All Activity
- Past hour
-
其实吧 卡巴的虚拟化只给安全支付用 你不用这个功能,完全可以不开启卡巴的虚拟化。 系统自带额credential guard 和VBS 还有内核隔离,更加值得开启。
-

Применимые обновления
durtuno replied to QyzgaldaQ's topic in Kaspersky Endpoint Security для бизнеса
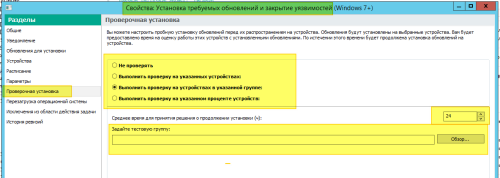
Ну, можно предположить, что речь о распространении на "тестовую группу". Тогда не одобряйте, а используйте отдельную задачу для этой "тестовой группы" - "Установка требуемых обновлений и закрытие уязвимостей", где в укажите, что можно устанавливать без одобрения (кстати, в этой же задаче имеется и отложенная установка): -
Применимые обновления
Friend replied to QyzgaldaQ's topic in Kaspersky Endpoint Security для бизнеса
Почему же? Можно создать запрос в поддержку и попросить рассмотреть возможность добавить того или иного ПО для обновления с аргументами. А там рассмотрят и решат: добавить или нет, но процесс не быстрый и итог неизвестный. Пока только видел обратный процесс, некоторые разработчики софта попросили исключить их из этого списка, так как автообновление у них работает лучше, чем это делает антивирус. -
Так и сделал. Спасибо
-
Михаил Пономарев joined the community
-
Применимые обновления
QyzgaldaQ replied to QyzgaldaQ's topic in Kaspersky Endpoint Security для бизнеса
к примеру вышел KES 12.10 при одобрении этого обновления начинается установка на всех устройствах, как изменить это поведение -

Применимые обновления
durtuno replied to QyzgaldaQ's topic in Kaspersky Endpoint Security для бизнеса
Что именно настроить? Сам использую отдельную задачу для обновления того или иного стороннего ПО. Т.е., не всё поддерживаемое "Kaspersky Lab" стороннее ПО одобряю, т.к. некоторое стороннее ПО поддерживаю/ обновляю отдельными задачами, с указанием параметров установки/ обновления. -
Применимые обновления
QyzgaldaQ replied to QyzgaldaQ's topic in Kaspersky Endpoint Security для бизнеса
Спасибо) Ещё такой вопрос, при одобрении обновлений KES запускается массовое обновление, это как то можно настроить? -

Применимые обновления
durtuno replied to QyzgaldaQ's topic in Kaspersky Endpoint Security для бизнеса
Это результат работы задачи "Поиск уязвимостей и требуемых обновлений". Не возможно. Имеется некоторый список стороннего ПО поддерживаемого "Kaspersky". Просмотр информации о доступных обновлениях приложений сторонних производителей. О приложениях сторонних производителей -
Как локализация операционной системы, сервера, консоли и плагинов управления влияет на язык интерфейса Консоли администрирования Kaspersky Security Center Как вариант используйте удалённую MMC-консоль с необходимой локализацией.
