Search the Community
Showing results for 'Quick Launch Keyboard'.
-
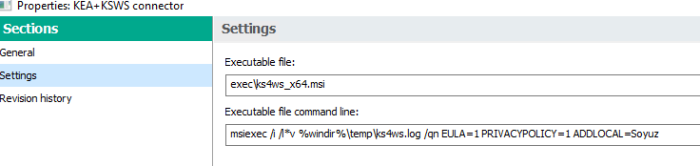
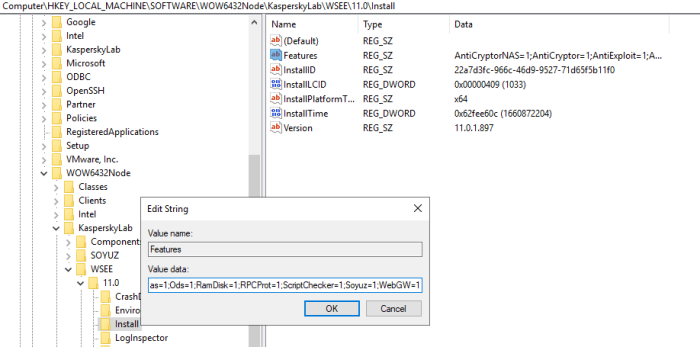
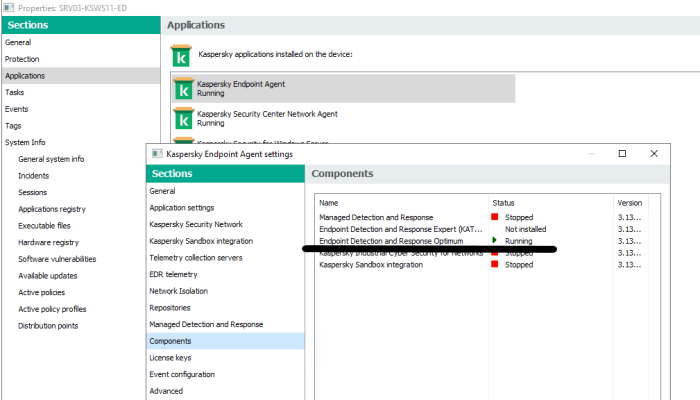
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Using EDR, you may encounter an issue where you're unable to view incident card regarding a detection in KSC Web Console. It looks like this: Here we will discuss known causes of such behavior (several products are involved, so causes may be different). Possible causes and solutions MDR In MDR, incidents are to be viewed using the dedicated MDR Console, and KSC version 13 and newer with configured MDR plug-in. KSC 12.* Web Console will not receive the data; this is expected behavior. KES+KEA If you first install KES without EA component, and then a standalone KEA package, KES EDRO integration will be disabled and killchain will not work. Here is a quick way to determine if KEA was installed as a component of KES. Open regedit, then navigate to: [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\KasperskyLab\protected\KES\Installer\features] "AntiAPTFeature" = "1" If the value is 0, proceed to the workaround to enable the component as described below. To fix this, we ran Change application components task on the host, enabling Endpoint Agent in KES. If KES/KEA integration is configured correctly, we can find the following in KES traces: 12:08:37.426 0x2a18 INF edr_etw Start processing detect = http://www.virusanalyst.com/eicar.zip//eicar/eicar.com, recordId = 6, taskId = 1128, result = 0 12:08:37.426 0x2a18 INF edr_etw Start processing actions = http://www.virusanalyst.com/eicar.zip//eicar/eicar.com, action = 4, recordId = 6, taskId = 1128, edrAction = 3489660999, result = 0 12:08:37.442 0x2a18 INF edr_etw Killchain is enabled! 12:08:37.442 0x2a18 INF edr_etw SystemWatcher is running! 12:08:37.442 0x2a18 INF edr_etw product::component::edr::`anonymous-namespace'::IsSystemWatcherDetect begin 12:08:37.442 0x2a18 INF edr_etw product::component::edr::`anonymous-namespace'::IsSystemWatcherDetect end 12:08:37.442 0x2a18 INF edr_etw product::component::edr::`anonymous-namespace'::InvestigateProcessIds begin 12:08:37.442 0x2a18 INF edr_etw product::component::edr::`anonymous-namespace'::InvestigateProcessIds end 12:08:37.442 0x2a18 INF edr_etw Finish processing detect = http://www.virusanalyst.com/eicar.zip//eicar/eicar.com threat status = 1, recordId = 6, taskId = 1128,result = 0 12:08:37.458 0x1f18 INF edr_etw Finish processing AV detect result = 0 Searching for ThreatID in KEA traces: 12:08:37.426 0x2a18 INF amfcd ThreatsProcessingEventsLogic::OnTreatActionImpl: ctx:0x23d68510 [TI 0x1b8dd490: id = 0x6, : tdid = {7F620459-6C51-9E46-9A5D-689A9B0D0098}, name = http://www.virusanalyst.com/eicar.zip//eicar/eicar.com, add info: <none>, 0x0] 0x4 0x0 KES+KEA (upgrade from KESB to EDR Optimum) EDR Optimum requires KSC 12.1 or newer to work. This includes the Network Agent, which is a part of KSC, and is generally installed on the host alongside KES. Using an outdated version of Network Agent (10.5, 11, etc.) will lead to the mentioned error when opening incident cards. If Network Agents were not upgraded along KSC, it's better upgrading them for EDR Optimum. KES 11.7+ Check that EDR Optimum feature is enabled in registry (GSI > Registry > HKLM_Software_Wow6432Node_KasperskyLab.reg.txt ). [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\KasperskyLab\protected\KES\Installer\features] EdrOptimumFeature = 1 If value is 0, run Change application components task on the host, enabling EDR Optimum in KES. Also in traces (*.SRV.log) you can search for sentence bundles::InstalledFeaturesProvider::InstalledFeaturesProvider and check that EDROptimumFeature is there, for instance in example below such component is missing KES.21.9.6.465_05.18_14.00_3952.SRV.log 11:00:36.897 0x26a0 INF bundles::InstalledFeaturesProvider::InstalledFeaturesProvider{ 3 (AVScannerAndCoreFeature) 28 (AdaptiveAnomaliesControlFeature) 0 (AdminKitConnectorFeature) 24 (AdvancedThreatProtectionFeature) 27 (AmsiFeature) 7 (ApplicationControlFeature) 17 (BehaviorDetectionFeature) 30 (CloudControlFeature) 4 (CriticalScanTask) 6 (DeviceControlFeature) 23 (EssentialThreatProtectionFeature) 11 (ExploitPreventionFeature) 8 (FileThreatProtectionFeature) 19 (FirewallFeature) 5 (FullScanTask) 2 (HostIntrusionPreventionFeature) 16 (MailThreatProtectionFeature) 14 (NetworkThreatProtectionFeature) 12 (RemediationEngineFeature) 25 (SecurityControlsFeature) 18 (UpdaterTask) 21 (WebControlFeature) 20 (WebThreatProtectionFeature) 22 (WholeProductFeature) } KSWS+KEA The same rule applies: KEA component needs to be installed in KSWS. KSWS does not have a "Change application components" task in KSC, so this has to be taken into account during KSWS deployment. Here is a quick way to determine if KEA was installed as a component of KSWS. Open regedit, then navigate to: [HKEY_LOCAL_MACHINE\Software\Wow6432Node\KasperskyLab\\WSEE\11.0\Install] "Features"="AntiCryptorNAS=0;AntiCryptor=0;AntiExploit=0;AppCtrl=0;AVProtection=0;DevCtrl=0;Fim=0;Firewall=0;ICAPProt=0;IDS=0;Ksn=0;LogInspector=0;Oas=0;Ods=0;RamDisk=0;RPCProt=0;ScriptChecker=0;Soyuz=0;WebGW=0" (Soyuz needs to be set to 1) If Soyuz is set to 0, apply workaround to enable it. KSWS allows to change its components locally or via cli. Here is the example of how to set Soyuz=1 when KEA was installed not as a component of KSWS: 1. Locate ks4ws_x64.msi or ks4ws.msi (depends on OS architecture) 2. Create custom installation package based on ks4ws_x64.msi or ks4ws.msi from p.1 with parameters as per screenshot (add UNLOCK_PASSWORD= if KSWS is protected by password in policy) 3. Deploy package on problematic servers with KSWS and KEA, then check registry that Soyuz=1 4. Check host's properties at KSC side - EDRO should be in Running state in KEA If KSWS/KEA integration is configured correctly, we can find the following in KSWS traces: 19:57:04.577 7a8 1310 info [edr] Published ThreadDetected: VerdictName : HEUR:Win32.Generic.Suspicious.Access RecordId : 0 DatabaseTime : 18446744073709551615 ThreatId : {ffb58079-6d8d-4a62-8ab0-021ff4ed61c5} IsSilent : false Technology : 3489661023 ProcessingMode : 3489660948 ObjectType : 3489660934 ObjectName : C:\Windows\System32\wbem\WmiPrvSE.exe Md5 : e1bce838cd2695999ab34215bf94b501 Sha256 : 1d7b11c9deddad4f77e5b7f01dddda04f3747e512e0aa23d39e4226854d26ca2 UniquepProcessId: 0xf7c807730e051a0d NativePid : 3360 CommandLine : AmsiScanType : AmsiScanBlob : FileCreationTime: 1601-01-06T23:09:56.075520800Z Searching for ThreatID in KEA traces: 19:57:05.583 704 9b0 debug [bl] ThreatsHandler: detect v2 verdictName: HEUR:Win32.Generic.Suspicious.Access detectTechnology: 0xd000005f processingMode: 0xd0000014 objectType: 0xd0000006 objectName: C:\Windows\System32\wbem\WmiPrvSE.exe nativePid: 3360 uniquePid: 17854528913448180237 nativePidTelemetry: 3360 uniquePidTelemetry: 17854528913448180237 downloaderUniqueFileId: <none> downloadUrl: <none> isSilentDetect: false threatId: ffb58079-6d8d-4a62-8ab0-021ff4ed61c5 19:57:05.583 704 650 info [evtstt] NetworkConnectionHandler statistics: queueSize=0, received=59675, processed=59675, dropped=0, queueBytes=191 19:57:05.583 704 650 info [evtstt] NetworkConnectionHandler statistics: queueSize=0, received=59676, processed=59676, dropped=0, queueBytes=132 19:57:05.583 704 650 info [evtstt] NetworkConnectionHandler statistics: queueSize=0, received=59677, processed=59677, dropped=0, queueBytes=371 19:57:05.583 704 9b0 debug [bl] Threats Handler: event processed, id = 2 19:57:05.584 704 1fc debug [killchain] Message discarded: name = ThreatDetect The verdict is Message discarded, this means the detection won't trigger killchain generation. No such entries can be found in traces, which might mean that EPP integration is not configured correctly (EDR component is disabled in KSWS). Check killchain presence on the host If all pre-requisites are met, it's worth checking if killchain files are actually created on the host. To check that, run cmd.exe as Administrator and check the c:\ProgramData\Kaspersky Lab\Endpoint Agent\4.0\Data\killchain\detects folder contents. Archives with <threat_id>.zip names should be present in the folder: C:\WINDOWS\system32>dir "c:\ProgramData\Kaspersky Lab\Endpoint Agent\4.0\Data\killchain\detects" Volume in drive C has no label. Volume Serial Number is 8010-ADC0 Directory of c:\ProgramData\Kaspersky Lab\Endpoint Agent\4.0\Data\killchain\detects 08/16/2021 12:20 PM <DIR> . 08/16/2021 12:20 PM <DIR> .. 08/16/2021 09:34 AM 636 0349c190-4ac3-4da4-9b64-07835298660f.zip //this is an archive with killchain info 08/16/2021 12:18 PM 696 1d306aa7-f37f-4ab2-969e-d337d398a995.zip 08/16/2021 09:34 AM 637 23a5dc93-5776-43c8-b949-79c102aa1184.zip 08/16/2021 12:19 PM 691 27bc9ea3-200b-49d2-b8b0-df7954cd428a.zip 08/16/2021 12:19 PM 683 40673c70-9e8e-420f-b5ce-65b406862b94.zip 08/16/2021 12:19 PM 688 590b6e30-4509-4b25-bdb0-062f89b7e062.zip 08/16/2021 12:20 PM 693 67993612-dc82-45a2-9e5b-74756adc46eb.zip 08/16/2021 12:20 PM 685 6a892bd1-f452-42d0-80b0-cb953cd7fc26.zip 08/16/2021 12:19 PM 686 a63fbafa-fcef-46f7-935f-42be4392a172.zip 08/16/2021 12:19 PM 699 d9d4f5eb-42b2-4460-8f8a-eb63bbef8791.zip 08/16/2021 12:19 PM 686 f6042624-9840-4a6e-9b30-9270cce22236.zip 11 File(s) 7,480 bytes 2 Dir(s) 240,763,092,992 bytes free
-
Merhabalar, age of empires 4 oyununu Steam dan satın alıp indirdim. Fakat oyun başlangıçta yükleme ekranında kalıyor ve ileri gitmiyor . Fakat Windows+ r den Kaspersky nin hizmetlerini kapatınca serverı aramaya başliyor . Nasıl son verebilirim Windows 11 CoreSinglelanguage x64 Kaspersky plus üyelik Sürüm : 21.14.5.462
-
