All Activity
- Past hour
-

KIS blocking a programs https call (Mordhau)
harlan4096 replied to beoxtc's topic in Kaspersky Internet Security
Welcome to Kaspersky Community. I would migrate 1st Your KIS to Kaspersky Standard, KIS getting obsolete, and then re-test.- 1 reply
-
- 1
-

-
harlan4096 started following KIS blocking a programs https call (Mordhau)
-
Danila T. started following Какая минимальная версия android поддерживается Kaspersky Safe Kids?
-
Какая минимальная версия android поддерживается Kaspersky Safe Kids?
Danila T. replied to Александр Доманский's topic in Kaspersky Safe Kids
Добрый день: https://support.kaspersky.com/KSK/Mob1.0-iOSTR106-AndroidTR108/ru-RU/94957.htm операционная система: Android 7 и более поздние; -

it-sa - Europas größte Fachmesse für IT-Sicherheit in Nürnberg
alexcad posted a topic in Für Unternehmen
Hallo Zusammen, auch dieses Jahr findet im Oktober die it-sa in Nürnberg statt: 7. - 9. Oktober 2025 Messezentrum Nürnberg https://www.itsa365.de/de-de/it-sa-expo-congress Vielleicht sehen wir uns am Kaspersky-Stand? Halle 7 Stand 312! https://www.kaspersky-dach.de/kaspersky-it-sa-2025/ Grüße Alex -
beoxtc started following KIS blocking a programs https call (Mordhau)
-
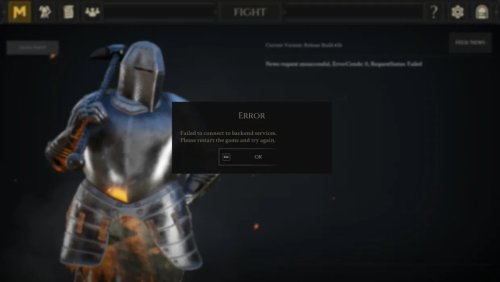
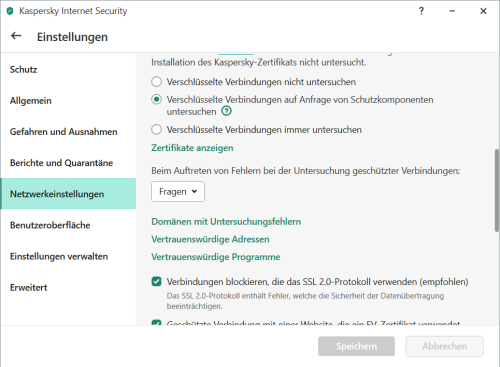
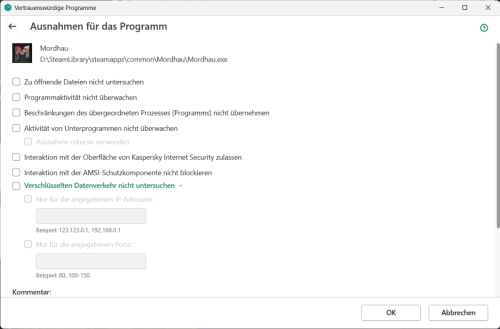
Hello there, Version of your operating system: Windows 11 Version 24H2 (OS Build 26100.4652) Name and version number of the Kaspersky application: 21.3.10.391 (m) When starting Mordhau (a game on Steam), I'm experiencing an error message. Digging into the logs, it seems that part of the SSL messages can't get through. Disabling KIS totally helps to get past this problem. I couldn't yet isolate that problem. Another problem related to this one: Whenever I want to add Mordhau to the list of exceptions for programs, Kaspersy crashes. Otherwise I'd just add a rule to omit that game. On the second screenshot, when I press OK, KIS crashes and I'm sending the reports to you. If necessary, attach a screenshot of the problem You can read my troubleshooting with the game developers in this discord thread https : //discord.com/channels/275436245318893568/1399120255774756895 In the logs ``` [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: request failed, libcurl error: 35 (SSL connect error) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 0 ( Trying 20.42.182.108...) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 1 (TCP_NODELAY set) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 2 (Connected to 12D56.playfabapi.com (20.42.182.108) port 443 (#1)) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 3 (ALPN, offering http/1.1) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 4 (Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 5 (TLSv1.3 (OUT), TLS handshake, Client hello (1):) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 6 (OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to 12D56.playfabapi.com:443 ) [2025.07.30-23.19.09:635][ 21]LogHttp: Warning: 00000210B36A2990: libcurl info message cache 7 (Closing connection 1) [2025.07.30-23.19.09:635][ 21]LogPlayFabAPI: Error: RetryRequest: LoginWithSteam request exhausted retries (1) [2025.07.30-23.19.09:635][ 21]LogPlayFabAPI: Error: LoginWithSteam: Request Timeout or null response (2 Request Timeout or null response) [2025.07.30-23.19.09:636][ 21]LogMordhauGameInstance: Error: Platform login failed, Reason: Login failed ``` Please help, either with the Mordhau problem, or the exceptions problem, either one I'm ok with as long as I can play my game with it. Cheers, tempx
-
Александр Доманский started following Какая минимальная версия android поддерживается Kaspersky Safe Kids?
-
Какая минимальная версия android поддерживается Kaspersky Safe Kids?
Александр Доманский posted a topic in Kaspersky Safe Kids
Какая минимальная версия android поддерживается Kaspersky Safe Kids? Нигде не нашёл данной информации. У ребёнка старый смартфон Redmi Note 4X. -
Александр Доманский joined the community
-
beoxtc joined the community
-
С этим стоит обратиться в техподдержку.
-
stan4ever started following kaspersky vpn
-
привет! такая проблемка.. на андроид 11 телефоне стоит касперский впн, стали переставать работать страны впн, хотя наверное это глюк.. в общем выбираешь страну(например аргентина) через некоторое время перестает работать интернет, переключаешься на другую - работает.. страны запоминает, повторно не работает.. хотя наверное это блажь..
- Today
-
clavo joined the community
-
Magdy joined the community
-
greendalf joined the community
-
Сергей Егоров started following Релиз Kaspersky Endpoint Security для Linux 12.3
-
Добрый день, @Mi14ek, Какая версия Mac OS? Все обновления Mac OS установлены? В других приложениях работает? Попробуйте переустановить Kaspersky Password Manager: 1. Удалите стандартным образом Kaspersky Password Manager 2. Перезагрузите устройство. 3. Скачайте и установите последнюю версию.
