any questions or issues, please post back? Thank you🙏 Flood🐳+🐋 -

NAS is blocked after upgrading to Premium?
Netz replied to Netz's topic in Kaspersky: Basic, Standard, Plus, Premium
Hi Yes - Both is enabled -
Вообще не работает ни один VPN - в чем дело?
Friend replied to Travelnok's topic in Kaspersky Secure Connection
К какому серверу в этот момент пытается подключится программа? Какая версия программы установлена? Какая операционная система? Попробуйте переустановить программу Kaspersky Secure Connection следующим образом: 1. Удалите программу стандартным образом. 2. Перезагрузите компьютер. 3. Скачайте и установите последнюю версию Kaspersky Secure Connection или по этой ссылке. 4. Подключите к My Kaspersky. -

Kaspersky premium VPN
Flood and Flood's wife replied to C700's topic in Kaspersky: Basic, Standard, Plus, Premium
Hello @C700, Thank you for posting back & the information. Read this: Suspended sales in India: Kaspersky has now suspended sales of Kaspersky VPN Secure Connection in India: it will no longer be available as a standalone product, or as a component inside Kaspersky Plus, Kaspersky Premium or Kaspersky Small Office Security. In instances where the paid version of Kaspersky VPN Secure Connection has already been activated – as a standalone product, or as a component in Kaspersky Plus, Kaspersky Premium or Kaspersky Small Office Security – it will continue to work until the end of the subscription period. Auto-renewal will continue to work as usual. If you have an active paid subscription purchased in India which includes VPN, and you’re having trouble installing or updating your app, please follow the instructions below. For Android, iOS or macOS, please contact Kaspersky Customer Service. ===== Re: "You can see the pics i shared before it was limited to 300mb but now it's finished." (ioo) that is due to action taken by KCS *after* you contacted KCS. (ioo) this "paid version of Kaspersky VPN Secure Connection has already been activated it will continue to work until the end of the subscription period." - applies to your subscription - ask support why it doesn't? Please share the outcome with the Community, when it's available? Thank you🙏 Flood🐳+🐋 -
Вообще не работает ни один VPN - в чем дело?
Travelnok posted a topic in Kaspersky Secure Connection
Я новый пользователь. Купил сегодня подписку Secure Connection/ Собственно ради VPN. А он не подключается ни к одному из серверов, перепробовал кучу стран ЕС и казахстан Грузию - везде картина одна, идет циклично по кругу соединение-разрыв-... В чем дело? Интернет домашний от МТС, на компьютере win 10 нахожусь в Москве -
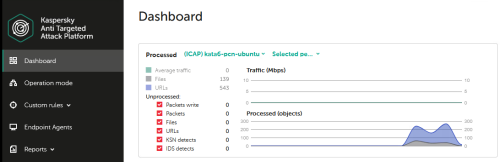
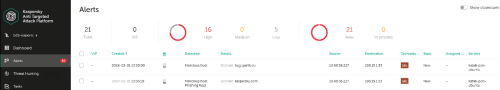
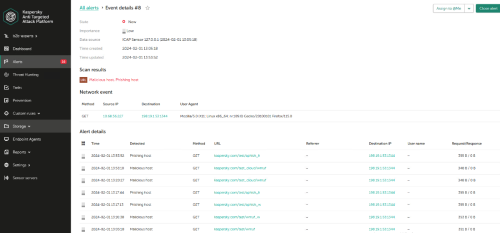
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Sometimes it's necessary to check KATA detects, for example IDS, IOA, Sandbox detects. Step-by-step guide IDS detects (SPAN) To check IDS detects (SPAN) you can use tcpreplay utility on server configured to receive SPAN traffic. KATA 4.0/4.1 tcpreplay package for such versions could be found here https://rhel.pkgs.org/7/epel-x86_64/tcpreplay-4.4.4-1.el7.x86_64.rpm.html KATA 5.