All Activity
- Past hour
-
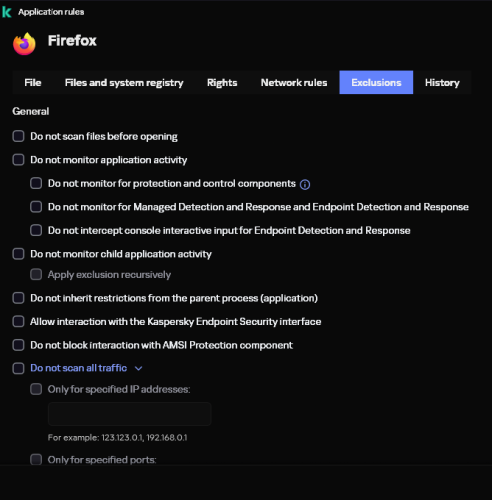
[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
AlexeyK replied to rbmancini's topic in Virus and Ransomware related questions
In 99% of cases - yes.) If the exception still needs to be configured, attach screenshots of your exception and AV detection - we'll try to help. -
В KSeC доступна только одна локация
AlexeyK replied to Zaurbek's topic in Kaspersky Secure Connection
Это давно так в России, тут не связано с переездом сервиса. В остальном - да, много тут еще предстоит налаживать. Спасибо за комментарий! -

[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
rbmancini replied to rbmancini's topic in Virus and Ransomware related questions
I tried exclusions and actions rules without success... maybe I did something wrong, I'm not sure. The guy from KeyPress OSD wrote this about virus warnings: https://keypressosd.com/virus-warnings/ He says there is an old version of the App that does not triggers this virus issues, but it is outdated. He also says "there is the option to certify the binary files, by obtaining a code signing certificate from a trusted Certificate Authority, e.g., DigiCert. However, this is very expensive and I am not yet ready to invest into it." -
В KSeC доступна только одна локация
iapet_us replied to Zaurbek's topic in Kaspersky Secure Connection
Да, без проблем. Скорость низкая, видеопоток даже в 720p стабильно не идет. Это вдобавок к абсолютно клоунской ситуации, когда приложение ksec отказывается работать при наличии kaspersky, но в самом приложении kaspersky подписка на ksec не видна. В чате поддержки посоветовали снести kaspersky и ksec, переустановить ksec НЕ устанавливая kaspersky, и добавить подписку. Так действительно заработало, НО при установке kaspersky обратно - вернулся к тому, с чего начал. Офк и kaspersky, и ksec под одной учеткой куплены. - Today
-
В KSeC доступна только одна локация
AlexeyK replied to Zaurbek's topic in Kaspersky Secure Connection
А можно чуть подробнее, чем именно недовольны? Скорость плохая, обрывы, что-то еще? Ну это помимо 1 локации. А то пока с такой ситуацией обновленного сервиса мало кто из пользователей встречался. -
Может ли стать причиной блокировки работы USB-модема?
A.S.R. replied to A.S.R.'s topic in Kaspersky: Basic, Standard, Plus, Premium
1. ОС - 22Н2 Сборка 19045.5965 Каспер - 21.21.7.384(а) 2. Huawei M150-2 3. Нет 4. Нет 5. Нет. 6. Как написала выше, удалить антивирус не могу, потом я его не поставлю из-за слабого интернет-соединения. Я вот что подумала - не мог антивирус прохлопать какой-нибудь вирус? Это была моя первая мысль. Я делала полную проверку и он ничего не нашел. Но, может быть, что-то где-то спряталось? Вот, проверила настройки. Кажется, все так, как у вас на скрине. -
[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
AlexeyK replied to rbmancini's topic in Virus and Ransomware related questions
"Exclusions and actions on object detection", section "Manage exclusions": https://support.kaspersky.com/help/Kaspersky/Win21.21/en-US/201385.htm -
d.vareni joined the community
-
Вовчик joined the community
-

[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
harlan4096 replied to rbmancini's topic in Virus and Ransomware related questions
-