Even I'm facing the same issue. I've kept the same Edge settings as you, I have removed all extensions from Edge. I've run a quick scan and a full scan and nothing has been detected so far. (I did have a virus attack a while ago, but I think I've removed all traces of it with Kaspersky; the new scans show no traces of any virus. I've no idea what to do now. Even the temporary solution of blocking all cookies does not seem to work for me because every time I open Edge I get this same notification and the file is subsequently deleted but I'm confused about what to do. I only use Edge on one PC so it is not sycned anywhere else. Edge version: 118.0.2088.76 OS: Windows 10, Version 22H2, OS Build 19045.3570 Kaspersky version: 21.14.5.462 Do you have any suggestions about the same?@harlan4096 Thanking you in advance.
-
Hello everyone, how are you? Good morning, good afternoon and good night. Look how interesting, I played Grand Theft Auto Multi Theft Auto: San Andreas and surprisingly, the administrator of the server I played on has bad intentions, I had a fight with him. It turned out that my computer and router connected to his server, and I believe he managed to steal my password through that. But look. How did I get attacked after formatting the HD and rewriting it in the BIOS? And rewritten the router Firmware? How is this possible? It happened that I did the formatting and cleaning process (disinfection) and it didn't solve the problem, I entered my Microsoft account (Outlook), I clicked on enter, I was redirected to a fake Microsoft page and I entered the email and password and then was redirected to the original page. HOW IS THIS POSSIBLE? Could the MASTERS help me? It looks like a movie, my Facebook was stolen. Even formatting, how is this possible? Any theories? I contacted Intel and MICROSOFT, luckily my PC parts are under warranty and from what I understand it would only be resolved with reverse engineering, because even formatting and connecting to another network with another IP, my hardware's firmware remains the same and doesn't work. This is a common virus, but a complex one and hackers. They stole my CPF, to commit CRIMES, this happened in Brazil, the country of organized CRIME. Kaspersky urgently needs to create antivirus that detects hardware malware, such as video cards, memory, USB devices, keyboard and mouse and to top it off processors, is it easy? kaspersky needs to invest in technology that detects this incident, especially in the case of espionage to steal personal data as was my case. Could anyone show me some technology or something to try to save some computers? And HDs, or is this a case of throwing the PC in the trash and buying a new one?
-
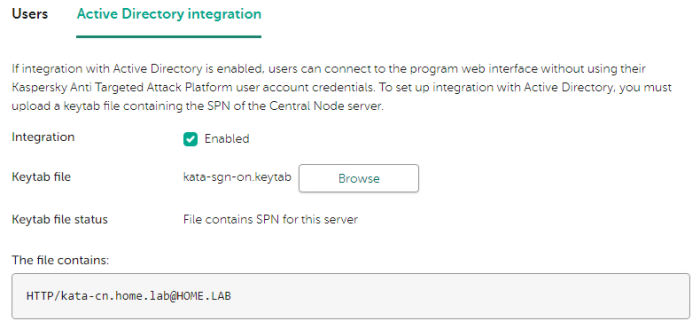
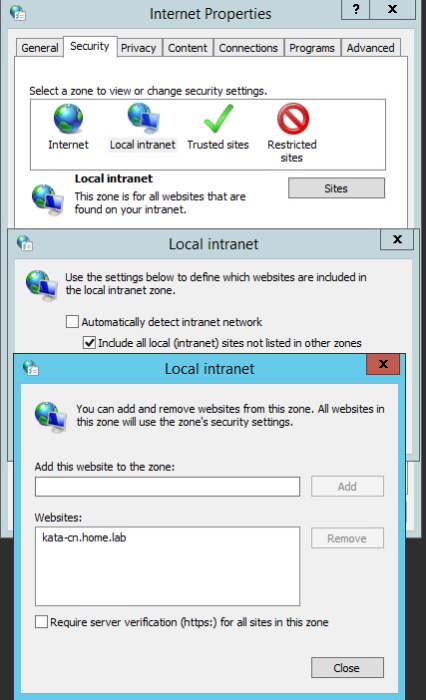
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. There is an example of a step-by-step instruction to configure Single-Sign-On (SSO) for KATA 4.1/5.0 into HOME.LAB domain. Prerequisites Deployed Central Node Server Name should be FQDN. (In current case FQDN name of Central Node - kata-cn.home.lab) It can be checked via Settings/Network Settings of Central Node. A and PTR record should be set for Central Node in DNS. Domain User Account should be created to set up Kerberos authentication by means of keytab file (in current case Domain User Account is kata-sign-on). AES256-SHA1 encryption algorithm should be enabled into created Domain User Account. Step-by-step guide to create keytab file On Domain Controller: Launch CMD As Administrator Execute the following command to create keytab file C:\Windows\system32\ktpass.exe -princ HTTP/kata-cn.home.lab@HOME.LAB -mapuser kata-sing-on@HOME.LAB -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass * +dumpsalt -out C:\TEMP\kata-sgn-on.keytab The utility requests the kata-sign-on user password when executing the command. The SPN of the selected server is added to the created keytab file. The generated salt is displayed on the screen: Hashing password with salt "<hash value>" For multiple Central Node servers you need to save "<hash value>" of hashing password to add an SPN for each subsequent Central Node servers further using ktpass.exe utility. On Central Node Web Interface Move to Settings/Users/Active Directory Integration Add the created keytab file: Keytab file status section contains File which contains SPN for this server The file contains section HTTP/*****@*****.tld Under Users tab click Add and select Domain user account. Set domain user as <username>@<domain> On client machine Host should be joined to the same domain. Domain user should be logged in with account added into the Central Node. Open Control Panel/Internet Options Click on Security and select Local Intranet Click on Sites and then on Advanced Add FQDN of central node - kata-cn.home.lab Close windows: Launch Web Browser and access to Web Interface of the Central Node https://kata-cn.home.lab:8443 and it should be opened without asking any Login/Password.