All Activity
- Past hour
-
Может ли вирус с удалённым доступом не показываться в списках приложений внутри антивируса в моём случае?
mikj replied to mikj's topic in Kaspersky Total Security
Есть какие-то способы их проверить?- 2 replies
-
- windows 10
- kts
-
(and 1 more)
Tagged with:
-
Vadim63 joined the community
-
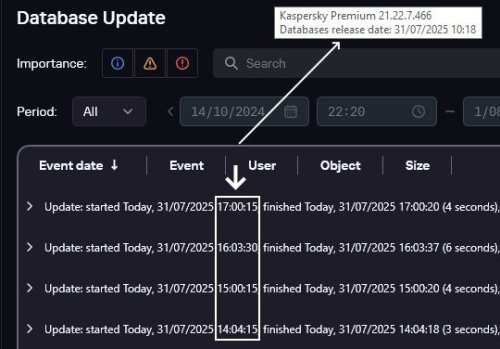
@tistou77 Bonjour, ↓ Sans nouvelles bases de données (10:18) affichage dans les rapports (14:04 - 15:00 - 16:03 - 17:00) ↓
-
Может ли вирус с удалённым доступом не показываться в списках приложений внутри антивируса в моём случае?
Maratka replied to mikj's topic in Kaspersky Total Security
Может. В списках не появляются драйвера.- 2 replies
-
- windows 10
- kts
-
(and 1 more)
Tagged with:
-
Более понятное продолжение моего прошлого поста с подозрением на бекдор из-за редких и безвредных, но непонятных вещей, происходящих с компьютером. Прошлый можно не читать, так как там по факту я не сформулировал нормальный вопрос. В антивирусе регулярно проверяю списки запускаемых/работающих приложений и сетевую активность. Никаких подозрительных приложений там нет. Только системное/с доверенностью по базе антивируса/софт Steelseries с моим разрешением/и абсолютно без всего процесс Registry, но это, кажется, норма. Соответственно, маскироваться ничего не может. Остаётся лишь узнать, может ли что-то просто не появляться в списках.
- 2 replies
-
- windows 10
- kts
-
(and 1 more)
Tagged with:
-
Schulte started following Kaspersky VPN & Security ( Android ) benötigt enorm Speicherplatz
-

Kaspersky VPN & Security ( Android ) benötigt enorm Speicherplatz
Schulte replied to Blacklandy's topic in Für Privatanwender
Hallo @Blacklandy, da scheint etwas aus dem Ruder gelaufen zu ein. Auf meinem Samsung belegt Kaspersky gerade mal ein GB, allerdings benutze ich es recht wenig. Mein Phone empfiehlt auch die Löschung der .apk. Das ist die Installationsdatei der Anwendung, theoretisch brauchst Du sie nicht (ist auch bei mir nur 203 MB). Mich hat noch eine PN von @Flood and Flood's wife zum Thema erreicht. Demnach kannst Du erstmal in der Kaspersky-App die Berichte löschen. Bei meiner Version geht das über unten rechts "Profil", dann "Einstellungen", dann ganz unten "Berichte". - Today
-
цаыф joined the community
-

Kaspersky VPN & Security ( Android ) benötigt enorm Speicherplatz
Blacklandy replied to Blacklandy's topic in Für Privatanwender
Ach so, da gäbe es ja noch die Möglichkeit Daten und Cache in der App zu löschen. Cache hätte ich keine Bedenken - aber bei den Daten ( 75,49 GB ) habe ich doch große Bedenken. -

Kaspersky VPN & Security ( Android ) benötigt enorm Speicherplatz
Blacklandy posted a topic in Für Privatanwender
Frage an die Fachleute hier im Forum. Heute meldet mein Samsung, dass ich von 128 GB Speicher nur noch 7,5... übrig habe. Habe mal nachgesehen und festgestellt, dass Kaspersky alleine davon ca. 79 GB für sich veranschlagt. Meine Frage ist nun - ist das normal ? Dann schlägt mir Samsung vor ich solle u.a . eine Datei kaspersky.apk löschen um Speicherplatz zu erhalten. Habe ich natürlich nicht gemacht, da ich überhaupt nicht weis, a) was ist das für ne Datei und b) was passiert bei eine Löschung. ( Sind eh nur schlappe 202mb ). Hat jemand einen Tip auf Lager. Habe schon einige Apps runtergeschmissen - bringt aber nicht viel. Danke für Eure Tips und Grüße aus dem Bergischen. -
_Сергей_ joined the community
-

My domain has been flagged
harlan4096 replied to erikjoylink's topic in Virus and Ransomware related questions
-
special_K started following Suivez nos actualités sur Telegram & WhatsApp
-
🔔 Ne manquez aucune information importante sur nos solutions professionnelles Pour rester informé des dernières actualités concernant nos solutions de sécurité pour les entreprises — nouvelles versions, cycle de vie, maintenances cloud, évolutions de la base de connaissances, etc. — abonnez-vous à nos canaux officiels : 📲 Telegram : https://t.me/kl_support_en 📲 WhatsApp : https://kas.pr/cs_whatsapp 📷 Ou scannez ce QR code pour accéder directement à notre canal WhatsApp : 💡 Notifications essentielles, directement sur votre mobile — sans surcharge inutile.
-
- 1
-

-
Как в KRD 2018 включали PPPoE? Надёжного способа нет. Можно сделать на флешке руками второй раздел, например файловой системы EXT. Из KRD закрыть утилиту KRT, из меню вызвать очистку данных, создать папку KRD2024_Data в корне созданного раздела, перезагрузить KRD, проверить что в KRD2024_Data появили папки. Если появились, значит базы должны качаться на флешку. Тут проблема что если такая шлефка будет запускаться на системе где уже сканировали через KRD и есть KRD2024_Data, то KRD будет путаться какую брать.
-
Какая минимальная версия android поддерживается Kaspersky Safe Kids?