[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
rbmancini replied to rbmancini's topic in Virus and Ransomware related questions
Yes, it really isn’t the most secure solution. I tried adding the application to a list of trusted apps, but it didn’t work. If Kaspersky itself suggested pausing protection, I believe there must be a good reason—perhaps it isn’t possible to add this application to the trusted apps list. In any case, I only use the app when I’m recording lessons, so the computer is unprotected for just a short period. -

kaspersky premium Problemas de uso de aplicaciones con KASPERSKY PREMIUM
harlan4096 replied to PowerSystemPC's topic in Para usuarios particulares
Bienvenido a la Comunidad de Kaspersky. Por favor, indica versión de KPremium instalada en los equipos. Indica también qué configuraciones habéis probado para mitigar el problema. -
Сергей1972 joined the community
-
iapet_us started following В KSeC доступна только одна локация
-
В KSeC доступна только одна локация
iapet_us replied to Zaurbek's topic in Kaspersky Secure Connection
Поддерживаю автора треда - оплаченный впн работает хуже бесплатного + доступна только 1 локация. Какие сроки поставки качественного решения? -
iapet_us joined the community
-
harlan4096 started following Problemas de uso de aplicaciones con KASPERSKY PREMIUM
-
PowerSystemPC started following Problemas de uso de aplicaciones con KASPERSKY PREMIUM
-
kaspersky premium Problemas de uso de aplicaciones con KASPERSKY PREMIUM
PowerSystemPC posted a topic in Para usuarios particulares
Hola, buenas tardes. Tenemos bastantes equipos con el antivirus KASPERSKY PREMIUM, y estamos satisfechos trabajando con esta marca, pero desde ya hace casi dos meses hemos tenido un problema extraño, del cual no hemos encontrado solución, pero si hemos podido identificar el causante del problema, el cual es por el antivirus; me explico, nosotros brindamos servicio de Soporte Técnico de computadoras, Modelado 3D, Marketing y diseño gráfico en general, y hemos tenido problemas con el programa Corel Graphics Suite 2024 y 2025, con los Corel antiguos no sucede esto, el problema es que cuando el antivirus esta activado, el Corel se demora una eternidad en abrir, unos más que otros, incluso cuando ya está abierto tratamos de abrir los archivos de diseño y se demora bastante, pero cuando cerramos el antivirus todo funciona perfecto, el Tecnico de la empresa ya ha tratado de cambiar la configuración de distintas formas sin resultado alguno, esto nos sucede con más de 20 equipos para lo cual nos hemos visto forzados a cerrar el antivirus para poder trabajar, lo cual expone el equipo a amenazas. Por favor, asistencia del por qué ocurre este problema y que podemos hacer, no queremos dejar de usar este producto suyo por un detalle, que estoy seguro se puede solucionar -

Cuidado prishing!!! Correo electrónico
JFNoda replied to Nathaniel's topic in Para usuarios particulares
Hola @Nathaniel Si no lo has recibido en tu cuenta de correo que tienes vinculada a MyKaspersky, no debería tener problemas. Que nunca hayas tenido la cuenta de correos, donde recibiste el email, vinculado a nada referente a Kaspersky.. está claro que Kaspersky nada tiene que ver con ese aviso, por lógica. Mi opinión personal. Slds. -
diflyon joined the community
-
PowerSystemPC joined the community
-
Erinaldo joined the community
-
Berny started following "Search-sprint.com" malware virus
-

Phishing from my email address
Berny replied to MarcInOz's topic in Virus and Ransomware related questions
@Abiodun Bralewood Welcome. Please see the Post from @harlan4096 above your Post. Also , please check the options under : Home → ⚙️Settings → Security settings → Mail Anti-Virus settings -

"Search-sprint.com" malware virus
harlan4096 replied to Dinesh's topic in Virus and Ransomware related questions
Welcome to Kaspersky Community. That looks like a Browser Hijacker, it may change the browser homepage, search engine without user permission. Try resetting your web browser settings: https://support.google.com/chrome/answer/3296214?hl=en&sjid=1865998812496049318-EU https://umatechnology.org/how-to-reset-google-chrome-on-android-smartphones/- 1 reply
-
- 1
-

