All Activity
- Past hour
-
svc_kms started following Trusted Applications [KES for Mac] , Trusted Applications [KES for Mac] , KWTS Kerberos LDAP, SSO, Proxy authentication problems [Kaspersky Web Traffic Security] and 7 others
-
Trusted Applications [KES for Mac]
svc_kms posted a blog entry in Kaspersky Endpoint Security's KES for Windows
The KESMac 12 and the KESMac 11.3 patch C allows adding particular processes into the trusted section named Trusted Applications. The both filesystem and network activity of which can be ignored by the product increasing performance. Please, however, note that this could be potentially risky. https://support.kaspersky.com/KESMac/11.3_adminguide/en-US/194142.htm Problem This article will describe a few ways to configure KES for Mac to exclude some of the software from the scope of the product. Solution Trusted applications In order to have an ability to exсlude an application from scanning with KES, a function of Trusted Applications available in Kaspersky Endpoint Security for Mac can be used: The Trusted applications section as seen in the policy creation wizard. Naturally, it can be configured later by modifying the policy. Update the plugin to at least version 11.3.0.33 to get the new functionality. In some specific cases it might be required to put several binaries to Trusted Applications simultaneously in order to take effect. So, a final solution might include several path-based exclusions accompanied by a few BundleID-based ones. Trusted Applications are only available for configuration via KSC policy; i.e. it is currently impossible to add application to exclusions having no KSC installed. Additionally, an appropriate application control plug-in for KESMac must be downloaded and installed on the KSC prior to using Trusted Application functionality. It can be found on the corresponding download page. Common exclusions for developers It's suggested excluding the following paths: "/Library/Developer/CommandLineTools" and "/Library/Toolchains" for the standard developers' utilities, as well as the "/Applications/Xcode.app/*" for the XCode. At the same time, in case you use alternative tools, contact Kaspersky Support to get the exact paths for further exclusions. Excluding TCP 443 from port monitoring Additionally, in case of HTTPS-connectivity issues, unchecking port 443 in Monitored ports may also help: -
Introduction Often problems with Kerberos are difficult to diagnose but they occur if you're deploying KWTS for the first time. There are three functional places in the product where Kerberos authentication can be used: Proxy authentication This is needed for users to authenticate on the proxy server automatically without login prompt. If login prompt pops-up, then Kerberos authentication failed. LDAP authentication This is needed for KWTS to synchronize LDAP cache with LDAP servers (simply put - with domain controllers). This cache is used in Rules creation and if KWTS has user login information for a given session supplied by proxy server, then traffic can be matched against those Rules that are defined by groups in AD for example. SSO This is needed to authenticate users on KWTS web administration console itself. SSO works only for one domain, as it is for KSMG as well. Check the documentation https://support.kaspersky.com/KWTS/6.1/en-US/166491.htm Read Kerberos and LDAP parts. Terminology FQDN - https://en.wikipedia.org/wiki/Fully_qualified_domain_name . In our use cases looks like: kwts.example.com SPN - Unique ID of the service in the network for authentication over the Kerberos protocol. In our use cases looks like: HTTP/<FQDN>@<realm Active Directory service in the upper case> or HTTP/*****@*****.tld Creating keytabs for multiple nodes For LDAP, SSO and Proxy authentication you need to create two keytabs: Keytab For LDAP without SPN Keytab for SSO and Proxy with SPN In this example there are two servers in cluster kwts1.example.com and kwts2.example.com and Realm (Domain) is EXAMPLE.COM. Please bear in mind that hostname of KWTS node in OS MUST be in lower-case. If it's in upper-case change hostname via command hostnamectl set-hostname kwts1.example.com First you remove any existing kwts users