All Activity
- Past hour
-
Расширение Касперского для браузера
Лексей replied to SergeiV's topic in Kaspersky: Basic, Standard, Plus, Premium
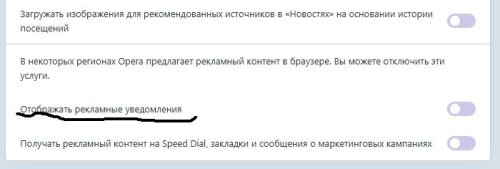
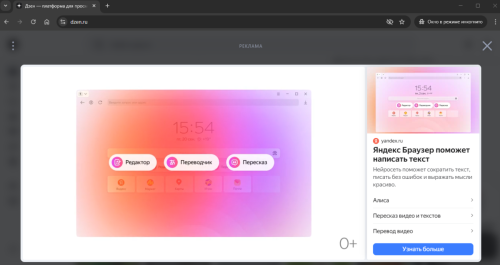
Вспомнил что иногда при входе в почту на mail.ru появляется Но я это предупреждение просто игнорирую и больше оно не появляется Но на дзене нет и такого предупреждения Выходит это действительно Опера - Today
-
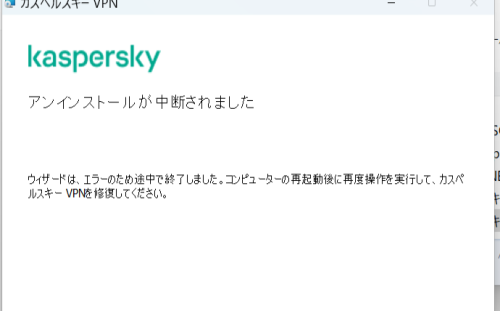
カスペルスキーVPN started following カスペルスキーVPN2024kのソフトには消されておりますが、コントロールパネルのプログラムと機能の中にVPNが入っていて、削除ができない状態になっております。削除中にエラーで止まるのです。
-
カスペルスキーVPN2024kのソフトには消されておりますが、コントロールパネルのプログラムと機能の中にVPNが入っていて、削除ができない状態になっております。削除中にエラーで止まるのです。エラーメッセージを添付を送らせていただきます。 よろしくお願いします。
-
OneinchofAsh started following kaspersky secure connection при включении не пропускает интернет
-
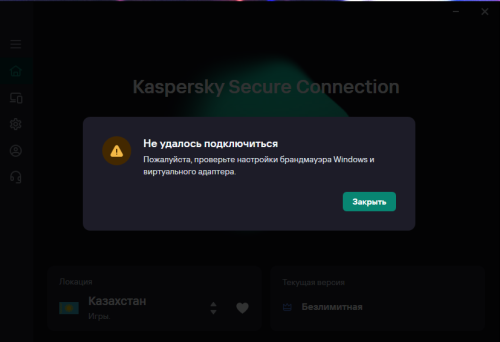
kaspersky secure connection при включении не пропускает интернет
OneinchofAsh replied to kinigos's topic in Kaspersky Secure Connection
Тоже всё работало нормально на ПК, а теперь выдаёт ошибку и ни к одной локации не подключиться. Хотя на смартфоне всё нормально. -
OneinchofAsh joined the community
- Yesterday
-
Statters. started following Whitelist internal web applictaions
-
Whitelist internal web applictaions
Statters. posted a topic in Kaspersky: Basic, Standard, Plus, Premium
Is it possible to whitelist internal web applications from the "Visiting an untrustworthy website has been prevented" function. I have multiple different items on my internal network that have web apps and two of the throw this error when I attempt to load them up. I have added both of their IP addresses to the "trusted addresses" list but they are still blocked. Is there something I'm missing with adding IPs to the "trusted addresses" list or is this not possible? -
Statters. joined the community
-
Hawk54645 started following VPN is preventing printing to network printer
-
VPN is preventing printing to network printer
Hawk54645 replied to Ian M's topic in Kaspersky VPN Secure Connection
I had the same problem, all I did was open the router settings find what's connected and changed the device type to Printer and changed the Hostname to Epson and now its working over VPN enabled -
Hawk54645 joined the community
-
Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
Shmel replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
А есть ли способ узнать явно - срабатывание валидное или ложное? -

Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
harlan4096 replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
-
Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
Shmel replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
кажется, вот отличие. Я не могу управлять значениями в настройках, т.к. это делается централизованно. Но в моем случае в Kaspersky Free включен эвристический анализ, а в KES - нет -

Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
harlan4096 replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
-
Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
Shmel replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
-
ikzuk joined the community
-

Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
andrew75 replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
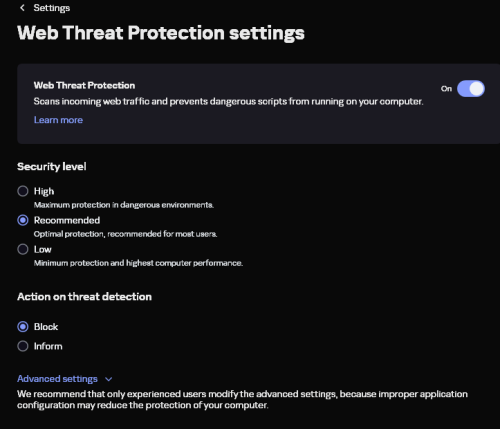
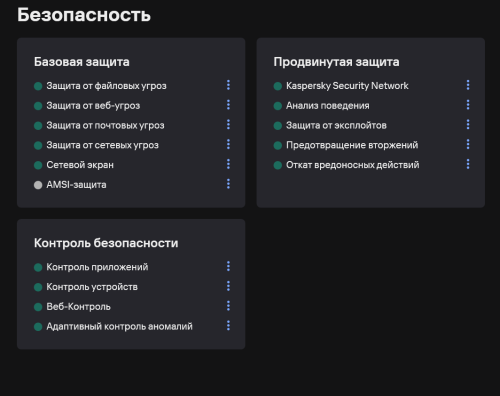
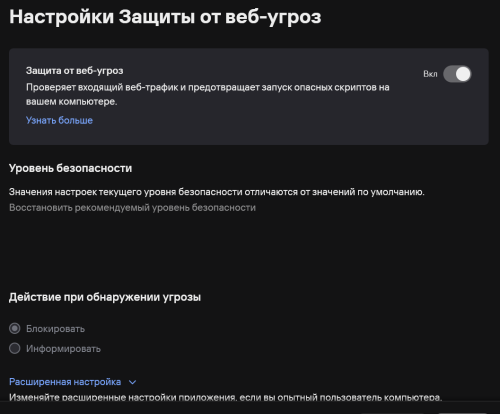
@Shmel, а вы уверены что у вас в KES включена "защита от веб-угроз"? -

Real pool 3d2
harlan4096 replied to Stephen Smith's topic in Kaspersky: Basic, Standard, Plus, Premium
If You exit Kaspersky temporally and run the app, does it work? -
Art28 joined the community
-
harlan4096 started following Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
-

Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
harlan4096 replied to Shmel's topic in Вопросы, связанные с вирусами и шифровальщиками
-
Real pool 3d2
Stephen Smith replied to Stephen Smith's topic in Kaspersky: Basic, Standard, Plus, Premium
- System - Provider [ Name] Application Error [ Guid] {a0e9b465-b939-57d7-b27d-95d8e925ff57} EventID 1000 Version 0 Level 2 Task 100 Opcode 0 Keywords 0x8000000000000000 - TimeCreated [ SystemTime] 2025-07-05T19:22:14.9300472Z EventRecordID 3839 Correlation - Execution [ ProcessID] 18796 [ ThreadID] 18000 Channel Application Computer Stephen - Security [ UserID] S-1-5-21-2088515173-1453250347-40221073-1001 - EventData AppName RealPool3.exe AppVersion 0.0.0.0 AppTimeStamp 68661818 ModuleName RealPool3.exe ModuleVersion 0.0.0.0 ModuleTimeStamp 68661818 ExceptionCode c0000005 FaultingOffset 00000000003d3e8d ProcessId 0x3ab0 ProcessCreationTime 0x1dbeddf0422cf12 AppPath C:\Program Files\WindowsApps\B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a\RealPool3.exe ModulePath C:\Program Files\WindowsApps\B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a\RealPool3.exe IntegratorReportId 8bf50229-c0f0-45f2-91fa-c998105e6b32 PackageFullName B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a PackageRelativeAppId App Another one - System - Provider [ Name] Application Error [ Guid] {a0e9b465-b939-57d7-b27d-95d8e925ff57} EventID 1000 Version 0 Level 2 Task 100 Opcode 0 Keywords 0x8000000000000000 - TimeCreated [ SystemTime] 2025-07-05T19:29:09.5616325Z EventRecordID 3844 Correlation - Execution [ ProcessID] 6808 [ ThreadID] 17340 Channel Application Computer Stephen - Security [ UserID] S-1-5-21-2088515173-1453250347-40221073-1001 - EventData AppName RealPool3.exe AppVersion 0.0.0.0 AppTimeStamp 68661818 ModuleName RealPool3.exe ModuleVersion 0.0.0.0 ModuleTimeStamp 68661818 ExceptionCode c0000005 FaultingOffset 00000000003d3e8d ProcessId 0x898 ProcessCreationTime 0x1dbede25c16f30d AppPath C:\Program Files\WindowsApps\B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a\RealPool3.exe ModulePath C:\Program Files\WindowsApps\B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a\RealPool3.exe IntegratorReportId 5fb598f9-52eb-4716-9b2f-d73ff8c4d838 PackageFullName B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a PackageRelativeAppId App and yet another -
Shmel started following Kaspersky Free и Kaspersky Endpoint Security по-разному реагируют на один и тот же url
-
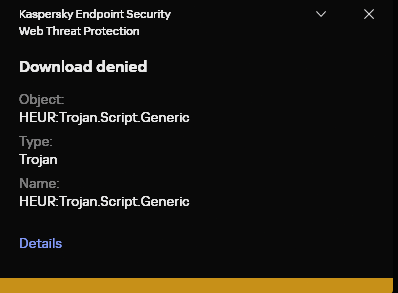
Добрый день, Столкнулся с неоднозначным поведением 2 ваших продуктов касательно одного и того же сайта. Данный url: https://desirefx.me Kaspersky Free - блокирует открытие данного ресурса, ссылаясь на HEUR:Trojan.Script.Generic, но при этом KES открывает молча и без каких-либо оповещений. Я дополнительно проверил сайт на различных платформах, включая Google, Yandex, Dr.Web и другие ресурсы, но только virus total показал нечто подобное. Kaspersky Free - версия 21.21.7.384(a), базы свежие KES - версия 12.9.0.384, базы тоже только сегодня обновлял Подскажите пожалуйста, какому результату можно верить? Заранее спасибо за помощь, с уважением, Кирилл.
-
Расширение Касперского для браузера
Лексей replied to SergeiV's topic in Kaspersky: Basic, Standard, Plus, Premium
Просто мне было непонятно-как это так-у меня судя по журналам антивирей-вообще эти банеры отсутствут а у других... Про Оперу я упустил. Вот это? -
Shmel joined the community
-
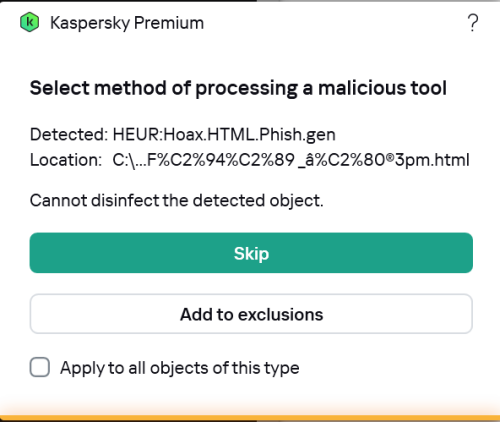
Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
SHOKA replied to SHOKA's topic in Virus and Ransomware related questions
Hi @Berny and @harlan4096, I hovered over the Location: field in the malicious tool pop window, which revealed the full path - it was very long I could not actually copy and paste it for you ( as soon as the mouse pointer stopped hovering the path disappeared). So instead I tried to navigate to the file location through windows explorer, but I could only go so far - it appears that this file is buried withing an outlook email archive that I recently loaded to my computer which I was going to import into my Mozilla Thunderbird email client. It turns out the file was from an alleged voicemail message alert that was sent to me back in 2021. I must have ignored it at the time and not deleted it. So now I know this I will be able to find the email in Thunderbird and delete it. That's pretty good detection on Kaspersky's part - impressive! I understand why Kaspersky premium couldn't disinfect it now. Mystery solved. Thanks very much for your help and pointers. Kind regards, SHOKA -
Real pool 3d2
Stephen Smith replied to Stephen Smith's topic in Kaspersky: Basic, Standard, Plus, Premium
- System - Provider [ Name] Application Error [ Guid] {a0e9b465-b939-57d7-b27d-95d8e925ff57} EventID 1000 Version 0 Level 2 Task 100 Opcode 0 Keywords 0x8000000000000000 - TimeCreated [ SystemTime] 2025-07-05T18:52:24.1025222Z EventRecordID 3830 Correlation - Execution [ ProcessID] 17980 [ ThreadID] 10436 Channel Application Computer Stephen - Security [ UserID] S-1-5-21-2088515173-1453250347-40221073-1001 - EventData AppName RealPool3.exe AppVersion 0.0.0.0 AppTimeStamp 68661818 ModuleName RealPool3.exe ModuleVersion 0.0.0.0 ModuleTimeStamp 68661818 ExceptionCode c0000005 FaultingOffset 00000000003d3e8d ProcessId 0x104c ProcessCreationTime 0x1dbedda84bb5419 AppPath C:\Program Files\WindowsApps\B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a\RealPool3.exe ModulePath C:\Program Files\WindowsApps\B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a\RealPool3.exe IntegratorReportId f8a666fe-0a26-4f06-b15c-2e55075fe652 PackageFullName B9BA84AC.3D2_2.4.3.0_x64__3ag0hv5nd203a PackageRelativeAppId App My IT friend saw the problem with kaspersky. I am not sure how or where to look for that same error I took the first crash event logged now and copied and pasted it here Hope it helps somewhat He also used teamviewer to log into my pc -

Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
harlan4096 replied to SHOKA's topic in Virus and Ransomware related questions
I mean the details of Your K. detection, thanks. -

Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
harlan4096 replied to SHOKA's topic in Virus and Ransomware related questions
Also, please can You go to Report of Your Kaspersky, and copy/paste the details of that detection? We need the full path of detection and other additional details, thanks. -
Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
SHOKA replied to SHOKA's topic in Virus and Ransomware related questions
@Berny Thanks for your help. # ------------------------------- # Malwarebytes AdwCleaner 8.5.1.601 # ------------------------------- # Build: 03-26-2025 # Database: 2025-04-04.3 (Cloud) # ------------------------------- # Mode: Scan # ------------------------------- # Start: 07-05-2025 # Duration: 00:00:23 # OS: Windows 10 (Build 19045.5965) # Scanned: 32094 # Detected: 0 ***** [ Services ] ***** No malicious services found. ***** [ Folders ] ***** No malicious folders found. ***** [ Files ] ***** No malicious files found. ***** [ DLL ] ***** No malicious DLLs found. ***** [ WMI ] ***** No malicious WMI found. ***** [ Shortcuts ] ***** No malicious shortcuts found. ***** [ Tasks ] ***** No malicious tasks found. ***** [ Registry ] ***** No malicious registry entries found. ***** [ Chromium (and derivatives) ] ***** No malicious Chromium entries found. ***** [ Chromium URLs ] ***** No malicious Chromium URLs found. ***** [ Firefox (and derivatives) ] ***** No malicious Firefox entries found. ***** [ Firefox URLs ] ***** No malicious Firefox URLs found. ***** [ Hosts File Entries ] ***** No malicious hosts file entries found. ***** [ Preinstalled Software ] ***** No Preinstalled Software found. ########## EOF - C:\AdwCleaner\Logs\AdwCleaner[S00].txt ########## -
harlan4096 started following Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
-

Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
Berny replied to SHOKA's topic in Virus and Ransomware related questions
@SHOKA Welcome. Please download and run AdwCleaner (*) as ADMIN. Don’t fix eventual detections Please copy/paste the TXT Log in your next post (*) No installation required. -
Berny started following Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
-
SHOKA started following Kaspersky Premium Detected: HEUR:Hoax.HTML.Phish.gen but 'Cannot disinfect the detected object.
-
Please advise what am I supposed to do now. I have the option to Skip and Add to exclusions - but this seems dangerous not knowing what the file is exactly. I don't understand that if Kaspersky thinks this is a malicious tool then why can't it be disinfected (i.e deleted automatically). I'd rather delete it from my system and see if anything breaks, rather than ignore it and forget about it. If anyone has had a similar experience and can advise, I would be very grateful. SHOKA
-
DDDDDDDDD joined the community
-
SHOKA joined the community
-
Douglas Cunha joined the community
-
Cuidado prishing!!! Correo electrónico
Nathaniel replied to Nathaniel's topic in Para usuarios particulares
Lo he recibido por otro email que no es la cuenta que utilizo para Karspersky. No, no he tenido ninguna cuenta más. No te puedo enviar nada en ningún formato, porque lo borré inmediatamente. Gracias por tu interés, pero no he recibido otro email sobre esto. Un abrazo. -
Расширение Касперского для браузера
AlexeyK replied to SergeiV's topic in Kaspersky: Basic, Standard, Plus, Premium