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This instruction is relevant only in case of troubleshooting incorrect loading or rendering of a web page. In order to troubleshoot issues KES network traffic related issues traffic dump is required. It is easier to analyze and does not require third-party software installation. If reproduction of the issue requires the web browser to open web pages(such as web control non-working as expected, web page not loading, and so on), the tests should be performed in Incognito mode(also known as private browsing). Chrome browser: Ctrl+Shift+N or you can start browser from terminal: & "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" -incognito . Starting application from terminal will make launch key visible in traces and make diagnostic easier. Firefox browser: Ctrl+Shift+P or you can start browser from terminal: & "C:\Program Files\Mozilla Firefox\firefox.exe" -private-window . Starting application from terminal will make launch key visible in traces and make diagnostic easier. Microsoft Edge: Ctrl+Shift+P Opera browser: Ctrl+Shift+N KES11 Instructions Disable KES11 Self-defense Navigate to the following registry key: x86: HKLM\SOFTWARE\KasperskyLab\protected\KES\environment\ x64: HKLM\SOFTWARE\Wow6432Node\KasperskyLab\protected\KES\environment\ Create a string type value named DumpNetworkTraffic : DumpNetworkTraffic = (REG_SZ)"1" Restart the product or reboot the host Traffic dump files will be saved to %ProgramData%\Kaspersky Lab\KES\Data\traffic Once the issue is reproduced compress the whole traffic directory Do not forget to disable traffic dump collection. To do so delete DumpNetworkTraffic value.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. The article is giving a working configuration instructions for domain authentication by using NTLM and Kerberos protocols. NOTE: Domain authentication in OpenAPI over Kerberos protocol has the following restrictions: Administration Server address must be specified exactly as the address for which the Service Principal Name (SPN) is registered for domain account name. In the domain, you need to set the Service Principal Name (SPN) to publish the OpenAPI service on port 13299 for the machine with the Administration Server, the service of which is running under the name of the domain user <domain-user>. Kaspersky Security Center 13 Web Console user must be authenticated in Active Directory by using Kerberos protocol. Kerberos authentication should be allowed in web-browser. For details, refer to documentation of used web-browser. Details SPN - Service Principal Name Log in Domain Controller as Domain administrator. Open powershell as admin and run the following commands: Powershell setspn.exe -A HTTP/hostname-node-1.domain.local -u domain\user-ksc-service setspn.exe -A HTTP/hostname-node-2.domain.local -u domain\user-ksc-service Example setspn.exe -A HTTP/kscw-node-1.sales.lab -u sales\ksc setspn.exe -A HTTP/kscw-node-2.sales.lab -u sales\ksc setspn.exe -L -u sales\ksc #command for check spn records #Response Registered ServicePrincipalNames for CN=KSC Service,CN=Users,DC=sales,DC=lab: HTTP/kscw-node-1.sales.lab HTTP/kscw-node-2.sales.lab Enable Kerberos/NTLM authentication in web browsers Microsoft Edge \ Internet Explorer win + r => inetcpl.cpl Activate the Security tab. Select Local intranet and click Sites. In the opened dialog box click Advanced. Add the host name of Adaxes Web interface (e.g. host.company.com). Click Close and then click OK. Click Custom level. Navigate to Scripting and enable Active scripting. Navigate to User Authentication \ Logon. Select Automatic logon only in Intranet zone and click OK. Activate the Advanced tab. In the Settings list, navigate to the Security section. Select Enable Integrated Windows Authentication and click OK. Mozilla Firefox - https://developer.mozilla.org/en-US/docs/Mozilla/Integrated_authentication Launch Mozilla Firefox In the URL window, enter about:config and press Enter. In the filter text box, enter network.negotiate. Double-click the network.negotiate-auth.trusted-uris option and enter the host name of Adaxes Web interface (e.g. host.company.com). Repeat previous step for the network.negotiate-auth.delegation-uris option. Google Chrome Add the Software\Policies\Google\Chrome\AuthServerWhitelist key equal to *.<domain-name>.local to the registry Add the Software\Policies\Google\Chrome\AuthNegotiateDelegateWhitelist key equal to *.<domain-name>.local to the registry
-
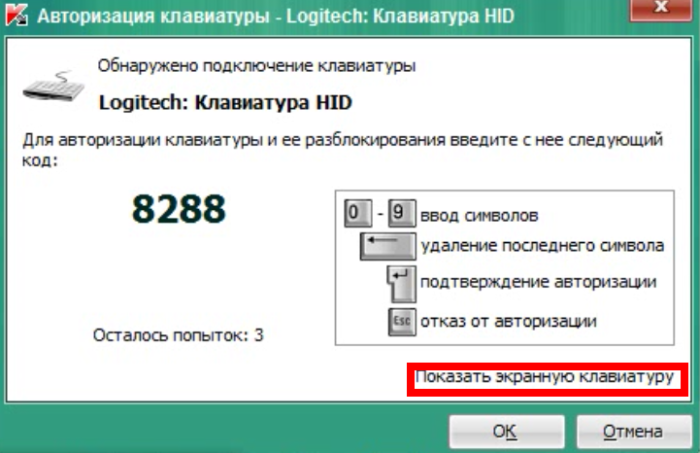
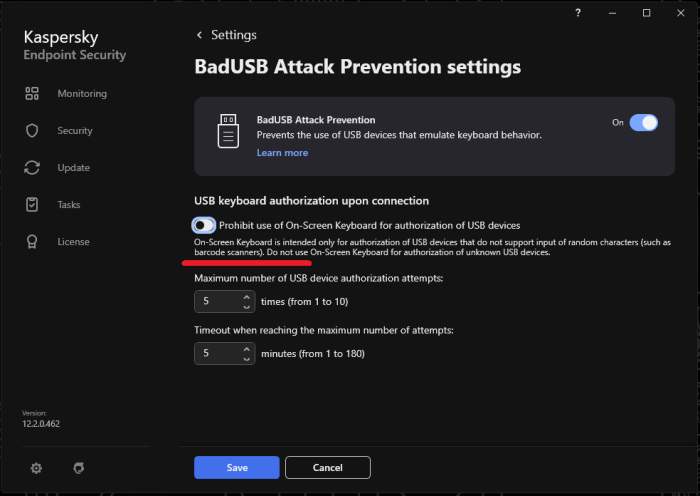