-
1.1. Scenario: KATA/EDR CN is deployed on site, and there are some remote users that cannot connect to the internal network, and you want to receive the EDR telemetry from those endpoints and laptops when they are outside the network (considering that you don't have any VPN functionality). You don't want to expose the CN on the internet, so you'd like to use the sensor to relay the telemetry to the CN and have visibility on the endpoints. 1.2. Pre-requisites and configuration steps: To achieve the above scenario, we can deploy the KATA Network Sensor in the DMZ and publish it on the internet for remote and roaming users. The Network Sensor will be integrated with the CN and public IP/FQDN will be used to send the traffic from the internet to the sensor using port 443. Two KES policies (Active/Out of Office) will be configured, The Active policy will have the KATA CN internal IP and the Out-of-Office policy will have the public IP/FQDN for KATA Sensor. Connection profiling can be used to switch between the policies (similar to the connection gateway for KSC). The below steps need to be performed for the successful deployment and integration. Deploy the KATA Network Sensor in the DMZ Configure to integrate with CN, and accept the request on the CN side. When using the KEDR license, the Accept button might not be available, integration of the KATA sensor requires a KATA license, or the latest KATA patch should be applied on the CN to fix this issue. Export the certificate from the KATA Sensor using WinScp and copy it to the local computer or KSC server. Note: you might need to allow the connection using WinSCP: https://forum.kaspersky.com/blogs/entry/100-how-to-copy-files-tofrom-kata-katakedre/ Location of the certificate = /etc/pki/tls/certs/ File name = kata.crt Copy the kata.crt to /tmp/ and change the permissions to download the file. Configure the destination NAT from Firewall towards KATA sensor internal IP for port 443. Configure the KES (Out-of-office) policy and add the Public FQDN/IP in the connection settings along with the sensor certificate. Apply the KES (Out-of-office) policy to a test laptop. Disconnect the Laptop from the network and wait for the connection to be established from the internet with KATA Sensor. Verify the Endpoint status on the Central Node and check for the recent events.
-
Description and cautions This article may be useful in certain cases, when you see that virtual machines running on the KATA Sandbox can not access internet using the properly configured malware interface. One can notice the issue based on several symptoms, such as VM activation errors, samples sent to Sandbox for processing not accessing internet, etc... We recommend to use the following article to check if the malware channel works properly on the KATA Sandbox server or not: https://forum.kaspersky.com/blogs/entry/162-how-to-test-malware-interface-on-kata-sandbox-katakedre/ Details In case if the tests listed above indeed show that malware channel fails to connect to the internet, we recommend to do the following checks among others: Run the following command on the sandbox server to check the currently configured network settings for the Sandbox: # /opt/kaspersky/sandbox/bin/sbnetworking all show check in the command's output if the malware interface is configured properly, i.e. it's intended IP, subnet, gateway, etc. Example of such output below: Correct values if they are misconfigured somehow from the web interface and don't forget to apply the settings afterwards and restart the host, to propagate those (prompt for restart will pop-up in the Sandbox web interface after applying those). Run the following command to check the system log on the Sandbox server if there are certain errors related to networking in general and malware interface in particular: # journalctl -u network # journalctl -u sandbox-networking.service In case if all checks listed above were passed, and there are no misconfigurations found and/or no specific errors were found in system journal, then try checking if routing is properly configured for the malware channel, i.e. run the following command: # ip route show table 701 Expected output below: if the output will be missing the default route entry via configured gateway for the malware interface, then add it manually like so: # ip route add default via <gateway's IP> table 701 after adding the route, double check that it indeed exists: # ip route show table 701 then restart the sandbox-networking service manually or the Sandbox server itself: # systemctl restart sandbox-networking.service Please note, that restarting sandbox-networking service may take a while especially on production servers that are processing a lot of samples at the moment and/or have a lot of worker slots. Thus it is highly recommended to detach this Sandbox server from KATA for the time of restart and expect 40 minutes - several hours downtime to complete the procedure. after restarting the sandbox-networking service check if you can ping public locations successfully from internet interface's namespace: # /opt/kaspersky/sandbox/bin/ns_exec /var/run/netns/dom1 /bin/ping -c 3 8.8.8.8
-
Melaku Mara joined the community
-
Сергей Егоров started following Релиз Kaspersky Endpoint Security для Windows 12.10
-
Сергей Егоров joined the community
-
KSC API use cases examples - host isolation with KES/KEA [KSC for Windows]
svc_kms commented on svc_kms's blog entry in Kaspersky Security Center's Kaspersky Security Center Community
KES Isolation (11.7 and upper) FindHost Find Host with previous method and copy value "KLHST_WKS_HOSTNAME" For example: "KLHST_WKS_DN":"KEDRO-1","KLHST_WKS_HOSTNAME":"a20da5de-49e5-469a-92ea-41b5adb74ea4" SrvView Find srvview data by filter string (SrvView::ResetIterator) "wstrViewName" - check List of supported srvviews. "vecFieldsToReturn" - check https://support.kaspersky.com/help/KSC/13.1/KSCAPI/a00307.html SrvView::ResetIterator POST /api/v1.0/SrvView.ResetIterator HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 614 { "wstrViewName": "HostTasksSrvView", "vecFieldsToReturn": [ "nState", "strTask", "TASK_NAME", "txtDisplayName", "TASKID_PRODUCT_NAME", "TASKID_PRODUCT_VERSION", "bCannotBeDeleted", "bSystem" ], "vecFieldsToOrder": [ { "type": "params", "value": { "Name": "TASK_NAME", "Asc": "true" } } ], "lifetimeSec": 100, "pParams": { "strHostId": "a20da5de-49e5-469a-92ea-41b5adb74ea4" }, "wstrFilter": "" } Response ID Response {"wstrIteratorId":"67D74142AE0FA1A3D05CD696B957902B"} GetRecordRange from Response data (SrvView.GetRecordRange) SrvView.GetRecordRange curl -L -X POST "https://127.0.0.1:13299/api/v1.0/SrvView.GetRecordRange" -H "X-KSC-Session: noOxgI9Ny7O5Whg/97qvcVg==" -H "Content-Type: application/json" --data-raw "{ \"wstrIteratorId\":\"67D74142AE0FA1A3D05CD696B957902B\", \"nStart\": 0, \"nEnd\": 100 }" Copy value "strTask" for Task "xdr_networkisolation_start" and "xdr_networkisolation_stop" For example: Isolation ON => "TASK_NAME":"xdr_networkisolation_start" .... "strTask":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056" Isolation OFF => "TASK_NAME":"xdr_networkisolation_stop .... "strTask":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d" Isolation ON GetHostTasks Return server specific identity to acquire and manage host tasks. (HostGroup::GetHostTasks) HostGroup.GetHostTasks POST /api/v1.0/HostGroup.GetHostTasks HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 58 { "strHostName":"a20da5de-49e5-469a-92ea-41b5adb74ea4" } Response: Response {"PxgRetVal":"8122017D5C4081753E8FDE94244DC1AF"} HostTasks GetTaskData Acquire task settings. (HostTasks::GetTaskData) strSrvObjId - server object ID that got from HostGroup.GetHostTasks strTask - storage identifier of the task (such as returned by HostTasks.AddTask) HostTasks::GetTaskData POST /api/v1.0/HostTasks.GetTaskData HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 112 { "strTask":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056", "strSrvObjId":"8122017D5C4081753E8FDE94244DC1AF" } Response: Response {"PxgRetVal":{"EVENT_TYPE":"PRTS_EVENT_NONE","FILTER_EVENTS_COMPONENT_NAME":"","FILTER_EVENTS_INSTANCE_ID":"","FILTER_EVENTS_PRODUCT_NAME":"","FILTER_EVENTS_VERSION":"","TASKID_COMPONENT_NAME":"Connector","TASKID_INSTANCE_ID":"","TASKID_PRODUCT_NAME":"KES","TASKID_VERSION":"11.0.0.0","TASKSCH_FIRST_EXECUTION_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASKSCH_FIRST_EXECUTION_TIME_SEC":0,"TASKSCH_LIFETIME":{"type":"datetime","value":""},"TASKSCH_MS_PERIOD":0,"TASKSCH_RUN_MISSED_FLAG":false,"TASKSCH_TYPE":0,"TASK_ADDITIONAL_PARAMS":{"type":"params","value":{"CompatibilityInfo":{"type":"params","value":{"MinimalPluginVersion":"11.7.0.0"}},"PRTS_TASK_EXT_SHEDULE_FLAGS":0,"exclusionRules":[{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}},"name":"DNS","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}},"name":"DNS","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":true,"paths":["%systemroot%\\system32\\dns.exe"]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":65535,"start":49152}}]}},"name":"Large numbered TCP ports, randomly assigned by the RPC service","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":true,"paths":["%systemroot%\\system32\\svchost.exe"]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":135,"start":135}}]}},"name":"RPC Endpoint Mapper","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":0,"localPorts":{"type":"params","value":{"enabled":false,"portRange":[]}},"name":"DNS client","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":0,"localPorts":{"type":"params","value":{"enabled":false,"portRange":[]}},"name":"DNS client","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":53,"start":53}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":2,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":68,"start":68}}]}},"name":"DHCP server","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":67,"start":67}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":2,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":67,"start":67}}]}},"name":"DHCP client","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":68,"start":68}}]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":2535,"start":2535}}]}},"name":"MADCAP","protocol":{"type":"params","value":{"enabled":true,"id":17}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}},{"type":"params","value":{"applications":{"type":"params","value":{"enabled":false,"paths":[]}},"dataSource":1,"localPorts":{"type":"params","value":{"enabled":true,"portRange":[{"type":"params","value":{"end":647,"start":647}}]}},"name":"DHCP failover","protocol":{"type":"params","value":{"enabled":true,"id":6}},"remoteAddress":{"type":"params","value":{"enabled":false,"ip":{"type":"params","value":{"octets":{"type":"binary","value":""},"zoneIPv6":""}}}},"remotePorts":{"type":"params","value":{"enabled":false,"portRange":[]}}}}],"isolationDuration":3600000,"klprts-TaskStorageId":"_LOCAL_2d076fbe-7e60-4a99-9177-173076a5a2b1","ksc_settings_compatibility::TaskUniqueId":"89621cce@xdr_networkisolation_start@NetworkIsolationStart","responseId":{"type":"long","value":7998665773575485050}}},"TASK_CLASS_ID":0,"TASK_DEL_AFTER_RUN_FLAG":false,"TASK_INFO_PARAMS":{"type":"params","value":{"DisplayName":"Network isolation","klprts-TaskCannotBeDeleted":true,"klprts-TaskScheduleSubtype":256}},"TASK_LAST_EXEC_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASK_LAST_EXEC_TIME_SEC":0,"TASK_MAX_EXEC_TIME":0,"TASK_NAME":"xdr_networkisolation_start","TASK_PREP_START":0,"TASK_PRIORITY":1,"TASK_START_DELTA":0,"TASK_UNIQUE_ID":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056"}} Copy some of value from response and change parameters on next request with Network isolation exclusions RDP protocol (for example): exclusionRules { "type": "params", "value": { "applications": { "type": "params", "value": { "enabled": true, "paths": [] } }, "dataSource": 2, #inbound and outbound "localPorts": { "type": "params", "value": { "enabled": true, "portRange": [ { "type": "params", "value": { "end": 3389, #port "start": 3389 #port } } ] } }, "name": "RDP ANY", #name "protocol": { "type": "params", "value": { "enabled": true, "id": 0 #TCP and UDP } }, "remoteAddress": { "type": "params", "value": { "enabled": false, "ip": { "type": "params", "value": { "octets": { "type": "binary", "value": "" }, "zoneIPv6": "" } } } }, "remotePorts": { "type": "params", "value": { "enabled": false, "portRange": [] } } } } UpdateTask Modify task settings. ( HostTasks::UpdateTask) HostTasks::UpdateTask Collapse source POST /api/v1.0/HostTasks.UpdateTask HTTP/1.1 Host: localhost:13299 X-KSC-Session: n18Zfc+1hPeedqD07uM96/A== Content-Type: application/json Content-Length: 32796 { "strTask": "_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056", "strSrvObjId": "46A9BEBC82C3FB1121050247A0697ECC", "pData": { "TASKID_COMPONENT_NAME": "Connector", "TASKID_PRODUCT_NAME": "KES", "TASKID_VERSION": "11.0.0.0", "TASKSCH_TYPE": 5, "TASK_ADDITIONAL_PARAMS": { "type": "params", "value": { "CompatibilityInfo": { "type": "params", "value": { "MinimalPluginVersion": "11.8.0.0" } }, "PRTS_TASK_EXT_SHEDULE_FLAGS": 0, "exclusionRules": [ { "type": "params", "value": { "applications": { "type": "params", "value": { "enabled": true, "paths": [] } }, "dataSource": 2, "localPorts": { "type": "params", "value": { "enabled": true, "portRange": [ { "type": "params", "value": { "end": 3389, "start": 3389 } } ] } }, "name": "RDP ANY", "protocol": { "type": "params", "value": { "enabled": true, "id": 0 } }, "remoteAddress": { "type": "params", "value": { "enabled": false, "ip": { "type": "params", "value": { "octets": { "type": "binary", "value": "" }, "zoneIPv6": "" } } } }, "remotePorts": { "type": "params", "value": { "enabled": false, "portRange": [] } } } } ], "isolationDuration":28800000, "klprts-TaskStorageId":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056", "ksc_settings_compatibility::TaskUniqueId":"89621cce@xdr_networkisolation_start@NetworkIsolationStart", "responseId":{"type":"long","value":4294967295}}}, "TASK_CLASS_ID":0, "TASK_DEL_AFTER_RUN_FLAG":false, "TASK_INFO_PARAMS": {"type":"params","value":{ "DisplayName":"Network isolation", "klprts-TaskCannotBeDeleted":true, "klprts-TaskScheduleSubtype":512} }, "TASK_NAME":"xdr_networkisolation_start", "TASK_PREP_START":0, "TASK_PRIORITY":1, "TASK_START_DELTA":0, "TASK_UNIQUE_ID":"_LOCAL_2212c5ce-c23d-4c55-8bca-656221d5f056" } } Response Response { } Host isolated successful with allowed RDP session. Isolation OFF For example: Isolation OFF => "TASK_NAME":"xdr_networkisolation_stop .... "strTask":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d" GetHostTasks Return server specific identity to acquire and manage host tasks. (HostGroup::GetHostTasks) HostGroup.GetHostTasks POST /api/v1.0/HostGroup.GetHostTasks HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 58 { "strHostName":"a20da5de-49e5-469a-92ea-41b5adb74ea4" } Response: Response {"PxgRetVal":"8122017D5C4081753E8FDE94244DC1AF"} HostTasks GetTaskData Acquire task settings. (HostTasks::GetTaskData) strSrvObjId - server object ID that got from HostGroup.GetHostTasks strTask - storage identifier of the task (such as returned by HostTasks.AddTask) HostTasks::GetTaskData POST /api/v1.0/HostTasks.GetTaskData HTTP/1.1 Host: localhost:13299 X-KSC-Session: nXo75DRoFMRjNp2jwByKlfg== Content-Type: application/json Content-Length: 112 { "strTask":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d", "strSrvObjId":"8122017D5C4081753E8FDE94244DC1AF" } Response: Response {"PxgRetVal":{"EVENT_TYPE":"PRTS_EVENT_NONE","FILTER_EVENTS_COMPONENT_NAME":"","FILTER_EVENTS_INSTANCE_ID":"","FILTER_EVENTS_PRODUCT_NAME":"","FILTER_EVENTS_VERSION":"","TASKID_COMPONENT_NAME":"Connector","TASKID_INSTANCE_ID":"","TASKID_PRODUCT_NAME":"KES","TASKID_VERSION":"11.0.0.0","TASKSCH_FIRST_EXECUTION_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASKSCH_FIRST_EXECUTION_TIME_SEC":0,"TASKSCH_LIFETIME":{"type":"datetime","value":""},"TASKSCH_MS_PERIOD":0,"TASKSCH_RUN_MISSED_FLAG":false,"TASKSCH_TYPE":0,"TASK_ADDITIONAL_PARAMS":{"type":"params","value":{"CompatibilityInfo":{"type":"params","value":{"MinimalPluginVersion":"11.8.0.0"}},"PRTS_TASK_EXT_SHEDULE_FLAGS":0,"klprts-TaskStorageId":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d","ksc_settings_compatibility::TaskUniqueId":"59e0cc70@xdr_networkisolation_stop@NetworkIsolationStop","responseId":{"type":"long","value":4294967295}}},"TASK_CLASS_ID":0,"TASK_DEL_AFTER_RUN_FLAG":false,"TASK_INFO_PARAMS":{"type":"params","value":{"DisplayName":"Termination of network isolation","klprts-TaskCannotBeDeleted":true,"klprts-TaskScheduleSubtype":256}},"TASK_LAST_EXEC_TIME":{"type":"datetime","value":"1970-01-01T00:00:00Z"},"TASK_LAST_EXEC_TIME_SEC":0,"TASK_MAX_EXEC_TIME":0,"TASK_NAME":"xdr_networkisolation_stop","TASK_PREP_START":0,"TASK_PRIORITY":1,"TASK_START_DELTA":0,"TASK_UNIQUE_ID":"_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d"}} Copy some value from response and change parameters on the next request with Network isolation exclusions. UpdateTask Modify task settings. ( HostTasks::UpdateTask) POST /api/v1.0/HostTasks.UpdateTask HTTP/1.1 Host: localhost:13299 X-KSC-Session: n18Zfc+1hPeedqD07uM96/A== Content-Type: application/json Content-Length: 32796 { "strTask": "_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d", "strSrvObjId": "A06A16B837CC0E73BD3BCCDAA98A3129", "pData": { "TASKID_COMPONENT_NAME": "Connector", "TASKID_PRODUCT_NAME": "KES", "TASKID_VERSION": "11.0.0.0", "TASKSCH_MS_PERIOD": 0, "TASKSCH_TYPE": 5, #change "TASK_ADDITIONAL_PARAMS": { "type": "params", "value": { "CompatibilityInfo": { "type": "params", "value": { "MinimalPluginVersion": "11.8.0.0" } }, "PRTS_TASK_EXT_SHEDULE_FLAGS": 0, "klprts-TaskStorageId": "_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d", "ksc_settings_compatibility::TaskUniqueId": "59e0cc70@xdr_networkisolation_stop@NetworkIsolationStop", "responseId": { "type": "long", "value": 4294967295 } } }, "TASK_CLASS_ID": 0, "TASK_DEL_AFTER_RUN_FLAG": false, "TASK_INFO_PARAMS": { "type": "params", "value": { "DisplayName": "Termination of network isolation", "klprts-TaskCannotBeDeleted": true, "klprts-TaskScheduleSubtype": 512 #change } }, "TASK_NAME": "xdr_networkisolation_stop", "TASK_PREP_START": 0, "TASK_PRIORITY": 1, "TASK_START_DELTA": 0, "TASK_UNIQUE_ID": "_LOCAL_f0395954-c011-445c-b2e3-0a1074a2cf8d" } } Response Response { } Host unblocked successfully. End Session to KSC (Session::EndSession) Session::EndSession curl --location --request POST 'https://127.0.0.1:13299/api/v1.0/Session.EndSession' --header 'X-KSC-Session: nsPbUpP1oAVZlM1lODEbg8A==' #PxgRetVal from Session.StartSession -
svc_kms started following KSC API use cases examples - host isolation with KES/KEA [KSC for Windows]
-
Description and cautions The article is giving some use cases examples of KSC API calls to ease one's start using the API. In that KB we are looking at host isolation with KES/KEA scenario. For the Windows version of cURL, you need to specify that the arguments need to be escaped with "\", otherwise there will be an error. For example: 'Authorization: KSCBasic user=\"YXBpLXVzZXI=\", pass=\"cGFzc3dvcmQ=\", internal=\"1\"' Details Prerequisites internal user: api-user Example KSC address - 127.0.0.1 (the address can also be external) API Port - 13299 (default) User: api-user (intrental KSC user), base64: YXBpLXVzZXI= Password: password, base64: cGFzc3dvcmQ= Credentials: User Password api-user password Base64: YXBpLXVzZXI= cGFzc3dvcmQ= Authentication, type: Authenticated session, other types: KSC Open API description Requests are in cUrl and http formats, as an alternative it is also possible to use Python library (KlAkOAPI Python package) Login Start connection to KSC (Session::StartSession) Session::StartSession