from AD and create new ones *****@*****.tld and *****@*****.tld Then for LDAP you don't need SPN, so create LDAP keytab like so (replace <password> with user password): ktpass.exe /crypto AES256-SHA1 /ptype KRB5_NT_PRINCIPAL /out C:\kwts-ldap.keytab /princ kwts-ldap-user@EXAMPLE.COM /pass <password> You can now add C:\kwts-ldap.keytab to LDAP settings and force LDAP synchronization. For SSO and Proxy authentication you then create a first keytab like so (do not use upper case letters in FQDN part kwts1.example.com/kwts2.example.com of SPN, this will not work for SSO): ktpass.exe -princ HTTP/kwts1.example.com@EXAMPLE.COM -mapuser kwts-control-user@EXAMPLE.COM -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass <password> -out C:\kwts-control-1.keytab Then using this keytab you create a new keytab with a second record in it: ktpass.exe -princ HTTP/kwts2.example.com@EXAMPLE.COM -mapuser kwts-control-user@EXAMPLE.COM -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass <password> -in C:\kwts-control-1.keytab -out C:\kwts-control-2.keytab -setupn -setpass If there are more servers, then please add more entries in the same manner. You can now add C:\kwts-control-2.keytab to SSO settings. When testing SSO you should use https://kwts1.example.com and https://kwts2.example.com URLs, not IP. If you are asked for credentials then it means that SSO doesn't work. For SSO on Internet Explorer and Chrome it is important that https://kwts1.example.com and https://kwts2.example.com are added to Local Intranet zones in IE settings (refer to https://support.kaspersky.com/ksmg/228052 - article is for KSMG, but fully applicable to KWTS as well): Open Internet Explorer and click the Settings gear icon in the top-right corner. Select Internet options. Select the Security tab. Select the Local Intranet zone and click the Sites button. Make sure that the first two options, Include all local (intranet) sites not listed in other zones and Include all sites that bypass the proxy server are checked. Click Advanced and add the KWTS addresses, one at a time, to the list of websites. In this example add https://kwts1.example.com and https://kwts2.example.com. Click Close. Click OK to save your configuration changes. For Firefox: Open the low level Firefox configuration page by loading the about:config page. In the Search text box, enter: network.negotiate-auth.trusted-uris Double-click the network.negotiate-auth.trusted-uris preference and enter KWTS address. Separate multiple addresses with a comma. Click OK. Now, if SSO works fine you can add the same C:\kwts-control-2.keytab to Proxy authentication settings and test it. When testing proxy authentication make sure proxy address in browser settings is set to kwts1.example.com or kwts2.example.com. IP address will not work. Creating SSO/Proxy keytabs for two domains (or more) for two nodes and a balancer Users from *both* domains must connect to KWTS via proxy1-kwts.firstdomain.ru FQDN, this is not optional. On domain controller of FIRSTDOMAIN.RU (user: control-user-domain1): C:\Windows\system32\ktpass.exe -princ HTTP/proxy1-kwts.firstdomain.ru@FIRSTDOMAIN.RU -mapuser control-user-domain1@FIRSTDOMAIN.RU -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass password1 +dumpsalt -out c:\Temp\1.keytab Assuming we've got salt "FIRSTDOMAIN.RUHTTPproxy1-kwts.firstdomain.ru" (salt usually consists of DOMAIN + HTTP + fqdn string, it is case sensitive, and doesn't change in the scope of a single user) C:\Windows\system32\ktpass.exe -princ HTTP/proxy2-kwts.firstdomain.ru@FIRSTDOMAIN.RU -mapuser control-user-domain1@FIRSTDOMAIN.RU -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass password1 -in c:\Temp\1.keytab -out c:\Temp\2.keytab -setupn -setpass -rawsalt "FIRSTDOMAIN.RUHTTPproxy1-kwts.firstdomain.ru" C:\Windows\system32\ktpass.exe -princ HTTP/balancer-kwts.firstdomain.ru@FIRSTDOMAIN.RU -mapuser control-user-domain1@FIRSTDOMAIN.RU -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass password1 -in c:\Temp\2.keytab -out c:\Temp\3.keytab -setupn -setpass -rawsalt "FIRSTDOMAIN.RUHTTPproxy1-kwts.firstdomain.ru" On domain controller of SECONDDOMAIN.RU (user: control-user-domain2): Copy c:\Temp\3.keytab from