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Some devices do not have keyboards, but still are detected with BadUSB. Step-by-step guide In order to allow them work properly use BadUSB on-screen keyboard, using other onscreen keyboards or physical ones is not recommended. To open BadUSB on-screen keyboard click on the highlighted text (example for Russian localization). Note that Prohibit use of On-Screen Keyboard for authorization of USB devices option should be turned off.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Description, Symptoms & Impact The installation of the Network Agent isn't possible on a device because of the error System error 0x1F (A device attached to the system is not functioning.) Diagnostics In the MSI Log and Application Eventlog can be found the following line: (1192/0x0 ("System container 'LOC-PUB-6EEB50F8D2EB46029DB4CCB77E0DA651' is corrupt") Workaround & Solution The issue comes from a corrupt cryptostorage in the OS. It's not a KL related issue, although there is a possible solution to fix it. On the problem host launch cmd.exe with administrative privileges Run klcryptstgclean.exe: klcryptstgclean -tl 4 -tf $klcryptstgclean_trace.txt -l klcryptstgclean.log Try to install NAgent. If it doesn't help, perform actions from the Cryptostorage-1.docx file. If installation fails again, send to Kaspersky Support the following files: "$klcryptstgclean_trace.txt", "klcryptstgclean.log", new GSI with klnagent installation logs. It is not KSC and klnagent related issue. It is OS related issue. If workaround doesn't help, try sfc /scannow command, OS restore, OS reinstallation or contact MS support.
-

I want a strictly black design
Guest replied to a topic in Kaspersky: Basic, Standard, Plus, Premium
here is the correspondence..... Hi There, I am Tiviya your support representative for today's chat. How may I assist you today? 😊 Operator 22.10.2023 12:16 hello please make a strictly black design for kaspersky standard 21.14.5.462 the same as the kaspersky endpoint security It should be completely black You 22.10.2023 12:16 Download You 22.10.2023 12:17 Here is the reference number for your chat today: INC000015817627 Please give me 2-3 min to bring up your details. Operator 22.10.2023 12:17 ok You 22.10.2023 12:17 Thank you for waiting Operator 22.10.2023 12:18 Open Kaspersky Standard > go to settings > interface settings > design theme > Choose Dark Operator 22.10.2023 12:18 I know this, I need the left side to be black too.... You 22.10.2023 12:20 Show me this on a screenshot please Operator 22.10.2023 12:20 Download You 22.10.2023 12:22 Sorry this is a default theme. It cannot be completely black as the other application. Is there anything else I can help with before we end the chat? Operator 22.10.2023 12:24 no, thank you very much(( You 22.10.2023 12:25 You 22.10.2023 12:25 This your chat reference number: INC000015817627 If that is all for now, I will end this chat here and I would appreciate it if you could complete a quick survey about the support that I have provided. 😊 Thank you for contacting Kaspersky and have a nice day. 😉 Operator 22.10.2023 12:25 The conversation has been completed. Please feel free to continue it anytime. Operator 22.10.2023 12:25 -
Hi. Don't work for me. I leave to copy and used CTRL+ENTER to fill a field or simultate copy&paste a password. Its only works. I opened a INC000015793435, but the solutions and, this is funny: they asked me for the debug report to look for the problem, when they know IT EXISTS. Hi. I was send a report, but the only solution that found is In the window of password (ctrl+alt+A, example). INTRO to copy&paste the user CTRL+INTRO copy&paste the password. Is a way to keep the problem until Kaspersky launch a new version fixed. 🙂
-
2 Preguntas sobre escaneo de sistema completo con KIS
tcwe replied to tcwe's topic in Para usuarios particulares
Muchísimas gracias, Harlan! OK, ya le hice los cambios indicados al Quick Scan. 👍 Muchas gracias! y también por los consejos de tipos de SSD. 100% de acuerdo. Lo raro es que ya tenía todo al máximo cuando sólo duraba 2 horas; no le he cambiando nada que aumente el tiempo. Esta versión 21.15... ¿esta numeración es sólo para la nueva suite de productos o por qué será que mi KIS se quedó en 21.3 y no se me actualizó a la 21.14 por sí sola, si antes se actualizaba sin yo tener que descargar nada? Es que no me queda claro: ¿la sugerencia es que me pase a Kaspersky Standard v.21.15, o hay una *KIS* 21.15? -

2 Preguntas sobre escaneo de sistema completo con KIS
harlan4096 replied to tcwe's topic in Para usuarios particulares
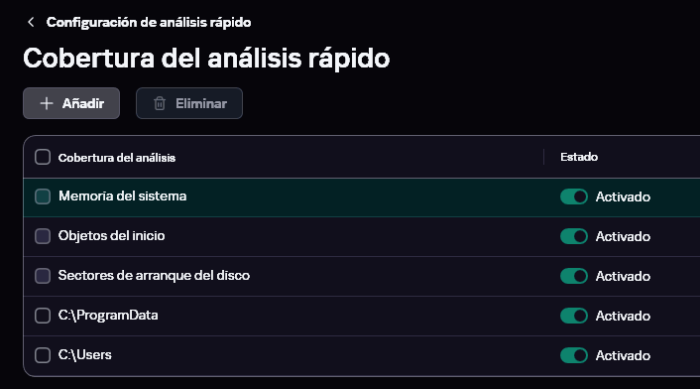
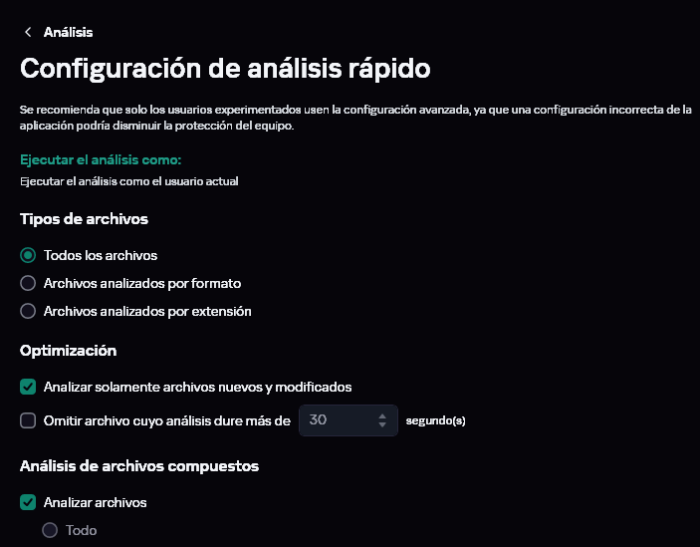
Bienvenid@ a la Comunidad de Kaspersky. Lo ideal sería obviamente hacer el análisis cuanto antes mejor. Aunque yo no hago nunca Full Scans... creo que ya lo he comentado otras veces en la Comunidad. Personalmente, pienso que son una pérdida de tiempo innecesaria y están sobrevalorados 😁. En su lugar, corro Quick Scans modificados, añadiéndole 2 carpetas a la Cobertura del análisis: También modifico un poco las opciones en su Configuración Avanzada: En los Full Scans, activar esta opción es fundamental para optimizar el tiempo de análisis: Configurar un Análisis Completo con todo al máximo, es una apuesta segura a que durará horas... Otra opción para agilizar los análisis completos del sistema es disponer de una unidad de tipo SSD, y si el sistema lo permite, pues mejor del tipo M2 de las nuevas generaciones 3/4. Para terminar tienes KIS 21.3, la versión 21.15 está ya calentita a punto de salir (¡estad atentos que pronto publicaremos los enlaces de descarga en esta sección!). Como tienes KIS, al migrar tu licencia se convertirá en Kaspersky Estándar. Saludos. -