-
Sometimes, KATA Sandbox may suddenly stop functioning normally and throw a self-diagnostic error. This may be caused by snapshots corruption: as one of the troubleshooting steps, you may remove the latest VM snapshots, this is harmless procedure. Step-by-step guide Login to Sandbox via SSH and execute the following command: ls -l /vm/qemu/vms/ total 36 drwxrwx---+ 3 sandbox-core klusers 4096 Apr 19 16:42 Win10_x64-1555680939 //This is the folder with original VM image drwxrwxr--+ 6 sandbox-core klusers 4096 Apr 22 00:17 Win10_x64-1555680939_2019.04.22.1555880403 //This is a folder with VM snapshot drwxrwxr--+ 6 sandbox-core klusers 4096 Apr 23 00:18 Win10_x64-1555680939_2019.04.23.1555966815 //This is a folder with VM snapshot drwxrwx---+ 3 sandbox-core klusers 4096 Apr 19 16:34 Win7_x64-1555680478 //This is the folder with original VM image drwxrwxr--+ 6 sandbox-core klusers 4096 Apr 22 00:09 Win7_x64-1555680478_2019.04.22.1555880403 //This is a folder with VM snapshot drwxrwxr--+ 6 sandbox-core klusers 4096 Apr 23 00:11 Win7_x64-1555680478_2019.04.23.1555966815 //This is a folder with VM snapshot drwxrwx---+ 3 sandbox-core klusers 4096 Apr 19 16:27 WinXP-1555680293 //This is the folder with original VM image drwxrwxr--+ 5 sandbox-core klusers 4096 Apr 22 00:07 WinXP-1555680293_2019.04.22.1555880403 //This is a folder with VM snapshot drwxrwxr--+ 5 sandbox-core klusers 4096 Apr 23 00:08 WinXP-1555680293_2019.04.23.1555966815 //This is a folder with VM snapshot Remove the latest snapshots by date and restart the following services - KATA 3.7.2 : service sandbox-komilfo restart service sandbox-create-snapshot restart For KATA 4.0/4.1/5.0 - restart Sandbox
-
Security officers may need raw alerts data from KATA for further processing in Excel/etc. Here's how to export all alerts from KATA database to .csv file: KATA 3.7.2 sudo -u postgres bash -c "psql -d antiapt -c \"COPY (SELECT * FROM all_alerts) TO '/tmp/kata_alerts.csv' (format csv, delimiter ';', header, encoding 'UTF8');\"" Instead of simply copying all alerts, administrator may export only last N alerts, or play around with SQL queries: sudo -u postgres psql antiapt -c "copy (select * from all_alerts limit N) to '/tmp/test_oneliner1.csv' (format csv, header, encoding 'UTF8');" For example, if a specific time interval is required, it can be done like this: sudo -u postgres bash -c "psql -d antiapt -c \"COPY (SELECT * FROM all_alerts WHERE update_time BETWEEN '2021-04-19 21:36:11'::timestamp AND '2021-05-01 13:29:57'::timestamp) TO '/tmp/kata_alerts.csv' (format csv, delimiter ';', header, encoding 'UTF8');\"" NB! Sometimes, filenames may have \r\n EOL symbols, which may affect CSV import to Excel. You can change \r\n to \n via Notepad++ or any other text processor. P.S. To export all connected/not connected endpoints you can execute: sudo -u postgres bash -c "psql -d antiapt -c \"COPY (SELECT * FROM agent_status) TO '/tmp/agent_status.csv' (format csv, delimiter ';', header, encoding 'UTF8');\"" KATA 4+/5+/6+ If the command above doesn't work or hangs, use the command below: psql -U kluser -h 127.0.0.1 antiapt -c "select * from all_alerts;" > /tmp/all_alerts Similar to previous, you can spice up the query to your taste, for example, to get time interval between now and then, execute: psql -U kluser -h 127.0.0.1 antiapt -c "select * from all_alerts where update_time between '2021-04-19 21:36:11'::timestamp and now()::timestamp;" > /tmp/all_alerts Then just open Excel and make import from Data -> From Text/CSV from /tmp/all_alerts (download it to local computer first).
-
Problem The error message Downloading the distribution package of the device security application. Failed to download the distribution package of the device security application is displayed in the browser after following a new invitation link on the iOS device. Solution Make sure that The new invitation link is used. KESCloud invitation links are one-time-use only on mobile devices. Send the new link. The APNs certificate is added to KESCloud console. Login to KESCloud and open the workspace. Switch to the Getting started tab and scroll down to the Recommended section. See if APNs certificate is added and valid. Create or Renew certificate if needed.