FIRSTDOMAIN.RU domain controller to c:\Temp\3.keytab on SECONDDOMAIN.RU domain controller C:\Windows\system32\ktpass.exe -princ HTTP/proxy1-kwts.firstdomain.ru@SECONDDOMAIN.RU -mapuser control-user-domain2@SECONDDOMAIN.RU -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass password2 +dumpsalt -in c:\Temp\3.keytab -out c:\Temp\4.keytab Assuming we've got salt "SECONDDOMAIN.RUHTTPproxy1-kwts.firstdomain.ru". C:\Windows\system32\ktpass.exe -princ HTTP/proxy2-kwts.firstdomain.ru@SECONDDOMAIN.RU -mapuser control-user-domain2@SECONDDOMAIN.RU -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass password2 -in c:\Temp\4.keytab -out c:\Temp\5.keytab -setupn -setpass -rawsalt "SECONDDOMAIN.RUHTTPproxy1-kwts.firstdomain.ru" C:\Windows\system32\ktpass.exe -princ HTTP/balancer-kwts.firstdomain.ru@SECONDDOMAIN.RU -mapuser control-user-domain2@SECONDDOMAIN.RU -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -pass password2 -in c:\Temp\5.keytab -out c:\Temp\6.keytab -setupn -setpass -rawsalt "SECONDDOMAIN.RUHTTPproxy1-kwts.firstdomain.ru" Apply 6.keytab in SSO and Built-in proxy kerberos authentication settings. Notable differences and restrictions in Kerberos keytab requirements For Proxy and SSO authentication FQDN that is specified in keytab must always match the real and used FQDN. For Proxy authentication the address that is used in browser proxy settings MUST match the FQDN in keytab. For SSO, the address in the address bar in the browser that is used to access KWTS web interface MUST match the FQDN in the keytab and MUST match the real FQDN of KWTS and FQDN that is configured in OS. But for LDAP the FQDN in keytab SPN should just have valid records in DNS including PTR record. It is also not necessary for LDAP keytab to have an SPN at all while you must have it for Proxy and SSO; For LDAP authentication it is not possible to have multiple SPN entries in keytab. But in case of Proxy and SSO authentication you can create multiple entries. However for LDAP it is not needed (see 1); You cannot have SPN duplicates in the same domain. Meaning that you can't create two different keytabs that have duplicate SPN (which includes FQDN), you must not have SPN duplicates with different mapped users; User which was used to create keytab must contain only latin characters in Distinguished Name, so in the entire path to the user in AD there must not have Cyrillic or other characters. To sum up usually you must create two keytabs: For Proxy and SSO that have all the SPNs with all FQDNs of proxy and secondary nodes (to which fallback if control node fails); For LDAP that doesn't have an SPN or has one that just has an FQDN with valid DNS records but is not duplicate to any SPN in 1. How KWTS connects to LDAP servers using keytab There is no ldap server address configuration in KWTS. It takes the REALM (Domain) from keytab, for example EXAMPLE.COM, then the following DNS requests of type SRV are sent: _ldap._tcp.example.com _kerberos._tcp.example.com In KWTS console such requests can be reproduced with dig srv _ldap._tcp.example.com dig srv _kerberos._tcp.example.com There you will see a list of domain controllers, ports, weighs and priorities. For more information on SRV records see https://en.wikipedia.org/wiki/SRV_record LDAP servers are listed in _ldap._tcp.example.com , default port 389. _kerberos._tcp.example.com is needed for Kerberos, default port 88. Connection is tried to each one from the list (one at a time, with a timeout) until a it is successfully established or the list is exhausted. LDAP+Kerberos diagnostics To diagnose LDAP synchronization issues first turn on Debug level traces (link). Then reproduce the problem by clicking Synchronize button in LDAP settings. In 10-20 minutes depending on the size of your domains and number of them you should be able to check traces either directly on the server like so: grep LdapC /var/log/kwts-traces | less or by getting the built-in collect and looking in kwts-traces files by other means (link). For example, if you see the following errors: Sep 29 15:30:01 srv-proxy2 KWTS LdapCache[33227]: 33227 DBG trying to connect ldap://server.local:389 Sep 29 15:30:01 srv-proxy2 KWTS LdapCache[33227]: 33227 WRN Couldn't