+ and tcpreplay tcpreplay package is not installed by default, so you should install it manually, using step-by-step guide below: 1) Download this package from HERE 2) Place downloaded file tcpreplay_4.3.2-1build1_amd64.deb to your KATA node. For example, use scp: [user@host]$ scp <your-path>/tcpreplay_4.3.2-1build1_amd64.deb admin@<kata-ip>:/tmp 3) Run installation on your KATA node with the next command: [admin@katahost]$ sudo dpkg -i /tmp/tcpreplay_4.3.2-1build1_amd64.deb Success! Now you can use tcpreplay on your KATA 5.+ or any other UBUNTU system! Before using tcpreplay you should enable tx capture for span: KATA 3.7.* In technical support mode from user root run following commands : systemctl stop apt-preprocessor.service systemctl stop suricata.service rmmod pf_ring Edit file /etc/modprobe.d/pf_ring.conf: change line: options pf_ring enable_tx_capture=0 min_num_slots=16384 # tx capture is disabled to: options pf_ring enable_tx_capture=1 min_num_slots=16384 # tx capture is enabled save file. Start pfring and related services back: modprobe pf_ring systemctl start suricata.service systemctl start apt-preprocessor.service KATA 4.0/4.1 Edit file /etc/modprobe.d/pf_ring.conf: change line: options pf_ring enable_tx_capture=0 min_num_slots=16384 # tx capture is disabled to: options pf_ring enable_tx_capture=1 min_num_slots=16384 # tx capture is enabled save file. In technical support mode from user root run following commands: systemctl stop docker rmmod pf_ring modprobe pf_ring systemctl start docker tx capture for span is now enabled KATA 5.0/5.1/6.0 - see https://forum.kaspersky.com/topic/how-to-enable-tx-capturing-in-kata-katakedre-37514/ Eicar traffic detect: Upload EICAR-Test-File_TCP.pcap sample to server with SPAN interface, then execute command from root shell: tcpreplay -i ens34 EICAR-Test-File_TCP.pcap # ens34 in this example is SPAN interface Nmap traffic detect: Scenario is the same as for Eicar detect, only .pcap file differs (# tcpreplay HackTool.Nmap.HTTP.C&C.pcap). After testing detects from span we strongly recommend to disable tx capture back again by the same way as described above for enabling. AM Engine Use EICAR's - https://www.eicar.com/ Email - send the EICAR via SMTP to KATA 25 port. (SMTP processing needs to be Enabled of course). ProTip: you may use local swaks mail client on CN to skip elaborate mail setups. swaks examples swaks --server 127.0.0.1 --port 25 --from antony@test.org --to cleopatra@test.org --attach eicar.com swaks --server 127.0.0.1 --port 25 --from antony@test.org --to cleopatra@test.org --body "link_to_EICAR_here" Endpoint - put an EICAR file to the endpoint and fetch it using GetFile task, queue for scanning. YARA detects By default, no YARA rules are supplied with the product. For test purposes one can use a test rule from YARA docs https://yara.readthedocs.io/en/v4.1.0/writingrules.html rule ExampleRule { strings: $my_text_string = "text here" $my_hex_string = { E2 34 A1 C8 23 FB } condition: $my_text_string or $my_hex_string } The rule will mark any analyzed object containing $my_text_string or $my_hex_string. IoA detects To check IoA detect (IoA detects can be checked only if you have KEDR license): Copy .bat file from attached archive Test_IOA.rar(not_infected) to any folder on host with installed EDR and start it. After some time(KATA need several minutes to transmit and process telemetry from EDR) check alerts in KATA. Alert should have type ioa_test_detect. For testing IoA detects on host more than once, .bat file should be placed to different locations on this host. On the host with