Friend replied to Александр Доманский's topic in Kaspersky Safe Kids
-
svc_kms started following KEA SSL Error: WINHTTP_CALLBACK_STATUS_FLAG_SECURITY_CHANNEL_ERROR [Kaspersky Endpoint Agent]
-
The article is applicable to KEA 3.x (any cf) as part of [KATA+]EDR solution. 1.1. Problem Some hosts (usually server, eg. Windows Server 2012 R2) will not appear in CN dashboard after being configured using correct settings, including a valid TLS certificate. In the known case, such Endpoint Agents were configured locally using the command line, not via policy; however, we were able to verify that the same configuration led to successful connection on most hosts. During troubleshooting, you should be able to find the following events in WEL, Schannel errors are present: Log Name: System Source: Schannel Event ID: 36871 Level: Error Description: A fatal error occurred while creating a TLS client credential. The internal error state is 10013. In KEA traces you should be able to find the following lines: SSL Error: WINHTTP_CALLBACK_STATUS_FLAG_SECURITY_CHANNEL_ERROR internal error kata.compression=true kata.sync_period=300 kata.certificate=[...] kata.servers=10.231.132.146:0; syslog.enable=false syslog.type=CEF syslog.server=: 0 The connection port is displayed as 0. This persists even though the port used by default is 443 (as it is on non-affected hosts), or if we specify the port in the configuration string like this: C:\Program Files (x86)\Kaspersky Lab\Endpoint Agent\agent.exe" --message-broker=enable --type=kata --servers=<servername>:443 --tls=yes --pinned-certificate=”%~dp0kata.crt 1.2. Cause Most common cause - TLS 1.2 is disabled (usually for Server OSes) Some of the ciphers are missing Alternative cause Recently it was found out that the problem persists on desktops (Win 10) with all the TLS1.2 keys and ciphers in place, when there is "CryptoPRO CSP" software installed, specifically following versions: CryptoPRO CSP - 4.0.9944 CryptoPRO CSP - 4.0.9958 1.3. Solution For KEA 3.11 and older - Upgrade KEA to the latest version. Ensure "КриптоПро CSP" is not listed in installed applications For Windows 2012R2 - install KB2919355 Enable TLS 1.2. Exhaustive article in Russian https://winitpro.ru/index.php/2022/04/19/vklyuchit-protokol-tls-1-2-windows/ Script to enable all the keys from the article @echo off reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" /v DisabledByDefault /t REG_DWORD /d 0 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" /v Enabled /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" /v DisabledByDefault /t REG_DWORD /d 0 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" /v Enabled /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHTTP" /v DefaultSecureProtocols /t REG_DWORD /d 2720 /REG:32 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /v SchUseStrongCrypto /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /v SchUseStrongCrypto /t REG_DWORD /d 1 /REG:32 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /v SystemDefaultTlsVersions /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" /v SystemDefaultTlsVersions /t REG_DWORD /d 1 /REG:32 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" /v SchUseStrongCrypto /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" /v SchUseStrongCrypto /t REG_DWORD /d 1 /REG:32 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" /v SystemDefaultTlsVersions /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" /v SystemDefaultTlsVersions /t REG_DWORD /d 1 /REG:32 /f Ensure the following registry keys for TLS 1.2 are present (it is possible to check using GSI6 report): Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2] [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] "DisabledByDefault"=dword:00000000 "Enabled"=dword:00000001 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] "DisabledByDefault"=dword:00000000 "Enabled"=dword:00000001 Ensure the following registry value for WinHttp API: 32-bit: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp 64-bit: HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp "DefaultSecureProtocols" = dword:00000AA0 0x0000AA0 — allow TLS 1.1 and TLS 1.2 in addition to SSL 3.0 and TLS 1.0; Allow following ciphers on the server in order to match KATA CN (old and outdated are not allowed from security point of view) - For Windows 2012 R2 it is necessary to add and enable TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 One can do this via MS documentation like this - https://docs.microsoft.com/en-us/windows/win32/secauthn/tls-cipher-suites-in-windows-server-2022: ECDHE-RSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-SHA384 ECDHE-ECDSA-AES256-SHA384 ECDHE-RSA-AES128-GCM-SHA256 ECDHE-ECDSA-AES128-GCM-SHA256 ECDHE-RSA-AES128-SHA256 ECDHE-ECDSA-AES128-SHA256 Ciphers can be enabled using tool called IISCrypto, it can be used to tweak TLS/SSL, cipehrs and Schannel with GUI - https://www.nartac.com/Products/IISCrypto/ Reboot for the settings to take effect - !Restart required!
-
Berny started following KIS blocking a programs https call (Mordhau)
-

KIS blocking a programs https call (Mordhau)
harlan4096 replied to beoxtc's topic in Kaspersky Internet Security
Welcome to Kaspersky Community. I would migrate 1st Your KIS to Kaspersky Standard, KIS getting obsolete, and then re-test.- 1 reply
-
- 1
-

-
harlan4096 started following KIS blocking a programs https call (Mordhau)
-
Danila T. started following Какая минимальная версия android поддерживается Kaspersky Safe Kids?
-
Какая минимальная версия android поддерживается Kaspersky Safe Kids?