-
Scenario In certain cases one may need to move an SQL database that stores KSE operational data to another SQL server/instance. The following procedure can be used to achieve that: Step-by-step guide Change the startup type of KSE services to Manual. Stop the KSE services which use this database (may be located on several hosts in case of DAG, for example). Create a backup of the KSE database using MS SQL tools. Restore the database on a new SQL server/instance using MS SQL tools. Assign the required rights for this database according to this article. Manually edit the file BackendDatabaseConfiguration*.config on every KSE server that will use this database. See this article for instructions. In the scenario when KSE doesn't use the DB default port, we must edit the BackendDatabaseConfiguration*.config file properly, here is an example when custom port is 1435: <SqlServerName>sqlag02ls,1435</SqlServerName> Manually change the values of BackendDatabaseName and BackendSqlServerName with the new ones in the registry key "HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Kaspersky Lab\Kaspersky Security for Microsoft Exchange Server" on every KSE server that will use this new database. Return the startup type for the KSE services back to original values. Start the KSE services. Verify that there are no errors in event logs after the service will be started.
-
KES11 audio or video is blocked in messengers [KES for Windows]
svc_kms posted a blog entry in Kaspersky Endpoint Security's KES for Windows
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This article is about Kaspersky Endpoint Security for Windows (KES for Windows) Problem HIPS (Host Intrusion Prevention System) unexpectedly blocks data stream (audio, video) in trusted communication software such as MS Teams, Skype, Skype for Business etc. Solution The root cause is in KUsrInit.exe (parent process for many processes in the OS where it exists) which in some cases can be found on pre-installed OS on Dell computers. KUsrInit.exe process must be added to HIPS trusted as well to avoid such issue. -
How to use FQDN as a display name [KSC for Windows]
svc_kms posted a blog entry in Kaspersky Security Center's Kaspersky Security Center Community
There is a known limitation in KSC. When hosts are managed from different domains and there are hosts with the similar names in these domains then 'doubles' will appear. To avoid this, use FQDN (fully qualified domain name) as a display name instead of NETBIOS name. Step-by-step guide Set up the following server flag: SrvUseFqdnAsDisplayNames [HKEY_LOCAL_MACHINE\SOFTWARE\KasperskyLab\Components\34\1093\1.0.0.0\ServerFlags] "SrvUseFqdnAsDisplayNames"=dword:00000001 2. Delete duplicated hosts from managed group and from unassigned devices. 3. Run polling so that hosts reappear on KSC. In order for hosts to reappear with an FQDN name, the KSC must know their DNS domain. This information appears on the KSC from an installed network agent or AD scan. Therefore, a network agent must be installed on these hosts or AD polling must be used. -
Problem You install latest Windows Assessment and Deployment Kit (Windows ADK) on the server where KSC is installed, but KSC console still shows message "to deploy OS images, you must install the Windows Assessment and Deployment Kit (Windows ADK) on the device that has KSC installed". Solution KSC doesn't see all the needed WADK components being installed. Because Microsoft is always changing components within their installation packages, we recommend to install all utilities from the Microsoft's official article. Go to https://docs.microsoft.com/en-us/windows-hardware/get-started/adk-install Download all utilities under "The Windows ADK includes:" including WinPE and WSIM.
-
The ability to modify the ciphers used by the product to communicate with port 13292 published on the Internet is required. Step-by-step guide You cannot change the ciphers used on a particular port, but you can change the cipher modes used by the MDM server on all listening ports.To do so, you will need to create a global variable KLTR_ENV_SSL_CIPHER_SUITE and restart Kaspersky Security Center server. You can familiarize yourself with the format of the values at this link https://www.openssl.org/docs/man1.0.2/man1/openssl-ciphers.html For example, a variable might look like the following: KLTR_ENV_SSL_CIPHER_SUITE=HIGH:!MD5:!DSS
-
Sometimes, you may need to check KSN servers availability and operation on KATA CN. This method is not applicable to KATA 6.0. The tool is still present, but it returns error 0x80000001 (Interface not supported). For KSN issues, there's a way to check specific hash for reputation: Become root sudo -i Check specific hash for reputation by running the following command: for KATA 4.+ and 5.0: docker exec -it "$(docker ps | grep ksn_proxy| awk '{print $1}')" /opt/kaspersky/apt-ksn_proxy/sbin/ksn_client --ip 127.0.0.1 --hash 9C642C5B111EE85A6BCCFFC7AF896A51 for KATA 5.1 and 6.1: docker exec -it "$(docker ps | grep ksn_proxy| awk '{print $1}')" /opt/kaspersky/apt-ksn_proxy/sbin/ksn_client --ip 127.0.0.1 --hash 9C642C5B111EE85A6BCCFFC7AF896A51 UnTrusted - means that KSN working properly.