installed KEA run command below in the cmd.exe shell: wmic.exe sfdguninstallkasperskyblabla There can be something else instead of sdfg and blabla, important part of command is uninstallkaspersky Command execution will fail with error, but it's not important. After some time new IoA detect should appear in KATA web-interface. IoC detects One can use the custom rule for testing - Ioctest.zip (infected123) - it is triggered for "c:\windows\system32\calc.exe" Automatic sandboxing in EDR To check automatic sandboxing: Unpack the archive with sample, use default password for samples: autosbtest.zip NB! Do not change MD5 of the sample. Run the sample on EDR-protected host and wait for automatic SB detect: Sandbox detect To check sandbox detect we can use file SA_sleep.exe from archive no_am_detection sample.rar. Password is inside text document in archive. Go to KATA senior security officer web-interface. Choose Storage → Upload and upload SA_sleep.exe from attached archive for KATA checking. Kata should enqueue it to sandbox , then a bit later verdict from SB should be Suspicious Activity. If SA_sleep.exe produces Not detected verdict then please use test_sb.bat from the test_sb.rar URL reputation Firstly, confirm K(P)SN is configured and works properly. MD5 used in this example should return UnTrusted status: Check KSN on KATA command for KATA 4.+ and 5.0: docker exec -it `docker ps | grep ksn_proxy| awk '{print $1}'` /opt/kaspersky/apt-ksn_proxy/sbin/ksn_client --ip 127.0.0.1 --hash 9C642C5B111EE85A6BCCFFC7AF896A51 for KATA 5.1: docker exec -it $(docker ps | grep ksn_proxy| awk '{print $1}') /opt/kaspersky/apt-ksn-proxy/sbin/ksn_client --ip 127.0.0.1 --hash 9C642C5B111EE85A6BCCFFC7AF896A51 Secondly, For traffic: access http://bug.qainfo.ru/TesT/Aphish_w/index For email (SMTP processing needs to be Enabled), send the link above via e-mail. For quick and dirty test: swaks examples swaks --server 127.0.0.1 --port 25 --from fisherman@test.org --to cleopatra@test.org --body "http://bug.qainfo.ru/TesT/Aphish_w/index"
-
Hello @AndreaG, Welcome! IF the LG is an Android TV?, perhaps OpenVPN will help: Kaspersky VPN Secure Connection can generate .ovpn file to use with OpenVPN clients, installed on your device. This file contains connection credentials to import to the device, where secure connection needs to be established. OpenVPN clients are built in, or can be installed in various devices including routers, Android TV and on a wide range of operating systems including Windows, Android, iOS, MacOS, and Linux. Please read: How to set up a connection via OpenVPN, & please note: the first point in the procedure: Go to the Secure connection tab = in (your) MyKaspersky account, go to this page: - https://my.kaspersky.com/VPN#/portal/pages/ksec OR select the VPN tab Please share the outcome with the Community, when it's available? Thank you🙏 Flood🐳+🐋
-
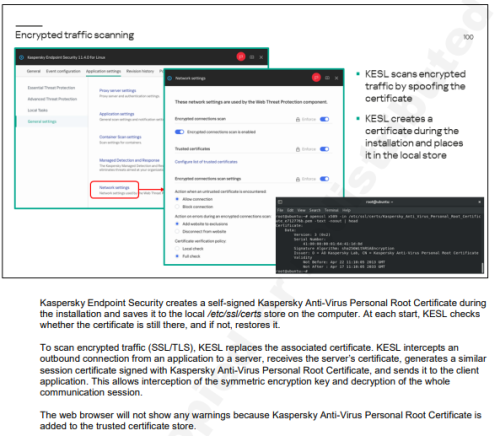
Hi I have readen thi Linux course of Kaspersky Endpoint Security and reached to the topic that was about "how kasperksy scan encrypted traffic?" and A question has arisen for me that how Kaspersky's Self-sign certificate participate in TLS/Handshake proccesses?How does it spoofed it self ?what contents does it have? I konw that it uses Man In The Middle to sacn the traffic but I have confused what role takes on the self-sign certificate in the whole proccess.