When I try to open the Valorant game I get a message saying "Cannot guarantee authenticity of the domain to which an encrypted connection is being established", and even if I click continue the game does not open, and not only that, but from then on the game never opens unless I restart the computer and I get the message again. SSL connection with invalid certificate detected;Riot Client;RiotClientServices.exe;
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. RDP connection invoked via KSC console uses hostname to connect to a host - mstsc.exe is invoked with /v hostname parameter. Edit command line used to invoke mstsc.exe with ip address parameter instead of the hostname: Open Custom tools → Configure custom tools Select Remote Desktop, click Modify Edit Command line text box, it should contain <host_ip> instead of <A>: /v:<host_ip>:<P> /f Disable Create tunnel for TCP port specified below checkbox Administration Console will now launch mstsc.exe with ip address as argument.
-

language change in KTS
Flood and Flood's wife replied to ukaszw80's topic in Kaspersky Total Security
Hello @ukaszw80, Thank you for posting back & the information! You can't *make* the software English without installing a English language version, the shift+f12 is just a quick workaround, not sustainable. Uninstall the existing version, then download & install: Kaspersky Total Security for Windows® - from Kaspersky's Global website, select Global OR The European Union (if that suits your needs). IF that does not work, (your) best course of action is to contact Kaspersky Customer Service - select Email or Chat & fill in the template as in our image at the end of our reply. Because the license is from Ebay & there may be an issue - it's possible Kaspersky Customer Service may not be able to assist *but* all you can do is ask. Contact the Ebay merchant - find out why the product is not functioning in the manner you expect? 💥Just as information, the *repeated* advice provided here in the Community is: do not buy Kaspersky software from Ebay - some unscrupulous merchants sell Kaspersky licenses multiple times, knowing the license is limited or has other problems, they really don't care - they get their sale - if it turns out you've been sold a dud license - report the merchant to Ebay💥 Please share the outcome with the Community, when it's available? Thank you🙏 Flood🐳+🐋 -
Settings and Storage Buttons Grayed Out
v4u6h4n replied to v4u6h4n's topic in Kaspersky Endpoint Security for Business
Hey Demiad, thanks for your help with that :-) Can I launch the GUI from CLI using sudo? -
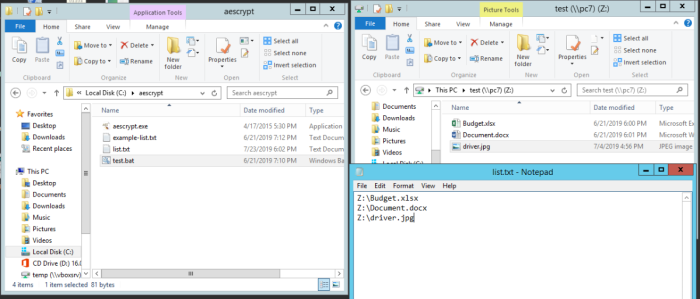
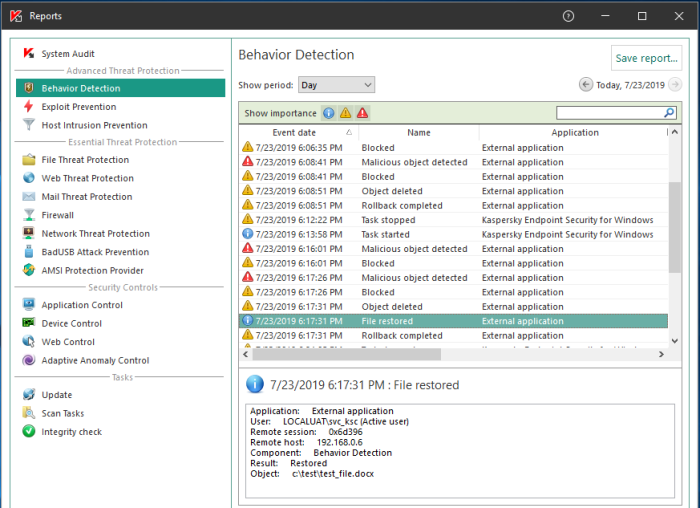
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This article is about Kaspersky Endpoint Security for Windows (KES for Windows) aescrypt.zip and TestProgExp.zip can be found here. Remote encryption test This test requires two participating workstations: an Attacker PC and a Victim PC. Behavior Detection component has to be configured on a Victim PC to detect malware activity, protect shared folders and block connections on detection of external encryption. Step-by-step guide On a Victim PC create folder with regular office-like files: *.DOC, *.DOCX, *.XLX, *.JPG Share folder on the Victim PC, ensure that the account logged on to the Attacker PC has full access to the shared folder. Map the shared folder as a network drive on the Attacker PC. Add/unpack the aescrypt.zip archive to the Attacker PC. Add contents to the list.txt file, based on the files in a mapped folder. Since the folder is mapped, paths will look like local ones, eg. Z:\Book1.xlsx. Use the contents of file example-list.txt as an example: On an Attacker PC, launch test.bat file to start encrypting files from list.txt . Behavior Detection in KES on the Victim PC will detect the attempt and will try to perform a rollback. Full access to a share on Victim PC for an Attacker PC will be blocked (if specified in KES policy). File restoring event is logged on a protected workstation Access to a folder is blocked from an attacker's point of view Local encryption test Step-by-step guide Prepare a folder with files to get encrypted, perform tests on files *.DOC, *.DOCX, *.XLX, *.JPG. Add/unpack to this folder the attached TestProgExp.zip utility. Launch TestProgExp utility to start the encryption. Files will be encrypted in a folder with test utility Allow some time for Behavior Detection in KES to detect the attempt and perform the rollback, as well as get rid of the suspicious software: Files get restored