-
Scenario Backup task fails indicating corrupted files. Specific file names may vary. The following error appears in Kaspersky Event Log (file name may vary): Database is corrupted. At least one repository corrupted C:\ProgramData\Application Data\KasperskyLab\adminkit\1093\gsyn\klsdata.dat has been corrupted and will not be recovered. Hardware fixing and application reinstallation are required. Possible root causes The most common reasons are OS crash and unexpected reboot (for example due to power loss) of the system with disk caching is enabled. It leads to corruption of KSC repositories. Solution Uninstall KSC Install KSC Restore from the latest backup How to avoid the issue Ensure the system is stable, prevent power outages. You may also check System event log for the large number of any warnings, such as events 50 or 140. These events may be a sign of a file system problem. If NTFS events such as Event ID 55, 50, 140, and 98 are logged, Microsoft suggests running the "chkdsk" utility. Because NTFS couldn't write data to the transaction log, this could affect the ability of NTFS to stop or roll back the operations in which the transaction data couldn't be written: https://learn.microsoft.com/en-us/troubleshoot/windows-server/backup-and-storage/troubleshoot-data-corruption-and-disk-errors#troubleshooting-event-id-55-and-98.
-
Problem Error Failed to get IP addresses for connecting to SVM appears during SVM deployment. Solution To troubleshoot this problem, you need to follow our step-by-step guide: I. Disable SVM rollback Go to C:\Program Files (x86)\Kaspersky Lab\Kaspersky VIIS Console\ for KSV LA 5.1 or to C:\Program Files (x86)\Kaspersky Lab\Kaspersky VIISLA Console for KSV LA 5.2 Edit the Kaspersky.VIISConsole.UI.exe.config file Uncomment <!--<add key="disableRollback" value="1" />--> (delete <!-- and-->) Save changes II. Enable VIIS traces Go to C:\Program Files (x86)\Kaspersky Lab\Kaspersky VIIS\ for KSV LA 5.1 or to C:\Program Files (x86)\Kaspersky Lab\Kaspersky VIISLA for KSV LA 5.2 Open NLog.config file in a text editor Find the line <logger name="*" minlevel="Info" writeTo="file"/> and change minlevel value from Info to Trace Save changes III. Enable extended logging of deployment wizard Go to C:\Program Files (x86)\Kaspersky Lab\Kaspersky VIIS Console\ for KSV LA 5.1 or to C:\Program Files (x86)\Kaspersky Lab\Kaspersky VIISLA Console for KSV LA 5.2 Open NLog.config file in a text editor Find the line <logger name="Kaspersky.Virtualization*" minlevel="Info" writeTo="DeployWizardLog" final="true"/> and change minlevel value from Info to Trace for KSV LA 5.1 and <logger name="DeployWizardFileLogger" minlevel="trace" writeTo="DeployWizardLog" final="true"/> and change minlevel value from off to Trace for KSV LA 5.2 Save changes IV. Start troubleshooting Start SVM deploying wizard and don’t forget to enable option Allow remote access via SSH for root account. Wait for the error and then, make sure that deployment wizard skipped rollback step. Disable all traces returning to the previous values. Connect to SVM directly, using hypervisor. Login to SVM OS under the root account, using default password 7czWtTKhCgrvEYBHb3rE This password can be applied only during troubleshooting process with disabling SVM rollback and it wouldn't work with normally deployed SVMs. Use command ifconfig to check if the SVM received network adapter settings, specified at the beginning of installation. Try to establish connection by SSH from KSC (where VIIS installed) to the SVM. If SSH connection fails, then there are no issues with Kaspersky product. You should configure the environment according to our system requirements. Especially, at the side of ports accessibility. Configuring ports used by the application If the SSH connection established successfully, please collect the following data and send it to Kaspersky Support: Data to be collected Screenshot of network settings that has been applied to the SVM VIIS log from - C:\ProgramData\Kaspersky Lab\VIIS\logs for LA 5.1 and C:\ProgramData\Kaspersky Lab\VIISLA\logs\ for LA 5.2 Deployment wizard detailed log from - C:\Users\<Account>\AppData\Local\Kaspersky_Lab\ViisConsole for LA 5.1 and C:\Users\<Account>\AppData\Local\Kaspersky Lab\Kaspersky VIISLA Console\logs\ for LA 5.2 /var/log/ – from SVM /var/opt/– from SVM