-
Предложения к Kaspersky Password Manager
Kastor replied to supportIV's topic in Kaspersky Password Manager
Очевидно, что все клиентские пути должны быть едины на всех версиях приложения для всех платформ, если при этом, конечно, нет технических ограничений. На версии для iOS кнопка поиска удобно расположена внизу экрана прямо под пальцем, нажимаешь и сразу пошел ввод данных для поиска на появившейся клавиатуры, поэтому проблемы активации поиска в данном случае нет. -

Предложения к Kaspersky Password Manager
kmscom replied to supportIV's topic in Kaspersky Password Manager
Если писать каки-то предложения, то оно должно быть точным и однозначным. Менеджер работает еще на iOS и Android. А то получается, другим предлагаете провести исследования, а сами в сути своего же предложения не разобрались. -

Предложения к Kaspersky Password Manager
andrew75 replied to supportIV's topic in Kaspersky Password Manager
@Kastor, я не сотрудник компании, я такой же пользователь как и вы. И высказываю свою точку зрения. Вы же ссылаетесь на действия "любого пользователя". Я показал что есть пользователи, которые действуют иначе. На самом деле, если приложение нормально распознает сайты и приложения, в которых нужно подставить пароли, то поиск требуется редко. Вы же не написали, на какой системе работаете. Возможно разработчики прислушаются к вашей точке зрения. -
harlan4096 started following "Search-sprint.com" malware virus
-
Предложения к Kaspersky Password Manager
Kastor replied to supportIV's topic in Kaspersky Password Manager
Так делают международные менеджеры паролей, которые существуют на рынке и развиваются уже более 10 лет. В частности я про версию приложения для Mac OS. Если этот клиентский путь для вас не очевиден, то проведите исследование. Либо собственными силами, если имеются компетенции и соответствующая форма организации бизнес-процессов и принятия решений, которые позволяют выработать и принять объективно правильное решение, либо закажите исследование в сторонней, специализированной организации. И, кстати, зачем сначала спорить, а потом признавать, что так уже реализовано в версии на Windows? Я не помню как именно в версии для Windows реализовано. -

Предложения к Kaspersky Password Manager
andrew75 replied to supportIV's topic in Kaspersky Password Manager
Если так делаете вы, это не значит что так делают все. У меня больше 10 паролей, а я так не делаю ) Но вообще на Windows версии программа так себя и ведет. Или я не понял, что именно вы хотите? Вот я открыл приложение и курсор находится в поле поиска: -
Kastor started following Предложения к Kaspersky Password Manager
-
Предложения к Kaspersky Password Manager
Kastor replied to supportIV's topic in Kaspersky Password Manager
Здравствуйте. Сделайте на всех версиях приложения так, чтобы после ввода мастер-пароля при загрузке приложения, сразу был бы активирован ввод данных в поле для поиска. Так как это первое, что делает любой пользователь с количеством паролей больше 10. -
Crowen joined the community
-
Kastor joined the community
-
Dinesh started following "Search-sprint.com" malware virus
-
Malware called "search-sprint.com" virus have attacked my chrome and have lost the connetivity to the Internet. Kaspersky scan and the tools have not helped Can any one please highlight how it can be resolved.
-
Abiodun Bralewood started following Phishing from my email address
-
Phishing from my email address
Abiodun Bralewood replied to MarcInOz's topic in Virus and Ransomware related questions
How can i use Kaspersky to block phishing emails? -
Abiodun Bralewood joined the community
-

[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
harlan4096 replied to rbmancini's topic in Virus and Ransomware related questions
Yes, but an unsecure solution -> pausing protection... -

[False Positive] KeyPress OSD (AHK-based tool) blocked by Kaspersky Plus – how to whitelist?
rbmancini replied to rbmancini's topic in Virus and Ransomware related questions
Hello. I received the following message from Kaspersky support: "In this case, you can pause Kaspersky while using the tool: right-click the Kaspersky icon in the lower-right corner and select “Pause Protection.” Then you can use the tool while Kaspersky is paused so that no conflict occurs." Answering your question, the antivirus simply does not allow the use of the application. It blocks it and automatically deletes the executable file (.exe). The solution proposed by Kaspersky does indeed resolve the problem.