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This article is about Kaspersky Endpoint Security for Windows (KES for Windows) Description FDE precheck is a utility used for advanced Full Disk Encryption compatibility testing. It contains latest drivers which will be implemented in future KES releases. FDE precheck also collects diagnostic data used to fix compatibility issues. Inability to use laptop keyboard and\or touch-pad is one of the most frequently met issues. Using FDE precheck you can understand if compatibility issue was already fixed and will be included in next release or it should be addressed. You can download latest FDE precheck utility using following links: For KES 11 - https://support.kaspersky.com/14328 System requirements Single operating system should be installed on the test machine, FDE Precheck can't properly function on a host with multiple operating systems. Use administrative account to run the utility. Read before proceeding Decrypt the test host and remove Kaspersky Endpoint Security and AES module. Do a backup of the critical data on the test machine. Follow the test sequence exactly as stated below. Do not manually stop the execution of the utility. The system will automatically restart several times, it is an expected behavior. Plug in laptop. Do not run test on battery. Failure to comply with steps above may lead to unpredictable consequences. Test sequence Make sure machine decrypted does not have KES or AES module installed not running any KL drivers has no critical data plugged in Reboot. Copy and unpack fde_precheck.zip archive. Run elevated fde_precheck.exe (either by right-clicking and choosing Run as administrator or by starting it from an elevated command prompt). If the program will not find any incompatibilities the following message box will appear: Press Yes, to initiate installation of the encryption drivers and initiation of the test. Wait for the automatic reboot, then login using the administrative user as was done earlier. Press OK on the pop-up that will appear shortly after the reboot: Press Yes in the UAC window if it will appear shortly after. Wait for several minutes (up to 10-15 minutes) until next automatic reboot will occur. Do not initiate reboot manually! It will be done automatically. Manual reboot at this stage may result in corruption of the OS. All preparations are run in background, it is normal that there will be no indication of activity on the desktop. After automatic reboot you will see the preboot agent, and it will require human presence to complete those tests. If possible, record the whole process on a camera of smartphone. You will be asked to enter random keystrokes using the keyboard and mouse. In case of successful keystroke registration you will see something like that: Just follow the instructions that will appear on the screen and press "NEXT >" when done with each test. In case FDE Precheck Preboot agent will fail booting or will freeze at some point, please take photo of the error message, or record the whole process on a camera and reboot the machine if necessary. OS will boot either way. Login using the administrative account that was used earlier. At this point drivers will be removed in the background and host will be rebooted one last time automatically. Wait for several minutes (up to 10-15 minutes) until next automatic reboot will occur. Do not initiate reboot manually! It will be done automatically. Manual reboot at this stage may result in corruption of the OS. All preparations are run in background, it is normal that there will be no indication of activity on desktop. The following three files are always created. All three files are mandatory to provide for analysis. fde_precheck_report.txt fde_precheck.log (will be located in the folder with fde_precheck.exe) Description of what have happened during tests (with screenshots and video if possible).
-
I recentlly discovered that Microsoft OneDrive, Phone Link, Microsoft Store and Windows Update had stopped working, all claiming I was not connected to the internet. This wasn't true, as my browsers were still working. I contacted Microsoft Support who found that their Quick Assist app couldn't connect. Microsoft suggested a clean boot, and when I did this with Kaspersky Total Security V 21.3.10.391 running the problems persisted. After pausing the Kaspersky protection, all the Microsoft apps worked correctly. Searching through the Kaspersky Forum I found this thread which provided a fix by Friend https://forum.kaspersky.com/topic/ms-teams-only-works-when-i-disable-my-kaspersky-35859/ This fix solved the immediate problems, and all the Microsoft apps worked correctly with Kaspersky protection running. Reading further in the thread I found that I should have installed Kaspersky Plus to replace my Kaspersky Total Security. I have done that, and everything is working.