curl --location --request POST 'https://127.0.0.1:13299/api/v1.0/Session.StartSession' \ --header 'Authorization: KSCBasic user="YXBpLXVzZXI=", pass="cGFzc3dvcmQ=", internal="1"' Username and password should be encoded to base64 format as part of a secure HTTPS session. For example, https://www.base64encode.org/ can be used for encoding. Response { "PxgRetVal": "nsPbUpP1oAVZlM1lODEbg8A==" } Use this token in request header Find Host Find host by filter string (HostGroup::FindHosts) Filter string, contains a condition over host attributes, see also Search filter syntax. We use "KLHST_WKS_DN" - Host display name HostGroup::FindHosts POST /api/v1.0/HostGroup.FindHosts HTTP/1.1 Host: localhost:13299 X-KSC-Session: nH4iKWCdxuBJWO5U4ATKSew== Content-Type: application/json Content-Length: 170 { "vecFieldsToReturn": [ "KLHST_WKS_HOSTNAME", "KLHST_WKS_DN" ], "lMaxLifeTime": 1200, "wstrFilter": "(KLHST_WKS_DN=\"WIN10-*\")" } Response ID Response {"strAccessor":"ppYeO5rmkvKcMUm8vQzOK2","PxgRetVal":18} Copy Accessor for next request (ChunkAccessor::GetItemsChunk) ChunkAccessor::GetItemsChunk curl -L -X POST "https://127.0.0.1:13299/api/v1.0/ChunkAccessor.GetItemsChunk" -H "X-KSC-Session: noOxgI9Ny7O5Whg/97qvcVg==" -H "Content-Type: application/json" --data-raw "{ \"strAccessor\":\"fb07haDqXIKZbQzyDsMwx1\", \"nStart\": 0, \"nCount\": 100 }" Response info about host: Response { "pChunk": { "KLCSP_ITERATOR_ARRAY": [ { "type": "params", "value": { "KLHST_WKS_DN": "WIN10-OPTIMUM-1", "KLHST_WKS_HOSTNAME": "c0816918-fbc5-4fbc-8fed-6f245756120e" } }, { "type": "params", "value": { "KLHST_WKS_DN": "WIN10-KES-11-OLD", "KLHST_WKS_HOSTNAME": "ab365e11-a1c7-492b-a981-e84402b33a8f" } } ] }, ........ "PxgRetVal": 18 } Copy value "KLHST_WKS_HOSTNAME" for next request KEA Isolation HostGroup.GetHostInfo Acquire specified host attributes. (HostGroup::GetHostInfo) strHostName (wstring) host name, a unique server-generated string (see KLHST_WKS_HOSTNAME attribute). It is NOT the same as computer network name (DNS-, FQDN-, NetBIOS-name) pFields2Return (array) array of names of host attributes to return. See List of host attributes for attribute names HostGroup.GetHostInfo POST /api/v1.0/HostGroup.GetHostInfo HTTP/1.1 Host: localhost:13299 X-KSC-Session: nH4iKWCdxuBJWO5U4ATKSew== Content-Type: application/json Content-Length: 185 { "strHostName":"ab365e11-a1c7-492b-a981-e84402b33a8f", "pFields2Return": [ "KLHST_WKS_HOSTNAME", "KLHST_WKS_DN", "KLHST_APP_INFO" ] } HostGroup.SS_GetNames Get section names from host settings storage. (HostGroup::SS_GetNames) Parameters values should be taken from the previous response. HostGroup::SS_GetNames POST /api/v1.0/HostGroup.SS_GetNames HTTP/1.1 Host: localhost:13299 X-KSC-Session: nqH6Qma75t/wBcQm8vlyqvQ== Content-Type: application/json Content-Length: 148 { "strHostName":"ab365e11-a1c7-492b-a981-e84402b33a8f", "strType":"SS_SETTINGS", "strProduct":"SOYUZ", "strVersion":"4.0.0.0" } Response: Response { "PxgRetVal": [ ".KLNAG_SECTION_REBOOT_REQUEST", "85", "AccountLogonSettings", "ApplicationSettings", "AutoStartEntriesNotifySettings", "ConnectionSettings", "CreateProcessSettings", "FileChangeNotificationSettsEdr", "KLEVP_NF_SECTION", "KsnServiceSettings", "LoadImageSettingsEdr", "MaintenanceSettings", "MdrServiceSettings", "MessageBrokerSettings", "NetworkConnectionSettingsEdr", "NetworkIsolationProfilesSetts", "NetworkIsolationSettings", #copy this field setting "PasswordSettings", "PreventionSettings", "ProductPermissionSettings", "QuarantineSettings", "SandboxSettings", "SelfDefenceSettings", "UserModeApiMonitorSrvSettings", "WMIActivitySettings", "WindowsEventLogSettingsEdr", "WindowsRegistrySettings" ] } With NWC web console KSC create local network exteption for VPN: 1) Open host properties → Applications → KEA 2) Open tab APP Settings → Network Isolation → Isolation on detection 3) Add rule for RDP → click "OK" → click "Save" HostGroup.SS_Read Read data from host settings storage. (HostGroup::SS_Read) Parameters values should be taken from two previous responses HostGroup::SS_Read POST /api/v1.0/HostGroup.SS_Read HTTP/1.1 Host: localhost:13299 X-KSC-Session: nqc+0P0UI+Wzuu+FREB74yQ== Content-Type: application/json Content-Length: 194 { "strHostName":"ab365e11-a1c7-492b-a981-e84402b33a8f", "strType":"SS_SETTINGS", "strProduct":"SOYUZ", "strVersion":"4.0.0.0", "strSection":"NetworkIsolationSettings" } Response info about Network Isolation with RDP rule exception: Response { "PxgRetVal": { "BaseSettings": { "type": "params", "value": { "Revision": { "type": "long", "value": 0 }, "__VersionInfo": [ 1, 0 ] } }, "Enable": false, "Exclusions": [ { "type": "params", "value": { "Description": "Custom (user-defined)", "Name": "Custom (user-defined)", "Rules": [ { "type": "params", "value": { "AppProtocolName": "RDP", "Applications": [], "Direction": 3, "Enable": true, "LocalAddress": "", "LocalPort": { "type": "params", "value": { "MaxPort": 3389, "MinPort": 3389, "__VersionInfo": [ 1, 0 ] } }, "Protocol": 0, "RemoteAddress": "", "RemotePort": { "type": "params", "value": { "MaxPort": 0, "MinPort": 0, "__VersionInfo": [ 1, 0 ] } }, "UseApplications": false, "UseLocalAddress": false, "UseLocalPort": true, "UseProtocol": false, "UseRemoteAddress": false, "UseRemotePort": false, "__VersionInfo": [ 1, 1 ] } } ], "__VersionInfo": [ 1, 0 ] } } ], "IsolationTimeout": 1800, "NotifyUser": true, "UseIsolationTimeout": true, "__VersionInfo": [ 1, 2 ] } } Copy all response for next request. HostGroup.SS_Write Write data to host settings storage for isolation workstation with RDP rule. (HostGroup::SS_Write) 1) Use previous value parameters 2) for nOption use 7 7 - "Clear", replaces existing section contents with pData, i.e. existing section contents will deleted and variables from pData will be written to the section. 3) for pSettings past previous response and change "Enable": true HostGroup::SS_Write POST /api/v1.0/HostGroup.SS_Write HTTP/1.1 Host: localhost:13299 X-KSC-Session: nbpsiiOAAxiDWfMSVkgciWQ== Content-Type: application/json Content-Length: 1066 { "strHostName":"bdcae680-eeaa-4279-a822-92a0d3e01dfb", "strType":"SS_SETTINGS", "strProduct":"SOYUZ", "strVersion":"4.0.0.0", "strSection":"NetworkIsolationSettings", "nOption":7, "pSettings":{ "BaseSettings": { "type": "params", "value": { "Revision": { "type": "long", "value": 0 }, "__VersionInfo": [ 1, 0 ] } }, "Enable": true, #Isolation ON "Exclusions": [ { "type": "params", "value": { "Description": "Custom (user-defined)", "Name": "Custom (user-defined)", "Rules": [ { "type": "params", "value": { "AppProtocolName": "RDP", #custom rule for RDP "Applications": [], "Direction": 3, "Enable": true, "LocalAddress": "", "LocalPort": { "type": "params", "value": { "MaxPort": 3389, "MinPort": 3389, "__VersionInfo": [ 1, 0 ] } }, "Protocol": 0, "RemoteAddress": "", "RemotePort": { "type": "params", "value": { "MaxPort": 0, "MinPort": 0, "__VersionInfo": [ 1, 0 ] } }, "UseApplications": false, "UseLocalAddress": false, "UseLocalPort": true, "UseProtocol": false, "UseRemoteAddress": false, "UseRemotePort": false, "__VersionInfo": [ 1, 1 ] } } ], "__VersionInfo": [ 1, 0 ] } } ], "IsolationTimeout": 1800, "NotifyUser": true, "UseIsolationTimeout": true, "__VersionInfo": [ 1, 2 ] } } Response Response { } Host isolated successfully. For off isolation you must change for pSettings past previous response and change "Enable": false