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This article is about Kaspersky Endpoint Security for Windows (KES for Windows) This article covering the specific effect brought by any PF installation for the following versions: KES 11 and higher Private fix installation on host with KES has a side effect: the HIPS (Host Intrusion Prevention System) configuration will be reset back to defaults and, since Firewall is the part of it, will also restore the network packet and application rules back to their original state. This is done intentionally to prevent storing in local KES cache outdated rules and synchronization issues, which is happening with product from time to time and causing strange and unexpected behavior of the product. In most cases, this is not crucial, because as long as endpoint managed by Network Agent and KSC, it will reload all settings from the defined policy. But, if KES installed as standalone endpoint and managed via GUI, it is completely expected that no Firewall or HIPS settings will be saved after reboot, so for such configurations it is recommended to have a backup .cfg file.
-
Patch Management FAQ [KSC for Windows]
svc_kms posted a blog entry in Kaspersky Security Center's Kaspersky Security Center Community
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. If you open KSC -> Advanced -> Application management -> Software Updates, there is a column Not assigned for installation (new version). Some computers may have this status or Not assigned for installation status. What does it mean? Installation status Not assigned for installation means that the update is applicable for this host (as a minor upgrade), but there is no patch management tasks for this host having an appropriate rule to install this update (update doesn't match any rule in any patch management task for this host). Column Not assigned for installation means number of computers having installation status Not assigned for installation. Installation status Not assigned for installation (new version) means that the update is applicable for this host (as a major upgrade - new version), but there is no patch management tasks for this host having an appropriate rule to install this update (update doesn't match any rule in any patch management task for this host). Column Not assigned for installation (new version) means number of computers having installation status Not assigned for installation (new version). Some computers have in Installation status Not assigned for installation. Should anything be done? Yes. Such updates should be analyzed, and if they should be installed, the administrator should decide, why it should be installed, and why it is not yes assigned for installation by any patch management task. if there is no patch management task at all, it must be created, etc. if this update should be installed because it fixes a vulnerability, then probably existing patch management tasks should have a rule to install all patches which fix vulnerabilities having certain vulnerability rating (such rule to install all updates fixing Critical vulnerabilities is created in default patch management task); if existing patch management task have a rule to install all manually approved updates (such rule is also created by default in default patch management task), then this update should be approved by administrator (the update approval state should be changed to Approved); if this update is a MS update of types Critical Update or Security Update, then it should also be installed by default and such rule should be created for a task (such rule is also created by default in the default patch management task by QSW); if you want to install, e.g., all patches for Java, or all updates published by "Adobe", appropriate rules also can be created, etc; by default, major updates (which increase major version) are not installed automatically; if you want to install major upgrades as well, the appropriate option should be set in the task properties; if major upgrades should be allowed for certain rules only (e.g., for Java updates or critical vulnerabilities fixes only), an additional patch management task should be created with appropriate rules and the option should to install major upgrades should be set for this task; the most inefficient way is to add certain updates to a rule with a direct list of updates to be installed; in certain test or emergency cases for small amount of updates such way can also be used, but in general it's better to use categorial rules (like mentioned above), and in case of updates not matching any common rules use the "approvement" mechanism (when having the default rule to install all "approved" updates). How to update all of the software in Software Updates for the clients? In this rare case a patch management task in the root administration group should exist, and it should have a rule allowing to install any applicable updates (except having "denied" approval state). -