Danila T. replied to Александр Доманский's topic in Kaspersky Safe Kids
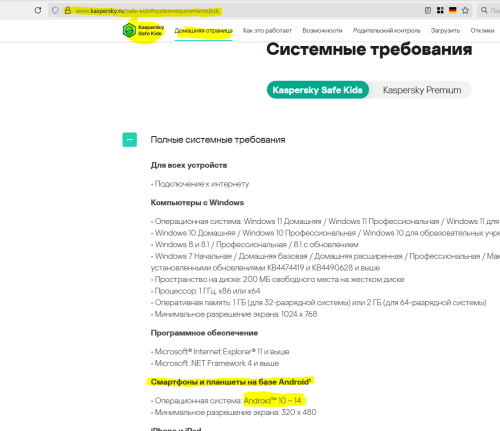
Добрый день: https://support.kaspersky.com/KSK/Mob1.0-iOSTR106-AndroidTR108/ru-RU/94957.htm операционная система: Android 7 и более поздние; -

it-sa - Europas größte Fachmesse für IT-Sicherheit in Nürnberg
alexcad posted a topic in Für Unternehmen
Hallo Zusammen, auch dieses Jahr findet im Oktober die it-sa in Nürnberg statt: 7. - 9. Oktober 2025 Messezentrum Nürnberg https://www.itsa365.de/de-de/it-sa-expo-congress Vielleicht sehen wir uns am Kaspersky-Stand? Halle 7 Stand 312! https://www.kaspersky-dach.de/kaspersky-it-sa-2025/ Grüße Alex -
beoxtc started following KIS blocking a programs https call (Mordhau)
-
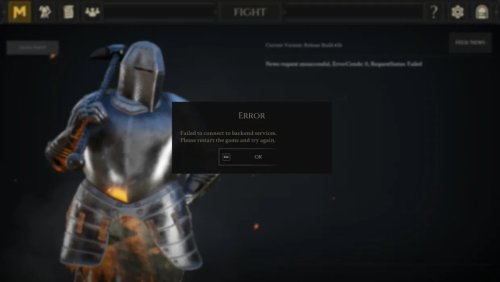
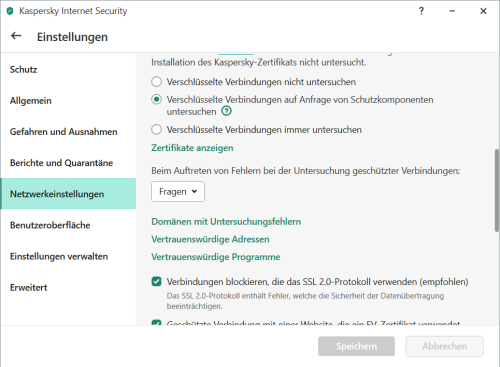
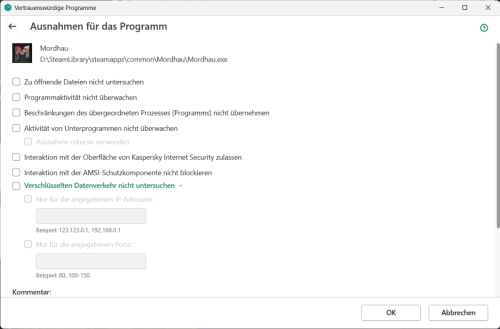
Hello there, Version of your operating system: Windows 11 Version 24H2 (OS Build 26100.4652) Name and version number of the Kaspersky application: 21.3.10.391 (m) When starting Mordhau (a game on Steam), I'm experiencing an error message. Digging into the logs, it seems that part of the SSL messages can't get through. Disabling KIS totally helps to get past this problem. I couldn't yet isolate that problem. Another problem related to this one: Whenever I want to add Mordhau to the list of exceptions for programs, Kaspersy crashes. Otherwise I'd just add a rule to omit that game. On the second screenshot, when I press OK, KIS crashes and I'm sending the reports to you. If necessary, attach a screenshot of the problem You can read my troubleshooting with the game developers in this discord thread https : //discord.com/channels/275436245318893568/1399120255774756895 In the logs ``` [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: request failed, libcurl error: 35 (SSL connect error) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 0 ( Trying 20.42.182.108...) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 1 (TCP_NODELAY set) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 2 (Connected to 12D56.playfabapi.com (20.42.182.108) port 443 (#1)) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 3 (ALPN, offering http/1.1) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 4 (Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 5 (TLSv1.3 (OUT), TLS handshake, Client hello (1):) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 6 (OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to 12D56.playfabapi.com:443 ) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 7 (Closing connection 1) [2025.07.30-23.19.09:635][ 21]LogPlayFabAPI: Error: RetryRequest: LoginWithSteam request exhausted retries (1) [2025.07.30-23.19.09:635][ 21]LogPlayFabAPI: Error: LoginWithSteam: Request Timeout or null response (2 Request Timeout or null response) [2025.07.30-23.19.09:636][ 21]LogMordhauGameInstance: Error: Platform login failed, Reason: Login failed ``` Please help, either with the Mordhau problem, or the exceptions problem, either one I'm ok with as long as I can play my game with it. Cheers, tempx
-
Александр Доманский started following Какая минимальная версия android поддерживается Kaspersky Safe Kids?
-
Какая минимальная версия android поддерживается Kaspersky Safe Kids?
Александр Доманский posted a topic in Kaspersky Safe Kids
Какая минимальная версия android поддерживается Kaspersky Safe Kids? Нигде не нашёл данной информации. У ребёнка старый смартфон Redmi Note 4X. -
Александр Доманский joined the community
-
beoxtc joined the community
-
С этим стоит обратиться в техподдержку.
-
привет! такая проблемка.. на андроид 11 телефоне стоит касперский впн, стали переставать работать страны впн, хотя наверное это глюк.. в общем выбираешь страну(например аргентина) через некоторое время перестает работать интернет, переключаешься на другую - работает.. страны запоминает, повторно не работает.. хотя наверное это блажь..
-
clavo joined the community
-
Magdy joined the community
-
greendalf joined the community
-
Добрый день, @Mi14ek, Какая версия Mac OS? Все обновления Mac OS установлены? В других приложениях работает? Попробуйте переустановить Kaspersky Password Manager: 1. Удалите стандартным образом Kaspersky Password Manager 2. Перезагрузите устройство. 3. Скачайте и установите последнюю версию.
-
1.1. Scenario: KATA/EDR CN is deployed on site, and there are some remote users that cannot connect to the internal network, and you want to receive the EDR telemetry from those endpoints and laptops when they are outside the network (considering that you don't have any VPN functionality). You don't want to expose the CN on the internet, so you'd like to use the sensor to relay the telemetry to the CN and have visibility on the endpoints. 1.2. Pre-requisites and configuration steps: To achieve the above scenario, we can deploy the KATA Network Sensor in the DMZ and publish it on the internet for remote and roaming users. The Network Sensor will be integrated with the CN and public IP/FQDN will be used to send the traffic from the internet to the sensor using port 443. Two KES policies (Active/Out of Office) will be configured, The Active policy will have the KATA CN internal IP and the Out-of-Office policy will have the public IP/FQDN for KATA Sensor. Connection profiling can be used to switch between the policies (similar to the connection gateway for KSC). The below steps need to be performed for the successful deployment and integration. Deploy the KATA Network Sensor in the DMZ Configure to integrate with CN, and accept the request on the CN side. When using the KEDR license, the Accept button might not be available, integration of the KATA sensor requires a KATA license, or the latest KATA patch should be applied on the CN to fix this issue. Export the certificate from the KATA Sensor using WinScp and copy it to the local computer or KSC server. Note: you might need to allow the connection using WinSCP: https://forum.kaspersky.com/blogs/entry/100-how-to-copy-files-tofrom-kata-katakedre/ Location of the certificate = /etc/pki/tls/certs/ File name = kata.crt Copy the kata.crt to /tmp/ and change the permissions to download the file. Configure the destination NAT from Firewall towards KATA sensor internal IP for port 443. Configure the KES (Out-of-office) policy and add the Public FQDN/IP in the connection settings along with the sensor certificate. Apply the KES (Out-of-office) policy to a test laptop. Disconnect the Laptop from the network and wait for the connection to be established from the internet with KATA Sensor. Verify the Endpoint status on the Central Node and check for the recent events.