connect ldap://server.local:389 Sep 29 15:30:01 srv-proxy2 KWTS LdapCache[33227]: 33227 ERR CheckFailedException - LDAP error (-2) : Local error - Cannot perform LDAP SASL interactive bind operation. At /tmp/buildbot/core_ldap_cache-kwts_linux-64/build/source/ldap/connection.cpp(203) Then make sure you can connect to server.local:389 with telnet and verify that: On KWTS you can resolve server.local by FQDN and resolve PTR for its IP. Domain controller PTR record should be matched to A record otherwise Kerberos will not work and the error will be exactly as in above log; On server.local you can resolve KWTS by FQDN and resolve PTR for its IP; Time on KWTS servers is synchronized properly with an NTP server. How to use multiple domains in LDAP Create multiple LDAP connections in LDAP settings, one for each domain and use a separate keytab for each; Make sure that a specific DNS server can resolve _kerberos._tcp. and _ldap._tcp. SRV records for each domain. For that in the main domain DNS server you can create stub DNS zones for each domain; Configure KWTS to use that DNS server. Proxy authentication diagnostics Check squid logs: /var/log/squid/cache.log shouldn't contain errors regarding Kerberos or NTLM /var/log/squid/access.log should contain usernames of authenticated users For example: negotiate_kerberos_auth.cc(182) : pid=63851 :2020/06/03 11:28:00| negotiate_kerberos_auth: ERROR: gss_accept_sec_context() failed: Unspecified GSS failure. Minor code may provide more information. Request ticket server HTTP/kwts.test.local@TEST.LOCAL kvno 2 found in keytab but not with enctype rc4-hmac Means that keytab was created with AES128 or AES256 encryption but the user with which it was created doesn't have AES128 or AES256 enabled in user settings (Properties → Account → Account Options → This account supports Kerberos AES 128/256 bit encryption). Trace kinit: Run on KWTS: KRB5_TRACE=/tmp/kr.tr kinit -Vkt /etc/squid/auth_krb5.keytab HTTP/FQDN@REALM where HTTP/FQDN@REALM is the SPN of used keytab. For standalone (not built-in proxy) instead of /etc/squid/auth_krb5.keytab specify the real path to keytab); Check output of the command AND /tmp/kr.tr file, it should contain detailed trace. SSO authentication diagnostics Check logs in /var/log/kaspersky/kwts/extra/ For example in webapi.log if you see ERROR:root:GSSError: (('Unspecified GSS failure. Minor code may provide more information', 851968), ('Request ticket server HTTP/*****@*****.tld found in keytab but does not match server principal HTTP/dpc-kwts-01.example.com@', 100005)) [pid: 14648|app: 0|req: 701/53178] 10.199.5.19 () {50 vars in 4127 bytes} [Wed Oct 14 14:12:46 2020] GET /web/api/get-session-info?cb=1602673966446 => generated 224 bytes in 12 msecs (HTTP/1.1 403) 3 headers in 93 bytes (1 switches on core 0) That means that there are two PTR records in DNS for KWTS IP address. Remove one that is not for the FQDN that should be used to access KWTS web interface. ./celery.log:[2020-06-02 18:00:47,860: ERROR/ForkPoolWorker-1] there are no valid principal for HTTP service on kwts.example.com host in keytab data; <class 'kerberos.KrbError'>: ('Principal not found in keytab', -1) ./webapi.log:ERROR:root:there are no valid principal for HTTP service on kwts.example.com host in keytab data; <class 'kerberos.KrbError'>: ('Principal not found in keytab', -1) Means there is no SPN record in keytab for the FQDN which was accessed by the web browser. ./webapi.log:ERROR:root:GSSError: (('Unspecified GSS failure. Minor code may provide more information', 851968), ('Request ticket server HTTP/*****@*****.tld kvno 6 found in keytab but not with enctype rc4-hmac', 100005)) Means the keytab was created with AES128 or AES256 cryptography but it is not enabled in user settings in AD. ./webapi.log:ERROR:root:GSSError: (('Unspecified GSS failure. Minor code may provide more information', 851968), ('Request ticket server HTTP/*****@*****.tld kvno 8 not found in keytab; keytab is likely out of date', 100005)) Means keytab was created with wrong user password or password was changed after keytab was created. Time out sync between KWTS and DC On KWTS time is far behind DC: ./webapi.log:ERROR:root:GSSError: (('Unspecified