Problem On Windows 10 v1903 and Windows Server v1903 after applying GPO Enable svchost.exe mitigation options, in System\Service Control Manager Settings\Security Settings, high CPU consumption by the following processes may be observed (avp.exe, klnagent.exe, kavfs.exe, kavfswp.exe). When checking if any resource consuming tasks are running, there are no ODS tasks running in KES or KSWS and no patch management related tasks are running too. This is happening because MS security configuration baselines recommendations had a suggestion to enable this option and this policy was applied to the host. This policy setting enables process mitigation options on svchost.exe processes. If you enable this policy setting, built-in system services hosted in svchost.exe processes will have stricter security policies enabled on them. This includes a policy requiring all binaries loaded in these processes to be signed by Microsoft, as well as a policy disallowing dynamically-generated code. https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-servicecontrolmanager Solution Microsoft has removed it from security baseline. MS have updated their Windows 10 v1903 and Windows Server v1903 security configuration baseline recommendations to address some issues: The first and most important change is that we are removing the Computer Configuration setting, “Enable svchost.exe mitigation options” (in System\Service Control Manager Settings\Security Settings) from the Windows 10 and Windows Server baselines at this time because of reports that in its current implementation it causes more compatibility issues than we had anticipated. https://techcommunity.microsoft.com/t5/Microsoft-Security-Baselines/Security-baseline-Sept2019Update-for-Windows-10-v1903-and/ba-p/890940
-
For KATA 3.7.2 You can force run Sandbox Healthcheck instead of waiting for 30 minutes' timeout. Step-by-step guide Log into Sandbox Server via ssh. To run checker, first you need to delete /var/tmp/sbtest file: rm /var/tmp/sbtest Then run checker and wait until it finishes: /bin/su -c 'exec /opt/kaspersky/sandbox/libexec/utilities/checker.py -l /var/log/kaspersky/sandbox/checker/checker.log' -s /bin/sh kluser Then on Central Node server run update_sandbox_status.py script: sudo -u kluser flock -w 1 /tmp/health_status_sandbox.lock python -B /opt/kaspersky/apt-base/libexec/health_status/update_sandbox_status.py For KATA 4+ / 5+ On Central Node under root execute: docker exec $(docker ps -q --filter name=kata_scanner) supervisorctl start update_sandbox_status And after command's execution wait for 10-15 minutes and gather from SB file /var/tmp/sbtest (for Kaspersky support just in case).
-
FDE implementation best practices [KES for Windows]
svc_kms posted a blog entry in Kaspersky Endpoint Security's KES for Windows
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This article is about Kaspersky Endpoint Security for Windows (KES for Windows) This is a rough guide for testing FDE prior to implementation in production. Make sure that the encrypted hosts will be serviced by a healthy KSC infrastructure (backups are performed regularly, no errors in Kaspersky Event log that need to be addressed, healthy database with plenty room for growth, no cloned hosts, etc.). Create a scope of devices for FDE testing, that will consist of devices representing most widespread hardware & software configurations that is used in the enterprise infrastructure. Devices should have default firmware settings configured on them. Attach to the test devices as much peripheral devices as possible (most widespread configurations that is likely to be attached to encrypted devices during its regular usage) USB headsets, dongles, external flash drives, tokens, card-readers, etc... Run current FDE precheck version on the test devices. Analyze the precheck's output. In case of errors, handle each of them individually. After addressing them all, proceed to the next step. Prior to starting full disk encryption, you are advised to make sure that the computer is not infected. To do so, start the Full Scan or Critical Areas Scan task. Performing full disk encryption on a computer that is infected by a rootkit may cause the computer to become inoperable. Ensure that disk is healthy. Corrupted disk may cause the computer to become inoperable. Deploy FDE and encrypt devices using actual KES version on a limited scope of test devices in production. Monitor the user experience on the test devices in actual production environment during the pilot testing period. Prohibit the end-users to adjust firmware setting on the hosts with encryption, prior to deploying FDE to production on the whole set of devices, by setting a BIOS password, for example. Deploy FDE to production.