-
How to renew the KSC certificate correctly [KSC for Windows]
svc_kms posted a blog entry in Kaspersky Security Center's Kaspersky Security Center Community
This article is about Kaspersky Security Center for Windows (KSC for Windows) Problem: KSC certificate renewal or replacement is made incorrectly because the option to instantly replace the server certificate is used. There is an article in Online help dedicated to the klsetsrvcert utility (https://support.kaspersky.com/KSC/13.2/en-US/227838.htm). Sometime people follow the instructions according to the example indicated in the article – "klsetsrvcert -t C -i <inputfile> -p <password> -o NoCA" without thinking about the consequences. This leads to the fact that administration agents (nagents) do not receive a new certificate, and the users have to use the klmover utility. Cause: After the certificate is renewed with "-t C" option, network agents do not receive a new certificate and have no connection to the server. Solution: Run the certificate renewal script using the "-t CR" option (CR — Replace the common reserve certificate for ports 13000 and 13291) and the "-f" option in the <dd.mm.yyyy> format where we indicate the date 3–4 weeks ahead the current one. The time we set aside for changing the certificate to a backup one will allow a new certificate to be distributed to all Kaspersky Network Agents (Nagent): -t <type> Type of certificate to be replaced. Possible values of the <type> parameter: C—Replace the common certificate for ports 13000 and 13291. CR—Replace the common reserve certificate for ports 13000 and 13291. M—Replace the certificate for mobile devices on port 13292. MR—Replace the mobile reserve certificate for port 13292. MCA—Mobile client CA for auto-generated user certificates. -f <time> Schedule for changing the certificate, using the format "DD-MM-YYYY hh:mm" (for ports 13000 and 13291). Use this parameter if you want to replace the common or reserve certificate before it expires. Specify the time when managed devices must synchronize with Administration Server on a new certificate. For example, consider the command "klsetsrvcert.exe -f "DD-MM-YYYY hh:mm" -t CR -g nb.loc". Since this command was used in October, a backup certificate would be created and distributed to all nagents within a month. Thus, the certificate should have been applied on November 1, 2022. Let's check if the backup certificate has applied to the host. To do this, using the klscflag utility, enter the command: klscflag.exe -ssvget -pv 1103/1.0.0.0 -s KLNAG_SECTION_CERTDATA -n KLNAG_SSL_SERVER_CERT_RESERVE -ss '|ss_type = \"SS_LOCAL_MACHINE\";' The certificate has been delivered. If the backup certificate is not yet delivered to the destination host, we will see the following result of this command: Known problem: Problem with Webconsole login - incorrect user or password - see article https://forum.kaspersky.com/blogs/entry/331-ksc-web-console-shows-an-error-after-upgrade-incorrect-user-or-password-ksc-for-windows/ Error - Failed to establish connection with the remote device: This error occurs because we are trying to execute 2 consecutive commands on the same line. The first command is "-t CR -g nb.loc" and the second is "-f '20-12-2023 00:00'". Since the administration server restarts after executing the first command, the second command waits for some timeout before executing. But since in some user configurations, restarting the service can take a long time, the second part is performed when the server has not started yet. Which leads to the above error. In order to fix this behavior, you need to run the commands separately, according to this scenario: Run .\klsetsrvcert.exe -t CR -g nb.loc Wait until the administration server service starts completely (you can check by connecting the console). Run .\klsetsrvcert.exe -f '20-12-2023 00:00' -
The problem is in the certificate - it has a 1024 bit long key. While Web Console now works only with 2048 bit long keys. The customer needs to reissue KSC server certificate to 2048 key length. What to do - 1. Generate reserve KSC certificate - for example by using command - klsetsrvcert -t CR -g "dns_name" -o "RsaKeyLen:2048" where DNS name is DNS name of KSC 2. Wait several days - hosts will connect to KSC and receive reserve cert. The customer could check on client hosts that cert if received by the command - klscflag -ssvget -pv 1103/1.0.0.0 -s KLNAG_SECTION_CERTDATA -n KLNAG_SSL_SERVER_CERT_RESERVE -ss "|ss_type = \"SS_LOCAL_MACHINE\";" In results - if reserve cert is installed - there will be smthg like - +--- (PARAMS_T) +---KLNAG_SSL_SERVER_CERT_RESERVE = BINARY_T (size = 2944): 2D2D2D2D2D424547494E2043455254494649434154452D2D2D2D2D0A4D494945627A4343413165674177494241674955616E63416F503772716145594E44376265534D4D47396941716951774451594A4B6F5A496876634E4151454C0A42514177567A455A4D42634741315545417777516347786C61326868626D39324C6D46... If there is no reserve cert - there will be a message - FAILED - 1125 ('Parameter with name "KLNAG_SECTION_CERTDATA" not exist.') 3. Specify the date and time of next cert change by the command - klsetsrvcert -f "DD-MM-YYYY hh:mm" If you are sure that reserve cert if received already - you can specify the past date in this command - cert will be replaced right after that. Don't forget that if agent didn't receive reserve cert and cert is replaced already - agent will lost connection to KSC server. 4. Run WebConsole installer and specify new klserver cert there. Check the connection in WebConsole.
-
Добрый день, Была разница в адресе подключения, перевыпустил сертификат. Теперь на планшете и в сертификате одинаково. Но проблема сохранилась.
-
Banabas joined the community
-
Хотелось бы у KRD иметь функциональность шире, чем у KVRT. Ибо заморочек с созданием флешки больше. Тем более что эта функция была на прошлой версии.