-
I have Kaspersky Premium. "Previous application launch failed". Apparently after few minutes when Windows boots, Kaspersky crashes and opens up again and displays this error. And it does the same several times again during the day. It's really annoying. I have contacted customer support and gave them all the necessary files (dump and system info files), It's been 3 weeks and I haven't heard anything back. I went so far as to fresh install the latest Windows 11 (ISO on Microsoft's website), but nothing changes. I do not have any cracked software and everything I installed are genuine and properly bought. I thought the issue may be due to system stability, so I did a memory test overnight and did some burn-in benchmarks and there are no errors. No other program on my system acts weirdly. I have also tried "Kaspersky removal tool" and did another installation of Kaspersky, but the issue persists. I am very close to uninstalling this for good, and I don't want to, I really like Kaspersky. Please help!
-
KSK causing Google Classroom to refresh constantly
Ragman replied to TheMK's topic in Kaspersky Safe Kids
Adding the affected domain as trusted in web protection is a quick fix if you want to give a try. -
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Description and cautions This article describes how to configure dump for capturing memory dumps, including application memory. To create a memory dump of a virtual machine: HOWTO: Get a memory dump of a virtual machine from its hypervisor. Details The recommended text editor is nano, below is a quick tutorial on how to use it if you are using it for the first time. Quick description of nano's basic functions Configure kdump Altlinux There is no kdump-tools package in the default repository, so it has to be downloaded from the sisyphus repository: Go to https://packages.altlinux.org/en/sisyphus/srpms/kdump-tools/ In List of rpms provided by this srpm select the kdump-tools package for the required architecture (can be checked by running uname -m) Download the package from the Download link Install it by running apt-get update && apt-get install <path to the downloaded rpm> After that, follow the Debian instruction from Edit /etc/default/kdump-tools step Red Hat based distributions (tested on Fedora 38, Rocky Linux 9, Red OS) Install kexec-tools sudo dnf install kexec-tools Edit /etc/kdump.conf. In the configuration file edit the core_collector setting: option -d should be set to 17 instead of 31 Edit /etc/default/grub. Edit GRUB_CMDLINE_LINUX, add crashkernel=256M to reserve enough RAM for the dump kernel to run, and nmi_watchdog=1, to capture a dump in case of a system hang Run sudo grub2-mkconfig -o /boot/grub2/grub.cfg Reboot Enable kdump service sudo systemctl enable --now kdump.service Debian based distributions (tested on Debian, Astra CE, Alt Linux) Install kdump-tools sudo apt update && sudo apt install kdump-tools -y Edit /etc/default/kdump-tools. In the configuration file edit the MAKEDUMP_ARGS variable: option -d should be set to 17 instead of 31 Configure the bootloader In /etc/default/grub edit GRUB_CMDLINE_LINUX_DEFAULT, add nmi_watchdog=1 to capture a dump in case of a system hang In /etc/default/grub.d/kdump-tools.cfg change crashkernel value to 384M-:256M (default is 384M-:128M) Expected result: GRUB_CMDLINE_LINUX_DEFAULT="$GRUB_CMDLINE_LINUX_DEFAULT crashkernel=384M-:256M" ave and run sudo update-grub SUSE Linux Install kdump sudo zypper in kdump kexec-tools Edit /etc/sysconfig/kdump Change KDUMP_DUMPLEVEL variable to 17 Edit /etc/default/grub Edit GRUB_CMDLINE_LINUX_DEFAULT, add crashkernel=256M to reserve enough RAM for the dump kernel to run, and nmi_watchdog=1, to capture a dump in case of a system hang Update the bootloader configuration sudo grub2-mkconfig -o /boot/grub2/grub.cfg Reboot Enable kdump service sudo systemctl enable --now kdump.service Configure SysRq dump trigger To enable SysRq trigger, these key combinations 'kernel.sysrq = 8'(without quotes) has to be added to /etc/sysctl.conf. In SUSE the value of kernel.sysrq has to be changed in /usr/lib/sysctl.d/50-default.conf instead of /etc/sysctl.conf Reboot or run sudo sysctl --system After the set up above is complete, to manually trigger a dump press Alt+SysRq, Alt+C. Alternatively: echo 8 | sudo tee /proc/sys/kernel/sysrq (Command above is only needed if kernel.sysrq is not set in /etc/sysctl.conf) echo c | sudo tee /proc/sysrq-trigger Location of the dump files may vary between different Linux versions, it is configurable in the kdump configuration file. In Debian based distributions it is set by KDUMP_COREDIR variable. In Red Hat based distributions it is set by the path setting, generally the default location is /var/crash. Make sure that the dump folder has enough free space for the dump to be written. You may search by filemask: vmcore.
-

2 questions about Kaspersky Plus
Flood and Flood's wife replied to DedoP's topic in Kaspersky: Basic, Standard, Plus, Premium
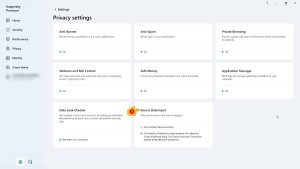
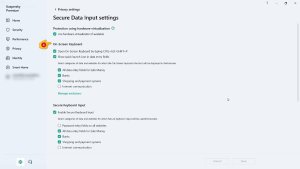
Hello DedoP, Welcome! 1. There is no interface language change Setting, (you) need to download & install - Kaspersky Plus - English version - from Kaspersky's Global website, using this link: Kaspersky Plus for Windows® 2. Please follow these images & the read the documentation: Protecting personal data on the Internet About protection of personal data on the Internet About On-Screen Keyboard How to open On-Screen Keyboard How to configure the display of the On-Screen Keyboard icon About protection of data entered on the computer keyboard How to configure protection of data entered on the computer keyboard Any questions or issues, please post back? Thank you🙏 Flood🐳+🐋



.thumb.jpg.abdc98a35c46f6ccc0ebc58394df874e.jpg)