-
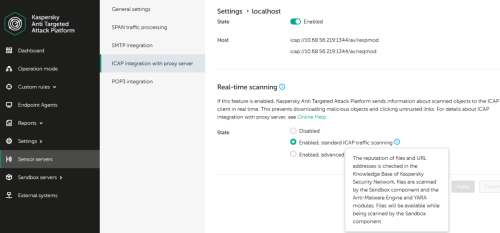
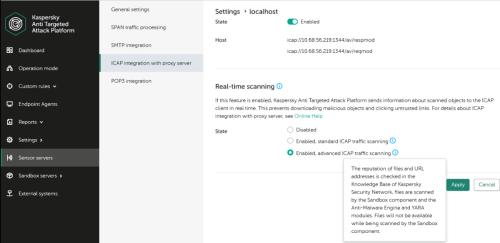
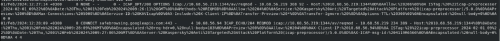
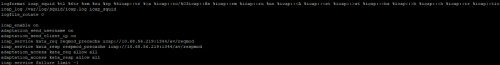
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Don't forget to install 6.0.1 patch, which fixes some bugs in ICAP integration. Description and cautions Since we have new ICAP working modes, presented in KATA 6.0 - https://support.kaspersky.ru/KATA/6.0/en-US/247269.htm , we would like to show you, how to configure such integration on example of squid proxy server. Added ICAP integration with feedback. ICAP integration with feedback can work in two modes: Standard scan. In standard scan mode, the object is scanned by all supported technologies. While being scanned by the Sandbox component, the object remains available. If a threat is detected, the object is blocked. Advanced scan. In the advanced scan mode, objects are scanned by all supported technologies. While being scanned by the Sandbox component, the object is not available. If a threat is detected, the object is blocked. Details Reminder - this is just an example, but working one:) Squid configuration part Assuming you already have squid installed with default configuration (of course, yours could be different according to your infrastructure), add following lines in the end of /etc/squid/squid.conf (surely, change the IP address to yours) icap_enable on adaptation_send_username on adaptation_send_client_ip on icap_service kata_req reqmod_precache icap://10.68.56.219:1344/av/reqmod icap_service kata_resp respmod_precache icap://10.68.56.219:1344/av/respmod adaptation_access kata_req allow all adaptation_access kata_resp allow all icap_service_failure_limit -1 The only thing we changed here as well is at the start of squid.conf - source subnet, in order to adapt server to our Lab # # Recommended minimum configuration: # # Example rule allowing access from your local networks. # Adapt to list your (internal) IP networks from where browsing # should be allowed acl localnet src 10.68.56.0/23 We also recommend to add these lines below as well, so you would be able to analyze ICAP logs logformat icap_squid %tl %6tr %rm %ru %rp %6icap::tr %>a %icap::to/%03icap::Hs %icap::rm %icap::ru %un %icap::<A %icap::<st %icap::>st %icap::<bs %icap::>h %icap::<h %icap::tr %icap::tio icap_log /var/log/squid/icap.log icap_squid ICAP logs are located at /var/log/squid/icap.log and look like So the whole picture should look like this Testing part If standard scan mode is enabled, let's check on KATA side, how it looks like in /var/log/kaspersky/services/preprocessor_icap/preprocessor_icap.log grep --color 'blocking_simple mode' | grep 'verdict' In this example we can see that from URL file was scanned with verdict: clean (whitelist) 09:41:46.697 INF 137781 server/source/file_handler_respmod.cpp:435 [sid: 0x0000004d] RESPMOD: Finish processing file in blocking_simple mode (request url: 'r3.o.lencr.org', size: 503, filename: 'baf664a8a7841e1d057f5ab0da58bcf0', uuid: 5cc2d18781924f98b6e4961494125616, md5: baf664a8a7841e1d057f5ab0da58bcf0, format: GeneralBin), processing time: 0.147ms, verdict: clean (whitelist) File from URL with verdict: clean (cached) 09:40:14.476 INF 137778 server/source/file_handler_respmod.cpp:435 [sid: 0x0000004a] RESPMOD: Finish processing file in blocking_simple mode (request url: 'detectportal.firefox.com/success.txt?ipv6', size: 8, filename: 'success.txt', uuid: 25f155a67eff4a4a90b33dbbb4f3367c, md5: ae780585f49b94ce1444eb7d28906123, format: GeneralTxt), processing time: 0.124ms, verdict: clean (cached) URL with verdict: good (KSN) 09:42:37.334 INF 137780 server/source/file_handler_reqmod.cpp:187 [sid: 0x0000004c] REQMOD: Finish processing url in blocking_simple mode ('box.kaspersky.com'), processing time: 3ms, verdict: good (KSN) File from URL verdict: clean (scanned) 09:35:14.691 INF 137770 server/source/file_handler_respmod.cpp:435 [sid: 0x00000042] RESPMOD: Finish processing file in blocking_simple mode (request url: 'detectportal.firefox.com/success.txt?ipv4', size: 8, filename: 