-
Description and cautions This article may be useful in certain cases, when you see that virtual machines running on the KATA Sandbox can not access internet using the properly configured malware interface. One can notice the issue based on several symptoms, such as VM activation errors, samples sent to Sandbox for processing not accessing internet, etc... We recommend to use the following article to check if the malware channel works properly on the KATA Sandbox server or not: https://forum.kaspersky.com/blogs/entry/162-how-to-test-malware-interface-on-kata-sandbox-katakedre/ Details In case if the tests listed above indeed show that malware channel fails to connect to the internet, we recommend to do the following checks among others: Run the following command on the sandbox server to check the currently configured network settings for the Sandbox: # /opt/kaspersky/sandbox/bin/sbnetworking all show check in the command's output if the malware interface is configured properly, i.e. it's intended IP, subnet, gateway, etc. Example of such output below: Correct values if they are misconfigured somehow from the web interface and don't forget to apply the settings afterwards and restart the host, to propagate those (prompt for restart will pop-up in the Sandbox web interface after applying those). Run the following command to check the system log on the Sandbox server if there are certain errors related to networking in general and malware interface in particular: # journalctl -u network # journalctl -u sandbox-networking.service In case if all checks listed above were passed, and there are no misconfigurations found and/or no specific errors were found in system journal, then try checking if routing is properly configured for the malware channel, i.e. run the following command: # ip route show table 701 Expected output below: if the output will be missing the default route entry via configured gateway for the malware interface, then add it manually like so: # ip route add default via <gateway's IP> table 701 after adding the route, double check that it indeed exists: # ip route show table 701 then restart the sandbox-networking service manually or the Sandbox server itself: # systemctl restart sandbox-networking.service Please note, that restarting sandbox-networking service may take a while especially on production servers that are processing a lot of samples at the moment and/or have a lot of worker slots. Thus it is highly recommended to detach this Sandbox server from KATA for the time of restart and expect 40 minutes - several hours downtime to complete the procedure. after restarting the sandbox-networking service check if you can ping public locations successfully from internet interface's namespace: # /opt/kaspersky/sandbox/bin/ns_exec /var/run/netns/dom1 /bin/ping -c 3 8.8.8.8
-
Melaku Mara joined the community
-
KSC API use cases examples - host isolation with KES/KEA [KSC for Windows]
svc_kms commented on svc_kms's blog entry in Kaspersky Security Center's Kaspersky Security Center Community
KES Isolation (11.7 and upper) FindHost Find Host with previous method and copy value "KLHST_WKS_HOSTNAME" For example: "KLHST_WKS_DN":"KEDRO-1","KLHST_WKS_HOSTNAME":"a20da5de-49e5-469a-92ea-41b5adb74ea4" SrvView Find srvview data by filter string (SrvView::ResetIterator) "wstrViewName" - check List of supported srvviews. "vecFieldsToReturn" - check https://support.kaspersky.com/help/KSC/13.1/KSCAPI/a00307.html SrvView::ResetIterator POST /api/v1.0/SrvView.ResetIterator HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 614 { "wstrViewName": "HostTasksSrvView", "vecFieldsToReturn": [ "nState", "strTask", "TASK_NAME", "txtDisplayName", "TASKID_PRODUCT_NAME", "TASKID_PRODUCT_VERSION", "bCannotBeDeleted", "bSystem" ], "vecFieldsToOrder": [ { "type": "params", "value": { "Name": "TASK_NAME", "Asc": "true" } } ], "lifetimeSec": 100, "pParams": { "strHostId": "a20da5de-49e5-469a-92ea-41b5adb74ea4" }, "wstrFilter": "" } Response ID Response {"wstrIteratorId":"67D74142AE0FA1A3D05CD696B957902B"} GetRecordRange from Response data (SrvView.GetRecordRange) SrvView.GetRecordRange curl -L -X POST "https://127.0.0.1:13299/api/v1.0/SrvView.GetRecordRange" -H "X-KSC-Session: noOxgI9Ny7O5Whg/97qvcVg==" -H "Content-Type: application/json" --data-raw "{ \"wstrIteratorId\":\"67D74142AE0FA1A3D05CD696B957902B\", \"nStart\": 0, \"nEnd\": 100 }" Copy value "strTask" for Task "xdr_networkisolation_start" and "xdr_networkisolation_stop" For example: Isolation ON => "TASK_NAME":"xdr_networkisolation_start" .... "strTask":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056" Isolation OFF => "TASK_NAME":"xdr_networkisolation_stop .... "strTask":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d" Isolation ON GetHostTasks Return server specific identity to acquire and manage host tasks. (HostGroup::GetHostTasks) HostGroup.GetHostTasks POST /api/v1.0/HostGroup.GetHostTasks HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 58 { "strHostName":"a20da5de-49e5-469a-92ea-41b5adb74ea4" } Response: Response {"PxgRetVal":"8122017D5C4081753E8FDE94244DC1AF"} HostTasks GetTaskData Acquire task settings. (HostTasks::GetTaskData) strSrvObjId - server object ID that got from HostGroup.GetHostTasks strTask - storage identifier of the task (such as returned by HostTasks.AddTask) HostTasks::GetTaskData POST /api/v1.0/HostTasks.GetTaskData HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 112 { "strTask":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056", "strSrvObjId":"8122017D5C4081753E8FDE94244DC1AF" } Response: Response {"PxgRetVal":{"EVENT_TYPE":"PRTS_EVENT_NONE","FILTER_EVENTS_COMPONENT_NAME":"","FILTER_EVENTS_INSTANCE_ID":"","FILTER_EVENTS_PRODUCT_NAME":"","FILTER_EVENTS_VERSION":"","TASKID_COMPONENT_NAME":"Connector","TASKID_INSTANCE_ID":"","TASKID_PRODUCT_NAME":"KES","TASKID_VERSION":"11.0.0.0","TASKSCH_FIRST_EXECUTION_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASKSCH_FIRST_EXECUTION_TIME_SEC":0,"TASKSCH_LIFETIME":{"type":"datetime","value":""},"TASKSCH_MS_PERIOD":0,"TASKSCH_RUN_MISSED_FLAG":false,"TASKSCH_TYPE":0,"TASK_ADDITIONAL_PARAMS":{"type":"params","value":{"CompatibilityInfo":{"type":"params","value":{"MinimalPluginVersion":"11.7.0.0"}},"PRTS_TASK_EXT_SHEDULE_FLAGS":0,"exclusionRules":[{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}},"name":"DNS","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}},"name":"DNS","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":true,"paths":["%systemroot%\\system32\\dns.exe"]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":65535,"start":49152}}]}},"name":"Large numbered TCP ports, randomly assigned by the RPC service","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":true,"paths":["%systemroot%\\system32\\svchost.exe"]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":135,"start":135}}]}},"name":"RPC Endpoint Mapper","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":0,"localPorts":{"type":"params","value":{"enabled":false,"portRange":[]}},"name":"DNS client","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":0,"localPorts":{"type":"params","value":{"enabled":false,"portRange":[]}},"name":"DNS client","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":2,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":68,"start":68}}]}},"name":"DHCP server","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":67,"start":67}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":2,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":67,"start":67}}]}},"name":"DHCP client","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":68,"start":68}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":2535,"start":2535}}]}},"name":"MADCAP","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":647,"start":647}}]}},"name":"DHCP failover","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}}],"isolationDuration":3600000,"klprts-TaskStorageId":"_LOCAL_2d076fbe-7e60-4a99-9177-173076a5a2b1","ksc_settings_compatibility::TaskUniqueId":"89621cce@xdr_networkisolation_start@NetworkIsolationStart","responseId":{"type":"long","value":7998665773575485050}}},"TASK_CLASS_ID":0,"TASK_DEL_AFTER_RUN_FLAG":false,"TASK_INFO_PARAMS":{"type":"params","value":{"DisplayName":"Network isolation","klprts-TaskCannotBeDeleted":true,"klprts-TaskScheduleSubtype":256}},"TASK_LAST_EXEC_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASK_LAST_EXEC_TIME_SEC":0,"TASK_MAX_EXEC_TIME":0,"TASK_NAME":"xdr_networkisolation_start","TASK_PREP_START":0,"TASK_PRIORITY":1,"TASK_START_DELTA":0,"TASK_UNIQUE_ID":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056"}} Copy some of value from response and change parameters on next request with Network isolation exclusions RDP protocol (for example): exclusionRules { "type": "params", "value": { "applications": { "type": "params", "value": { "enabled": true, "paths": [] } }, "dataSource": 2, #inbound and outbound "localPorts": { "type": "params", "value": { "enabled": true, "portRange": [ { "type": "params", "value": { "end": 3389, #port "start": 3389 #port } } ] } }, "name": "RDP ANY", #name "protocol": { "type": "params", "value": { "enabled": true, "id": 0 #TCP and UDP } }, "remoteAddress": { "type": "params", "value": { "enabled": false, "ip": { "type": "params", "value": { "octets": { "type": "binary", "value": "" }, "zoneIPv6": "" } } } }, "remotePorts": { "type": "params", "value": { "enabled": false, "portRange": [] } } } } UpdateTask Modify task settings. ( HostTasks::UpdateTask) HostTasks::UpdateTask Collapse source POST /api/v1.0/HostTasks.UpdateTask HTTP/1.1 Host: localhost:13299 X-KSC-Session: n18Zfc+1hPeedqD07uM96/A== Content-Type: application/json Content-Length: 32796 { "strTask": "_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056", "strSrvObjId": "46A9BEBC82C3FB1121050247A0697ECC", "pData": { "TASKID_COMPONENT_NAME": "Connector", "TASKID_PRODUCT_NAME": "KES", "TASKID_VERSION": "11.0.0.0", "TASKSCH_TYPE": 5, "TASK_ADDITIONAL_PARAMS": { "type": "params", "value": { "CompatibilityInfo": { "type": "params", "value": { "MinimalPluginVersion": "11.8.0.0" } }, "PRTS_TASK_EXT_SHEDULE_FLAGS": 0, "exclusionRules": [ { "type": "params", "value": { "applications": { "type": "params", "value": { "enabled": true, "paths": [] } }, "dataSource": 2, "localPorts": { "type": "params", "value": { "enabled": true, "portRange": [ { "type": "params", "value": { "end": 3389, "start": 3389 } } ] } }, "name": "RDP ANY", "protocol": { "type": "params", "value": { "enabled": true, "id": 0 } }, "remoteAddress": { "type": "params", "value": { "enabled": false, "ip": { "type": "params", "value": { "octets": { "type": "binary", "value": "" }, "zoneIPv6": "" } } } }, "remotePorts": { "type": "params", "value": { "enabled": false, "portRange": [] } } } } ], "isolationDuration":28800000, "klprts-TaskStorageId":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056", "ksc_settings_compatibility::TaskUniqueId":"89621cce@xdr_networkisolation_start@NetworkIsolationStart", "responseId":{"type":"long","value":4294967295}}}, "TASK_CLASS_ID":0, "TASK_DEL_AFTER_RUN_FLAG":false, "TASK_INFO_PARAMS": {"type":"params","value":{ "DisplayName":"Network isolation", "klprts-TaskCannotBeDeleted":true, "klprts-TaskScheduleSubtype":512} }, "TASK_NAME":"xdr_networkisolation_start", "TASK_PREP_START":0, "TASK_PRIORITY":1, "TASK_START_DELTA":0, "TASK_UNIQUE_ID":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056" } } Response Response { } Host isolated successful with allowed RDP session. Isolation OFF For example: Isolation OFF => "TASK_NAME":"xdr_networkisolation_stop .... "strTask":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d" GetHostTasks Return server specific identity to acquire and manage host tasks. (HostGroup::GetHostTasks) HostGroup.GetHostTasks POST /api/v1.0/HostGroup.GetHostTasks HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 58 { "strHostName":"a20da5de-49e5-469a-92ea-41b5adb74ea4" } Response: Response {"PxgRetVal":"8122017D5C4081753E8FDE94244DC1AF"} HostTasks GetTaskData Acquire task settings. (HostTasks::GetTaskData) strSrvObjId - server object ID that got from HostGroup.GetHostTasks strTask - storage identifier of the task (such as returned by HostTasks.AddTask) HostTasks::GetTaskData POST /api/v1.0/HostTasks.GetTaskData HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 112 { "strTask":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d", "strSrvObjId":"8122017D5C4081753E8FDE94244DC1AF" } Response: Response {"PxgRetVal":{"EVENT_TYPE":"PRTS_EVENT_NONE","FILTER_EVENTS_COMPONENT_NAME":"","FILTER_EVENTS_INSTANCE_ID":"","FILTER_EVENTS_PRODUCT_NAME":"","FILTER_EVENTS_VERSION":"","TASKID_COMPONENT_NAME":"Connector","TASKID_INSTANCE_ID":"","TASKID_PRODUCT_NAME":"KES","TASKID_VERSION":"11.0.0.0","TASKSCH_FIRST_EXECUTION_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASKSCH_FIRST_EXECUTION_TIME_SEC":0,"TASKSCH_LIFETIME":{"type":"datetime","value":""},"TASKSCH_MS_PERIOD":0,"TASKSCH_RUN_MISSED_FLAG":false,"TASKSCH_TYPE":0,"TASK_ADDITIONAL_PARAMS":{"type":"params","value":{"CompatibilityInfo":{"type":"params","value":{"MinimalPluginVersion":"11.8.0.0"}},"PRTS_TASK_EXT_SHEDULE_FLAGS":0,"klprts-TaskStorageId":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d","ksc_settings_compatibility::TaskUniqueId":"59e0cc70@xdr_networkisolation_stop@NetworkIsolationStop","responseId":{"type":"long","value":4294967295}}},"TASK_CLASS_ID":0,"TASK_DEL_AFTER_RUN_FLAG":false,"TASK_INFO_PARAMS":{"type":"params","value":{"DisplayName":"Termination of network isolation","klprts-TaskCannotBeDeleted":true,"klprts-TaskScheduleSubtype":256}},"TASK_LAST_EXEC_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASK_LAST_EXEC_TIME_SEC":0,"TASK_MAX_EXEC_TIME":0,"TASK_NAME":"xdr_networkisolation_stop","TASK_PREP_START":0,"TASK_PRIORITY":1,"TASK_START_DELTA":0,"TASK_UNIQUE_ID":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d"}} Copy some value from response and change parameters on the next request with Network isolation exclusions. UpdateTask Modify task settings. ( HostTasks::UpdateTask) POST /api/v1.0/HostTasks.UpdateTask HTTP/1.1 Host: localhost:13299 X-KSC-Session: n18Zfc+1hPeedqD07uM96/A== Content-Type: application/json Content-Length: 32796 { "strTask": "_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d", "strSrvObjId": "A06A16B837CC0E73BD3BCCDAA98A3129", "pData": { "TASKID_COMPONENT_NAME": "Connector", "TASKID_PRODUCT_NAME": "KES", "TASKID_VERSION": "11.0.0.0", "TASKSCH_MS_PERIOD": 0, "TASKSCH_TYPE": 5, #change "TASK_ADDITIONAL_PARAMS": { "type": "params", "value": { "CompatibilityInfo": { "type": "params", "value": { "MinimalPluginVersion": "11.8.0.0" } }, "PRTS_TASK_EXT_SHEDULE_FLAGS": 0, "klprts-TaskStorageId": "_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d", "ksc_settings_compatibility::TaskUniqueId": "59e0cc70@xdr_networkisolation_stop@NetworkIsolationStop", "responseId": { "type": "long", "value": 4294967295 } } }, "TASK_CLASS_ID": 0, "TASK_DEL_AFTER_RUN_FLAG": false, "TASK_INFO_PARAMS": { "type": "params", "value": { "DisplayName": "Termination of network isolation", "klprts-TaskCannotBeDeleted": true, "klprts-TaskScheduleSubtype": 512 #change } }, "TASK_NAME": "xdr_networkisolation_stop", "TASK_PREP_START": 0, "TASK_PRIORITY": 1, "TASK_START_DELTA": 0, "TASK_UNIQUE_ID": "_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d" } } Response Response { } Host unblocked successfully. End Session to KSC (Session::EndSession) Session::EndSession curl --location --request POST 'https://127.0.0.1:13299/api/v1.0/Session.EndSession' --header 'X-KSC-Session: nsPbUpP1oAVZlM1lODEbg8A==' #PxgRetVal from Session.StartSession -
Description and cautions The article is giving some use cases examples of KSC API calls to ease one's start using the API. In that KB we are looking at host isolation with KES/KEA scenario. For the Windows version of cURL, you need to specify that the arguments need to be escaped with "\", otherwise there will be an error. For example: 'Authorization: KSCBasic user=\"YXBpLXVzZXI=\", pass=\"cGFzc3dvcmQ=\", internal=\"1\"' Details Prerequisites internal user: api-user Example KSC address - 127.0.0.1 (the address can also be external) API Port - 13299 (default) User: api-user (intrental KSC user), base64: YXBpLXVzZXI= Password: password, base64: cGFzc3dvcmQ= Credentials: User Password api-user password Base64: YXBpLXVzZXI= cGFzc3dvcmQ= Authentication, type: Authenticated session, other types: KSC Open API description Requests are in cUrl and http formats, as an alternative it is also possible to use Python library (KlAkOAPI Python package) Login Start connection to KSC (Session::StartSession) Session::StartSession curl --location --request POST 'https://127.0.0.1:13299/api/v1.0/Session.StartSession' \ --header 'Authorization: KSCBasic user="YXBpLXVzZXI=", pass="cGFzc3dvcmQ=", internal="1"' Username and password should be encoded to base64 format as part of a secure HTTPS session. For example, https://www.base64encode.org/ can be used for encoding. Response { "PxgRetVal": "nsPbUpP1oAVZlM1lODEbg8A==" } Use this token in request header Find Host Find host by filter string (HostGroup::FindHosts) Filter string, contains a condition over host attributes, see also Search filter syntax. We use "KLHST_WKS_DN" - Host display name HostGroup::FindHosts POST /api/v1.0/HostGroup.FindHosts HTTP/1.1 Host: localhost:13299 X-KSC-Session: nH4iKWCdxuBJWO5U4ATKSew== Content-Type: application/json Content-Length: 170 { "vecFieldsToReturn": [ "KLHST_WKS_HOSTNAME", "KLHST_WKS_DN" ], "lMaxLifeTime": 1200, "wstrFilter": "(KLHST_WKS_DN=\"WIN10-*\")" } Response ID Response {"strAccessor":"ppYeO5rmkvKcMUm8vQzOK2","PxgRetVal":18} Copy Accessor for next request (ChunkAccessor::GetItemsChunk) ChunkAccessor::GetItemsChunk curl -L -X POST "https://127.0.0.1:13299/api/v1.0/ChunkAccessor.GetItemsChunk" -H "X-KSC-Session: noOxgI9Ny7O5Whg/97qvcVg==" -H "Content-Type: application/json" --data-raw "{ \"strAccessor\":\"fb07haDqXIKZbQzyDsMwx1\", \"nStart\": 0, \"nCount\": 100 }" Response info about host: Response { "pChunk": { "KLCSP_ITERATOR_ARRAY": [ { "type": "params", "value": { "KLHST_WKS_DN": "WIN10-OPTIMUM-1", "KLHST_WKS_HOSTNAME": "c0816918-fbc5-4fbc-8fed-6f245756120e" } }, { "type": "params", "value": { "KLHST_WKS_DN": "WIN10-KES-11-OLD", "KLHST_WKS_HOSTNAME": "ab365e11-a1c7-492b-a981-e84402b33a8f" } } ] }, ........ "PxgRetVal": 18 } Copy value "KLHST_WKS_HOSTNAME" for next request KEA Isolation HostGroup.GetHostInfo Acquire specified host attributes. (HostGroup::GetHostInfo) strHostName (wstring) host name, a unique server-generated string (see KLHST_WKS_HOSTNAME attribute). It is NOT the same as computer network name (DNS-, FQDN-, NetBIOS-name) pFields2Return (array) array of names of host attributes to return. See List of host attributes for attribute names HostGroup.GetHostInfo POST /api/v1.0/HostGroup.GetHostInfo HTTP/1.1 Host: localhost:13299 X-KSC-Session: nH4iKWCdxuBJWO5U4ATKSew== Content-Type: application/json Content-Length: 185 { "strHostName":"ab365e11-a1c7-492b-a981-e84402b33a8f", "pFields2Return": [ "KLHST_WKS_HOSTNAME", "KLHST_WKS_DN", "KLHST_APP_INFO" ] } HostGroup.SS_GetNames Get section names from host settings storage. (HostGroup::SS_GetNames) Parameters values should be taken from the previous response. HostGroup::SS_GetNames POST /api/v1.0/HostGroup.SS_GetNames HTTP/1.1 Host: localhost:13299 X-KSC-Session: nqH6Qma75t/wBcQm8vlyqvQ== Content-Type: application/json Content-Length: 148 { "strHostName":"ab365e11-a1c7-492b-a981-e84402b33a8f", "strType":"SS_SETTINGS", "strProduct":"SOYUZ", "strVersion":"4.0.0.0" } Response: Response { "PxgRetVal": [ ".KLNAG_SECTION_REBOOT_REQUEST", "85", "AccountLogonSettings", "ApplicationSettings", "AutoStartEntriesNotifySettings", "ConnectionSettings", "CreateProcessSettings", "FileChangeNotificationSettsEdr", "KLEVP_NF_SECTION", "KsnServiceSettings", "LoadImageSettingsEdr", "MaintenanceSettings", "MdrServiceSettings", "MessageBrokerSettings", "NetworkConnectionSettingsEdr", "NetworkIsolationProfilesSetts", "NetworkIsolationSettings", #copy this field setting "PasswordSettings", "PreventionSettings", "ProductPermissionSettings", "QuarantineSettings", "SandboxSettings", "SelfDefenceSettings", "UserModeApiMonitorSrvSettings", "WMIActivitySettings", "WindowsEventLogSettingsEdr", "WindowsRegistrySettings" ] } With NWC web console KSC create local network exteption for VPN: 1) Open host properties → Applications → KEA 2) Open tab APP Settings → Network Isolation → Isolation on detection 3) Add rule for RDP → click "OK" → click "Save" HostGroup.SS_Read Read data from host settings storage. (HostGroup::SS_Read) Parameters values should be taken from two previous responses HostGroup::SS_Read POST /api/v1.0/HostGroup.SS_Read HTTP/1.1 Host: localhost:13299 X-KSC-Session: nqc+0P0UI+Wzuu+FREB74yQ== Content-Type: application/json Content-Length: 194 { "strHostName":"ab365e11-a1c7-492b-a981-e84402b33a8f", "strType":"SS_SETTINGS", "strProduct":"SOYUZ", "strVersion":"4.0.0.0", "strSection":"NetworkIsolationSettings" } Response info about Network Isolation with RDP rule exception: Response { "PxgRetVal": { "BaseSettings": { "type": "params", "value": { "Revision": { "type": "long", "value": 0 }, "__VersionInfo": [ 1, 0 ] } }, "Enable": false, "Exclusions": [ { "type": "params", "value": { "Description": "Custom (user-defined)", "Name": "Custom (user-defined)", "Rules": [ { "type": "params", "value": { "AppProtocolName": "RDP", "Applications": [], "Direction": 3, "Enable": true, "LocalAddress": "", "LocalPort": { "type": "params", "value": { "MaxPort": 3389, "MinPort": 3389, "__VersionInfo": [ 1, 0 ] } }, "Protocol": 0, "RemoteAddress": "", "RemotePort": { "type": "params", "value": { "MaxPort": 0, "MinPort": 0, "__VersionInfo": [ 1, 0 ] } }, "UseApplications": false, "UseLocalAddress": false, "UseLocalPort": true, "UseProtocol": false, "UseRemoteAddress": false, "UseRemotePort": false, "__VersionInfo": [ 1, 1 ] } } ], "__VersionInfo": [ 1, 0 ] } } ], "IsolationTimeout": 1800, "NotifyUser": true, "UseIsolationTimeout": true, "__VersionInfo": [ 1, 2 ] } } Copy all response for next request. HostGroup.SS_Write Write data to host settings storage for isolation workstation with RDP rule. (HostGroup::SS_Write) 1) Use previous value parameters 2) for nOption use 7 7 - "Clear", replaces existing section contents with pData, i.e. existing section contents will deleted and variables from pData will be written to the section. 