GSS failure. Minor code may provide more information', 851968), ('Ticket not yet valid', 100005)) On KWTS time is far ahead DC: ./webapi.log:ERROR:root:GSSError: (('Unspecified GSS failure. Minor code may provide more information', 851968), ('Ticket expired', 100005)) On KWTS time is slightly ahead DC: ./webapi.log:ERROR:root:GSSError: (('Unspecified GSS failure. Minor code may provide more information', 851968), ('Clock skew too great', 100006)) Also you can upload the keytab to the server via WinSCP and trace kinit as in proxy authentication diagnostics. If kinit is successful but browser doesn't authenticate check that web interface FQDN is added to trusted servers in browser settings. See for example: https://docs.cloudera.com/documentation/enterprise/5-12-x/topics/cdh_sg_browser_access_kerberos_protected_url.html Please note that if the keytab that you are adding does not contain an SPN with FQDN from 'hostnamectl' command output, you will get "Invalid keytab file for the Control node". In that case change hostname to FQDN with: hostnamectl set-hostname FQDN Useful tricks Run the following in PowerShell (on DC) to get the list all users for which keytabs were created with SPN that starts with "HTTP/" Get-ADUser -Filter 'UserPrincipalName -like "HTTP/*"' A faster way to find if there are duplicates: setspn -X This command would remove SPN for a specific user kaspersky: setspn -D HTTP/FQDN kaspersky On Windows workstations you can also get the current list of Kerberos tickets with klist Sometimes there might be an incorrect old ticket, in that case you can purge ticket: klist purge You can also request a ticket manually with klist get HTTP/kwts.example.com
-
Problem KSC Web Console can be used for monitoring purposes. It is particularly important to have no timeout disconnection errors in this scenario. To avoid them, the timeout before Web Console disconnects can be increased. Step-by-step guide All you have to do is the following: Edit node.js web server config file located at C:\Program Files\Kaspersky Lab\Kaspersky Security Center Web Console\server\config.json Change the following values and restart KSC WC services: "clientIdleTimeout": 2147483600, "clientLogoutTimeout": 2147483600, "serverLogoutTimeout": 2147483600, This value represents the maximum possible timeout period, which is about 24 days.
-
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. This article is about Kaspersky Endpoint Security for Windows (KES for Windows) Problem 3d party video monitoring solution from HIKVision and KES 11.3 or more recent version, up to 12.0 When you open the URL of video web server, for example, http://172.17.64.5/ the error Playback interrupted occurs. The problem occurs because video software does not comply with HTTP RFC. Use the following key words to identify the problem in KES SRV trace: rtsp://172.17.64.5/Streaming/ .......................................................................... GET /SDK/playback HTTP/1.1 ......................................................................... Incorrect HTTP header (replace the example IP with one of web server's) Solution Add the executable of the web browser to Trusted applications: Tick the option "Do not scan network traffic"; Specify the IP address of the web server in question (in our example, 172.17.64.5) . When adding Internet Explorer to Trusted applications, please make sure to add the x86 version, which is run by default: %ProgramFiles(x86)%\Internet Explorer\iexplore.exe Unfortunately, it is not possible to add an IP subnet or IP range to the list of excluded IP addresses in trusted applications settings. In recent versions of KES, the following event is logged to local reports: Event: Connection blocked Application name: chrome.exe Application path: C:\Program Files\Google\Chrome\Application Application PID: **** User name: **** User type: Active user Component: Protection Event date: **** IP address: 1.1.1.1 Protocol: HTTP or HTTPS Resource name: office365atwork.com Result: The HTTP connection is terminated. Resource name: office365atwork.com Reason: The format of transferred data does not allow to scan it for threats. If you trust this resource, add it to scan exclusions.