'success.txt', uuid: 4c87c81cf3d543ceb6694d917329d2b8, md5: ae780585f49b94ce1444eb7d28906123, format: GeneralTxt), processing time: 124.894ms, verdict: clean (scanned) URL with verdict: bad (KSN) 10:05:18.354 INF 137802 server/source/file_handler_reqmod.cpp:187 [sid: 0x00000062] REQMOD: Finish processing url in blocking_simple mode ('kaspersky.com/test/wmuf'), processing time: 146ms, verdict: bad (KSN) If advanced scan mode is enabled, let's check on KATA side, how it looks like in /var/log/kaspersky/services/preprocessor_icap/preprocessor_icap.log grep --color 'blocking_advanced mode' | grep 'verdict' Picture is pretty the same, but from browser side you will see that object is blocked/inaccessible 10:54:01.341 INF 139635 server/source/file_handler_reqmod.cpp:187 [sid: 0x0000000e] REQMOD: Finish processing url in blocking_advanced mode ('bug.qainfo.ru/test_cloud/wmuf'), processing time: 27ms, verdict: bad (KSN) 10:54:20.467 INF 139635 server/source/file_handler_reqmod.cpp:187 [sid: 0x0000000e] REQMOD: Finish processing url in blocking_advanced mode ('secure.eicar.org:443'), processing time: 0ms, verdict: good (KSN) 10:50:45.303 INF 139632 server/source/file_handler_respmod.cpp:435 [sid: 0x0000000b] RESPMOD: Finish processing file in blocking_advanced mode (request url: 'ocsp2.globalsign.com/gsorganizationvalsha2g3', size: 1461, filename: 'gsorganizationvalsha2g3', uuid: f88dd52252da4fdf8aaabc3aafdbdb0a, md5: 9a3ec48893b2952f013e03311b878e18, format: GeneralBin), processing time: 0.346ms, verdict: clean (whitelist) During tests at KATA web UI you should see activity on ICAP dashboard and under Security office we can see two alerts, generated after our tests (10.68.56.227 is squid IP address) In real world, of course, you will see other detects as well, for instance, on infected objects and malicious URLs.
-
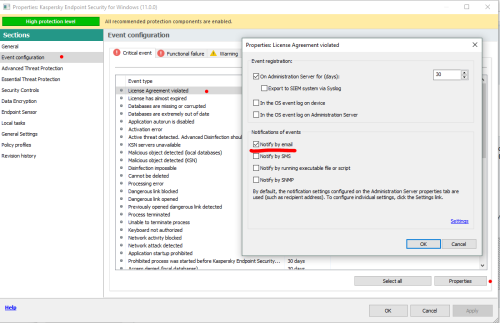
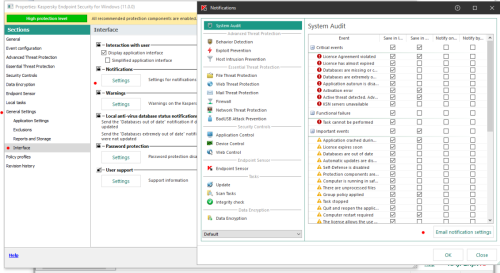
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. There are multiple settings in both KES and KSC that allow to set notifications about various events. This article is based on example of setting complaint notification (message send to administrator if the users considers the blocking of the page to be mistaken). Let's review three main scenarios, when KES is connected to KSC (either constantly or intermittently) and when it is not connected. KES is always connected to KSC How to set To set address for email notifications go to Administration Server properties -> Notification delivery settings -> Notification and input email into Recipients filed. To enable email notifications do the following Open KES policy Navigate to KES policy -> Event notification -> Warning -> Web page access blockage message to administrator Press Properties Mark Notify by email checkbox What to expect Once the user will fill the form (way to change default complaint message will be covered later in this article) and press Send, Network agent will send event to KSC. Once KSC will receive it, email notification will be send to administrator. The default email will look like this: Event "%EVENT%" happened on computer %COMPUTER% in the domain %DOMAIN% on %RISE_TIME% %DESCR% %EVENT%, %COMPUTER%, %DOMAIN%, %RISE_TIME% are self explanatory, while %DESCR% may rise some questions. This part will be substituted the whole message that the user put in to the complaint form. You can change format of the email at Administration Server properties -> Notification delivery settings -> Notification. Note that it will affect all email notifications KES in not connected to KSC How to set Open KES GUI Navigate to Settings -> Endpoint control -> Web Control and press Templates Switch to Message to administrator tab Input address for notifications into To field Change Subject of the email and notification text if required. Open General Settings -> Interface -> Notifications Settings configure SMTP client connection settings in "Email notification settings" menu of Notifications. What to expect Once the user will fill the form (way to change default complaint message will be covered