-

How to analyze KATA collect script output [KATA/KEDRE]
Egor Erastov posted a blog entry in Kaspersky Anti Targeted Attack & EDR Expert's KATA & KEDR Expert community articles
Collect script output is a must for most KATA-related issues and questions. Which information? Which file? How to find/interpret? Example КАТА version and role: CN/PCN/SCN/Sensor /config/apt-va File contains the version and role in human-readable form. Also, you can see if the node was upgraded from previous KATA versions in 'migrate' line Primary CN [product] name=kata-cn title=Kaspersky Anti Targeted Attack Platform version=3.5.0-1269 release=release master = yes sensor = yes timestamp = 1568700994 migrate = cn_role = pcn Standalone CN [product] name=kata-cn title=Kaspersky Anti Targeted Attack Platform version=3.6.1-713 release=release master = yes sensor = yes timestamp =1572445307.01 migrate = cn_role = cn Sensor node [product] name=kata-cn title=Kaspersky Anti Targeted Attack Platform version=3.6.1-713 release=release master = no sensor = yes timestamp =1583845362.98 migrate = cn_role = Virtual or hardware? /environment/dmesg.txt OR /var/log/messages OR /var/log/boot.log Search for "DMI" entries in the file. Physical server [ 0.000000] DMI: HPE ProLiant DL560 Gen10/ProLiant DL560 Gen10, BIOS U34 06/20/2018 Virtual server [ 0.000000] DMI: VMware, Inc. VMware Virtual Platform/440BX Desktop Reference Platform, BIOS 6.00 04/05/2016 CPU /environment/cpuinfo.txt Scroll to the bottom of the file. Each "processor" listed is not a physical core, but virtual "thread", so, i.e. 8-physical core CPU with hyper-threading will have 16 CPUs in the file. Keep in mind that CPUs are counted from 0, so for 16-thread CPU last entry will have number 15. processor : 15 vendor_id : GenuineIntel cpu family : 6 model : 79 model name : Intel(R) Xeon(R) Platinum 8158 CPU @ 3.00GHz stepping : 0 microcode : 0x2000050 cpu MHz : 2992.968 cache size : 25344 KB physical id : 0 siblings : 16 core id : 15 cpu cores : 16 apicid : 15 initial apicid : 15 fpu : yes fpu_exception : yes cpuid level : 13 wp : yes flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts mmx fxsr sse sse2 ss ht syscall nx pdpe1gb rdtscp lm constant_tsc arch_perfmon pebs bts nopl xtopology tsc_reliable nonstop_tsc eagerfpu pni pclmulqdq ssse3 fma cx16 pcid sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand hypervisor lahf_lm abm 3dnowprefetch ibrs ibpb stibp fsgsbase tsc_adjust bmi1 hle avx2 smep bmi2 invpcid rtm rdseed adx smap xsaveopt arat spec_ctrl intel_stibp arch_capabilities bogomips : 5985.93 clflush size : 64 cache_alignment : 64 address sizes : 43 bits physical, 48 bits virtual power management: RAM /environment/memory.txt File shows free command output. Values are in megabytes, pay attention to 'total' and 'available' columns. NB! Ignore 'free' column: despite of it's name, it doesn't actually show free RAM, 'available' column does it. total used free shared buff/cache available Mem: 197308 63869 3634 6738 129804 125558 Swap: 0 0 0 HDD /environment/hdd.txt Pay attention to partitions /dev/sda* and /dev/sdb*. If /dev/sdb* partition is present, you are dealing with two-disk installation, otherwise, it's one-disk installation. NB! Always check HDD partitions size and available free space! KATA needs a LOT of disk space to work correctly. Most important partitions are: /dev/sda4 1.2T 894G 224G 80% /data ← Used for processing queues and quarantine, main partition for KATA /dev/sdb1 2.7T 1.4T 1.3T 52% /data/var/lib/kaspersky/storage ← Used for EDR data: (telemetry from Endpoint Sensors) Filesystem Size Used Avail Use% Mounted on /dev/sda3 367G 14G 335G 4% / devtmpfs 126G 0 126G 0% /dev tmpfs 126G 252K 126G 1% /dev/shm tmpfs 126G 4.1G 122G 4% /run tmpfs 126G 0 126G 0% /sys/fs/cgroup /dev/sda2 232M 32M 189M 15% /boot /dev/sda1 237M 5.5M 232M 3% /boot/efi /dev/sda4 1.5T 435G 955G 32% /data /dev/sdb1 2.7T 1.4T 1.3T 52% /data/var/lib/kaspersky/storage tmpfs 26G 0 26G 0% /run/user/998 tmpfs 26G 0 26G 0% /run/user/1002 tmpfs 26G 0 26G 0% /run/user/1001 DNS name /environment/hostname.txt File contains exactly the hostname of the machine. kata-cn IP address /environment/ipa.txt /environment/ifconfig.txt Both files contain info about network interfaces and assigned IP addresses. ifconfig command is considered obsolete by community, but it can be useful: it helps to recognize SPAN interfaces. SPAN interfaces usually don't have IP address assigned, but have a lot of traffic. Also, SPAN interfaces always are in promiscuous mode: <UP,BROADCAST,RUNNING,PROMISC,MULTICAST> ipa.txt 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:50:56:9f:0e:77 brd ff:ff:ff:ff:ff:ff inet 10.200.178.85/23 brd 10.200.179.255 scope global ens192 valid_lft forever preferred_lft forever inet6 fe80::250:56ff:fe9f:e77/64 scope link valid_lft forever preferred_lft forever 3: ens224: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:50:56:9f:db:4d brd ff:ff:ff:ff:ff:ff inet6 fe80::250:56ff:fe9f:db4d/64 scope link valid_lft forever preferred_lft forever ifconfig.txt ens192: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 10.200.178.85 netmask 255.255.254.0 broadcast 10.200.179.255 inet6 fe80::250:56ff:fe9f:e77 prefixlen 64 scopeid 0x20<link> ether 00:50:56:9f:0e:77 txqueuelen 1000 (Ethernet) RX packets 604911116 bytes 747444631331 (696.1 GiB) RX errors 0 dropped 26 overruns 0 frame 0 TX packets 368814032 bytes 353073760300 (328.8 GiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens224: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet6 fe80::250:56ff:fe9f:db4d prefixlen 64 scopeid 0x20<link> ether 00:50:56:9f:db:4d txqueuelen 1000 (Ethernet) RX packets 437 bytes 135823 (132.6 KiB) RX errors 0 dropped 1125 overruns 0 frame 0 TX packets 8 bytes 656 (656.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 19418334689 bytes 12053991732736 (10.9 TiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 19418334689 bytes 12053991732736 (10.9 TiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 SPAN interface eno2: flags=4419<UP,BROADCAST,RUNNING,PROMISC,MULTICAST> mtu 1500 inet6 fe80::42f2:e9ff:fecc:4343 prefixlen 64 scopeid 0x20<link> ether 40:f2:e9:cc:43:43 txqueuelen 1000 (Ethernet) RX packets 122540697216 bytes 104768065608116 (95.2 TiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 7 bytes 586 (586.