3) for pSettings past previous response and change "Enable": true HostGroup::SS_Write POST /api/v1.0/HostGroup.SS_Write HTTP/1.1 Host: localhost:13299 X-KSC-Session: nbpsiiOAAxiDWfMSVkgciWQ== Content-Type: application/json Content-Length: 1066 { "strHostName":"bdcae680-eeaa-4279-a822-92a0d3e01dfb", "strType":"SS_SETTINGS", "strProduct":"SOYUZ", "strVersion":"4.0.0.0", "strSection":"NetworkIsolationSettings", "nOption":7, "pSettings":{ "BaseSettings": { "type": "params", "value": { "Revision": { "type": "long", "value": 0 }, "__VersionInfo": [ 1, 0 ] } }, "Enable": true, #Isolation ON "Exclusions": [ { "type": "params", "value": { "Description": "Custom (user-defined)", "Name": "Custom (user-defined)", "Rules": [ { "type": "params", "value": { "AppProtocolName": "RDP", #custom rule for RDP "Applications": [], "Direction": 3, "Enable": true, "LocalAddress": "", "LocalPort": { "type": "params", "value": { "MaxPort": 3389, "MinPort": 3389, "__VersionInfo": [ 1, 0 ] } }, "Protocol": 0, "RemoteAddress": "", "RemotePort": { "type": "params", "value": { "MaxPort": 0, "MinPort": 0, "__VersionInfo": [ 1, 0 ] } }, "UseApplications": false, "UseLocalAddress": false, "UseLocalPort": true, "UseProtocol": false, "UseRemoteAddress": false, "UseRemotePort": false, "__VersionInfo": [ 1, 1 ] } } ], "__VersionInfo": [ 1, 0 ] } } ], "IsolationTimeout": 1800, "NotifyUser": true, "UseIsolationTimeout": true, "__VersionInfo": [ 1, 2 ] } } Response Response { } Host isolated successfully. For off isolation you must change for pSettings past previous response and change "Enable": false
-
How to renew the KSC certificate correctly [KSC for Windows]
svc_kms posted a blog entry in Kaspersky Security Center's Kaspersky Security Center Community
This article is about Kaspersky Security Center for Windows (KSC for Windows) Problem: KSC certificate renewal or replacement is made incorrectly because the option to instantly replace the server certificate is used. There is an article in Online help dedicated to the klsetsrvcert utility (https://support.kaspersky.com/KSC/13.2/en-US/227838.htm). Sometime people follow the instructions according to the example indicated in the article – "klsetsrvcert -t C -i <inputfile> -p <password> -o NoCA" without thinking about the consequences. This leads to the fact that administration agents (nagents) do not receive a new certificate, and the users have to use the klmover utility. Cause: After the certificate is renewed with "-t C" option, network agents do not receive a new certificate and have no connection to the server. Solution: Run the certificate renewal script using the "-t CR" option (CR — Replace the common reserve certificate for ports 13000 and 13291) and the "-f" option in the <dd.mm.yyyy> format where we indicate the date 3–4 weeks ahead the current one. The time we set aside for changing the certificate to a backup one will allow a new certificate to be distributed to all Kaspersky Network Agents (Nagent): -t <type> Type of certificate to be replaced. Possible values of the <type> parameter: C—Replace the common certificate for ports 13000 and 13291. CR—Replace the common reserve certificate for ports 13000 and 13291. M—Replace the certificate for mobile devices on port 13292. MR—Replace the mobile reserve certificate for port 13292. MCA—Mobile client CA for auto-generated user certificates. -f <time> Schedule for changing the certificate, using the format "DD-MM-YYYY hh:mm" (for ports 13000 and 13291). Use this parameter if you want to replace the common or reserve certificate before it expires. Specify the time when managed devices must synchronize with Administration Server on a new certificate. For example, consider the command "klsetsrvcert.exe -f "DD-MM-YYYY hh:mm" -t CR -g nb.loc". Since this command was used in October, a backup certificate would be created and distributed to all nagents within a month. Thus, the certificate should have been applied on November 1, 2022. Let's check if the backup certificate has applied to the host. To do this, using the klscflag utility, enter the command: klscflag.exe -ssvget -pv 1103/1.0.0.0 -s KLNAG_SECTION_CERTDATA -n KLNAG_SSL_SERVER_CERT_RESERVE -ss '|ss_type = \"SS_LOCAL_MACHINE\";' The certificate has been delivered. If the backup certificate is not yet delivered to the destination host, we will see the following result of this command: Known problem: Problem with Webconsole login - incorrect user or password - see article https://forum.kaspersky.com/blogs/entry/331-ksc-web-console-shows-an-error-after-upgrade-incorrect-user-or-password-ksc-for-windows/ Error - Failed to establish connection with the remote device: This error occurs because we are trying to execute 2 consecutive commands on the same line. The first command is "-t CR -g nb.loc" and the second is "-f '20-12-2023 00:00'". Since the administration server restarts after executing the first command, the second command waits for some timeout before executing. But since in some user configurations, restarting the service can take a long time, the second part is performed when the server has not started yet. Which leads to the above error. In order to fix this behavior, you need to run the commands separately, according to this scenario: Run .\klsetsrvcert.exe -t CR -g nb.loc Wait until the administration server service starts completely (you can check by connecting the console). Run .\klsetsrvcert.exe -f '20-12-2023 00:00'