later in this article) and press Send, KES will send email to specified address. It will contain everything user put into the form. KES is connected to KSC from time to time How to set Follow the steps described in KES is always connected to KSC section. This will set KES for the time it has connection to KSC Do the same as described in KES is not connected to KSC with only difference – make changes to policy not KES local settings. This will set KES for the time when it is not connected to KSC: Open KES policy Navigate to Endpoint control -> Web Control and press Templates Set email address that will receive notifications when KES is not connected to KSC Change Subject of the email and notification text if required. What to expect When KES has connection to KSC you will receive message from KSC described in KES is always connected to KSC section. When KES has no connection to KSC you will receive email from KES described in KES is not connected to KSC section. The same goes for cases when out-of-policy is used. How it works As noted earlier, when you manage KES using Kaspersky Security Center you can specify two methods of email notification delivery, both of them could be configured in KES policy. KSC settings Open KES policy properties navigate to “Event configuration”, select event that you are interested in, mark “Notify by email” In this case, network agent transport will be used to deliver notification to KSC, then KSC will send an email to specified recipients. If you tracing KES activity, specialized information will be recorded in KES.version.date.time.PID.connector.log and KES.version.date.time.PID.SRV.log for each event sent by Nagent transport. KES settings Open KES policy, General Settings -> Interface -> Notifications Settings, leave tick marks in column "Notify by email" next to events that you are interested. Also you will have to configure SMTP client connection settings in "Email notification settings" menu of Notifications. In this case, KES will send emails using it’s own mail client, from computer where event was registered. KES actions will be recorded in KES.version.date.time.PID.SRV.log
-
I entered a website in Chrome and received a download refused notification from Kaspersky, but when I enter the same website in the Brave browser, I do not receive a notification. Kaspersky not working in Brave?
-
So nach einigen Test habe ich eine Umgehungslösung gefunden. Es ist tatsächlich so, dass sich Kaspersky Premium und VPN Secure Connect auf einem Account nicht mit einander vertragen und man dann nur die 5 Geräte von der VPN Lizenz nutzen kann. Ich habe nun einen neunen Account 2 unter my.Kaspersky angelegt und die VPN Secure Connect Lizenz vom Account 1 auf 2 übertragen. Unter dem Account 1 haben sich nun alle VPN Lizenzen wieder automatisch auf die Premium Lizenz angehangen und haben unlimitiertes Volumen. Auf dem 6. Geräte habe ich dann in der VPN App den Account von 1 auf 2 umgestellt. Das VPN Programm hat dann 1 Gerät aus der VPN Secure Connect Lizenz des Account 2 gezogen und auf unlimitiert gesetzt. Damit ist es nun möglich die gekauften 10 VPN Lizenzen (5 über Premium und 5 über VPN Secure Connect) auch über den Umweg von 2 Account voll zu nutzen. Ist jetzt etwas umständlich aber funktioniert als Umgehungslösung. @Kaspersky Team: Ihr könntet das ja mal prüfen, da scheint es noch einen Fehler zu geben, dass man die beiden Programme nicht unter einem Account voll nutzen kann. Es müsste möglich sein in der VPN App die Lizenz auf Premium oder VPN Secure Connect zuzuordnen. Über eine Antwort ob es ein Fehler ist, der evtl. noch behoben wird oder es nur über 2 Accounts geht würde ich mich freuen. VG Wolfgang
-
I installed Kaspersky Total Security today, with a one year subscription. However, after it did a scan and restarted the computer, my keyboard and mouse have stopped responding. I tried other keyboards and mice, both wired and wireless as well but it did not work. But they still work on the biOS screen of the pc. I could not find a recovery boot option. So I would like to have help with this.