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 device memory 0xbd5a0000-bd5bffff Sandbox server information /config/apt-agents-id Bottom part of the file contains info about connected sandbox nodes: IP addresses, cert fingerprints and states: Sandbox may be connected, but disabled. [sandbox_node.sandbox1] host = 172.16.0.151 enable = yes fingerprint = C0:15:18:C8:11:46:11:BC:23:50:16:95:10:2D:FF:FA:4E:06:21:90:20:AA:CC:36:53:27:B8:BF:CF:5A:1A:9C Enabled integrations(SPAN, ICAP, etc) /config/preprocessor.conf Preprocessor is the component responsible for main KATA integrations: SPAN, SMTP, ICAP, POP3. You should look for corresponding section in preprocessor.conf: SPAN: [traffic] SMTP: [smtp_proxy] ICAP: [icap] POP3: [pop3] For each section, there's a line defining whether this integration is enabled: enable=yes/no Other integrations like KSMG/KLMS/API aren't easy to check by collect script output Only SPAN is enabled [app] use_syslog=no trace_level=ERR cache_socket=localhost:6379 collector_url=http://centralnode:8081/apt/collector license_remote=no #this section applicable for sections: pop3, smtp_proxy and for traffic section but only for smtp preprocessor [mail] extract_urls=yes #file extensions of attachments which format recognizer is not used for file_extensions=dll,exe,com,java,js,jse,wsf,wsh,vbs,vbe,msi,deb,rpm,apk,zip,7z,rar,iso,cab,jar,bz2,gz,tgz,ace,arj,dmg,xsr,rtf,pdf,msg,eml,vsd,vdx,xps,xsn,odt,ods,odp,sxw,doc,dot,docx,docb,dotx,docm,dotm,xls,xlt,xlm,xla,xll,xlw,xlsx,xltx,xlsm,xltm,xlam,xlsb,ppt,pot,pps,ppam,sldx,sldm,thmx,pptx,potx,pptm,potm,ppsx,ppsm,pub,html,htm,hta,swf,jpg,jpeg,gif,png,tiff,chm,mht,cpl,ocx,pif,scr,bat,cmd,ps1,lnk,reg,msu,msp,z [traffic] enable=yes network_interfaces=ens6f0,ens6f1,ens5f1,ens5f0,ens5f3,ens5f2,eno1,ens3f1,ens3f0 pcap_snaplen=1600 pcap_cores= pcap_filter= checksum_validation=no buffer_size_limit=4096 tcp_threads_number=16 enable_dns=yes enable_http=yes enable_ftp=yes enable_ssl=yes enable_smtp=yes ftp_data_expired_timeout_in_seconds=60 ftp_data_supposed_max_size_in_bytes=10485760 [ksn] enable=yes #possible values of type are KSN or KPSN type=KSN timeout=500 non_dl_formats=GeneralHtml,GeneralTxt,ExecutableJs,ImageGif,ImageJpeg,ImagePng,ArchiveCab ksn_adapter_interfaces= # Change cache entries only you know what are doing. # 0 - disables cache cache_entries=3600100 request_threads=4 [snmp] enable=yes master_agent_address=tcp:localhost:705 ping_interval_in_seconds=15 [icap] enable=no listen_interfaces=ens3f3:1344,ens3f2:1344,eno2:1344 allow204=yes max_connections=5000 respmod_url=av/respmod header_client_ip=X-Client-IP header_client_port=X-Client-Port extract_user=no header_username=X-Authenticated-User base64_decode_username=yes [filter] file_size_limit=100000000 dns_lookup_enable=yes dns_timeout=500 html_filter=/var/opt/kaspersky/apt/update/bases/htmlre.txt [snort] enable=yes alerts_socket=/var/log/kaspersky/snort/snort_alert [pop3] enable=no server= port= user= password= cipher_list=ALL:!aNULL:!eNULL:!LOW:!EXP:!MD5:!DSS:!KRB5:!PSK:!RC4:!SRP:!CAMELLIA:!IDEA:!SEED:!3DES:@STRENGTH:!kDH:!kECDH encrypted=yes check_interval_in_seconds=2 accept_any_certificates=no accept_untrusted_self_signed_certificate=yes process_msgs_per_session=3000 request_timeout_in_seconds=60 [smtp_proxy] enable=no max_threads=20 socket_in=inet:10025@127.0.0.1 #RFC 1123 suggests 10 min timeout_in_seconds=600 [stat_engine] enable=yes db=kafka:centralnode:9092?topic=network oltp_bulk_size=1000 subnets= taa_skip_header_proxy_auth=status-code: 407 oltp_raw_data_limit=0 [proxy] enable=no bypass_local_addresses=yes host= port= user= password= Connected Endpoint Sensors /config/aapt_info You can find the beginning of Endpoint Sensors list by searching for 'Agent Status'. To find the number of connected sensors, you need to calculate lines; but it's not easy to automate it as the lines don't have obvious unique grep-able attribute. However, using 'Microsoft Windows' will give you enough precision(it will give a few extra matches from last detections info). Sample entry for 1 agent ae5290b1-c490-404b-beec-ee553d5d64ee | DXB00079395.*.corp | 2019-09-24 08:41:51.579011 | 10.56.14.170 | 3.5.435.0 | 2019-09-23 03:21:26.883616 | 2019-09-24 03:15:28.642816 | t | Microsoft Windows 10 | | | 2346c7a2-a395-4dc4-bc5c-ea99fa488386 | 6 | 568b01b8-4497-decf-7f8c-671bbf8ad8cc KSN/KPSN connection /config/preprocessor.conf From collect script, you can only determine whether KATA is set up to receive verdicts from the cloud, and understand which sort of cloud it is - global KSN or private KPSN. Look for [ksn] section in preprocessor.conf, it's pretty self-explanatory. Keep in mind that you have a tool which allows you to check KSN availability https://forum.kaspersky.com/blogs/entry/86-how-to-check-ksn-availability-on-kata-cn-katakedre/ [ksn] enable=yes #possible values of type are KSN or KPSN type=KSN -
У той или иной локации может быть один, а может быть и несколько IP. Все, кто подключаются к той или иной локации могут иметь один IP, а могут и несколько разных.
-
@IT ARB, добрый день. Этот же момент проверьте: https://forum.kaspersky.com/topic/kes-for-android-50554/#findComment-186705
-
на каждый аккаунт свой ип адрес? или у двух аккаунтов может быть один адрес?
-
Можно ежедневно скачивать новый образ KRD 2025 , в нем будут свежие юазы
-

Regarding the problem of Android malware being terminated after it is elevated.
Flood and Flood's wife replied to jjjhjkhjkhkjh's topic in Kaspersky: Basic, Standard, Plus, Premium
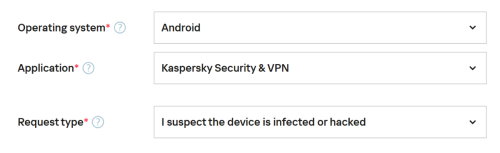
Hello @jjjhjkhjkhkjh, Welcome! Yes, as a *standard* - Kaspersky employs various features to do this, for example: Signature-based detection Behavioral analysis Cloud-based protection (KSN) Real-time protection, However, IF (you) believe (your) phone has been hacked, infected OR manipulated - for a *definitive-answer* to the *generic-question* - please submit a request to Kaspersky Customer Service, https://support.kaspersky.com/b2c/global#contacts - select Email & fill in the template as follows; the KSC Team will work with Kaspersky experts & you to determine the RC of the issue; Kaspersky may request logs, traces & other data, they will guide you: Please share the outcome, with the Community, when it's available? Thank you🙏 Flood🐳+🐋 -
schah joined the community
-
@tistou77 Bonjour, Sans nouvelles bases de données disponibles une MAJ manuelle s'affiche dans les rapports
-
Добрый день, У нас нет услуги динамического\статического IP адреса.
-
Ну а чтоб сервер при каждом новом подключении выдавал адрес, никак?)