-
Доброго времени суток! 🙂 Собственно, требуется быстрый, надёжный и стабильный VPN с безлимитным трафиком для задачи, не нарушающей законодательство РФ. А именно, нужно зарегистрировать зарубежный Steam-аккаунт, например, в Казахстане или Турции, для покупки недоступных на территории РФ игр. Kaspersky Secure Connection может обеспечить всё это? И если да, то как это сделать? К слову, много лет являюсь держателем подписки Kaspersky Internet Security.
-
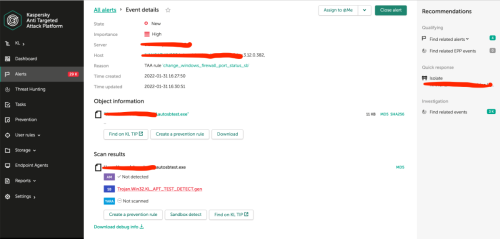
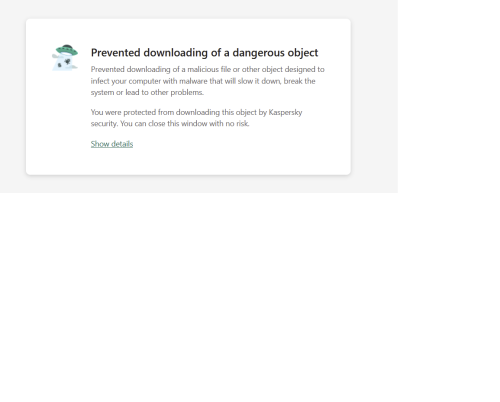
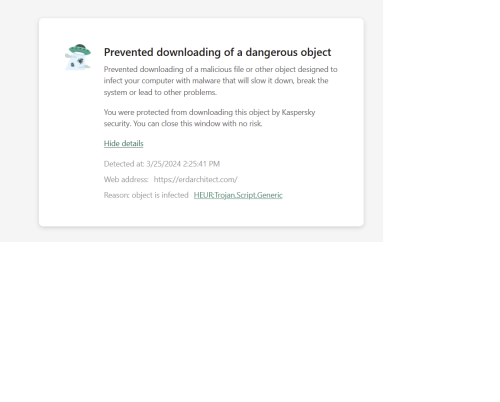
Hello, I am trying to connect to the ERD Architect Data Modeler website (it is "erdarchitect.com" and is an https site but for obvious reasons I am not putting the full URL here in this note) and Kaspersky keeps indicating that there is a dangerous object trying to download. This object is the Heur:Trojan.script.generic trojan. This occurs in both Firefox and Brave browsers which would be expected. I understand that it is possible the site is in fact infected but I would like to confirm. I recall reading on the Kaspersky site about providing the same information as above in another area of the site so it can be reviewed. Unfortunately, I cannot recall where this is to submit this. I have also included screenshots as well. Can someone direct me to this area so I can see if it is in fact an issue or a false positive? Thank you
- 2 replies
-
- windows 10
- trojan
-
(and 1 more)
Tagged with:
-
Hast du möglicherweise noch andere, ältere Versionen Von Kaspersky VPN bzw Secure Connect installiert ? Schau mal in die Programmliste.