-
You may need to add a batch of prevention rules to KATA. To speed up the process, we have created a script sample. Adding more than 1000 prevention rules will require additional PF to improve Web UI performance. Please contact technical support to get this PF. Adding more than 5000 prevention rules is highly NOT recommended as it may result in drastic performance degradation on both CN and Endpoint Agent. Step-by-step guide Script sample. To run it, you need any machine with 2 pre-requisites: sh or bash should be installed on the machine machine should have access to KATA Web UI To use the script, please place a file with hashes (each hash should be on new line in this file) near the script, and please fill in the variables required for script operation: #Fill in your KATA IP or FQDN address KATA_IP="" #Default port is 8443 KATA_PORT="8443" #You need Senior Security Officer account to add preventions USER="SSO" PASS="" To run the script, pass the file with hashes as argument to the script: sh add_prev.sh /path/to/file/with/hashes.txt Once the script is completed, it may take 5-10 minutes for the preventions to appear in Web UI. Export user's prevention rules from KATA 4.0/4.1/5.0 1) Under root execute: docker exec -it `docker ps | grep kedr_database_server | awk '{print $1}'` psql -U kluser antiapt -c "select * from agent_prevention_settings;" > /tmp/prevention_rules 2) Then import /tmp/prevention_rules to Excel as Data > From Text/CSV
-
How to integrate KATA and KWTS [KATA/KEDRE]
svc_kms posted a blog entry in Kaspersky Anti Targeted Attack & EDR Expert's KATA & KEDR Expert community articles
You may have purchased both the KATA and KWTS(Kaspersky Web Traffic Security) products. Since KWTS has built-in KATA integration, you may want to integrate KATA and KWTS. Problems after integration Shortly after integration you may notice that on KWTS side, there is an error about sending objects to KATA, and dashboards look similar to this: Resolution Prerequisite for successful integration with KWTS is KATA version 3.6.1.752 or higher. KATA side To clean tasks, stuck in 'processing' state, do the following: 1) Find out KWTS ID: sudo -u kluser psql antiapt -c "select id, sensor_type, sensor_name, ip from lms.client;" On KATA4: docker exec -it `docker ps | grep kedr_database| awk '{print $1}'` psql -U kluser antiapt -c "select id, sensor_type, sensor_name, ip from lms.client;" Name and IP of KWTS will be the same as in Administrator Web UI, External Systems section. Then, clean up tasks that may be stuck in 'processing state': sudo -u kluser psql antiapt -c "update lms.task set state = 'error', has_error = True where client_id = <KWTS ID> and state = 'processing' and update_time < now() - interval '1 hour';" On KATA4: docker exec -it `docker ps | grep kedr_database| awk '{print $1}'` psql -U kluser antiapt -c "update lms.task set state = 'error', has_error = True where client_id = <KWTS ID> and state = 'processing' and update_time < now() - interval '1 hour';" This command is safe to execute, it will do no harm even if there are no stuck tasks. To view all active tasks from KSMG/KLMS/KWTS/Other external systems without modifying their states, run the command: docker exec -it `docker ps | grep kedr_database| awk '{print $1}'` psql -U kluser antiapt -c "select count(*) from lms.task where client_id=<KSMG ID>;" The two commands above can be used to remove tasks stuck in processing from other types of external systems as well. KWTS side On KWTS side, it is important to exclude certain type of objects from being scanned in KATA: In file /var/opt/kaspersky/kwts/kata-filters.json remove the lines, containing keywords: ArchiveGzip ArchiveCab ExecutableJs After applying changes, restart kwts service: systemctl restarts kwts After these changes, KWTS and KATA integration is expected to work normally further on. -
Please use caution when following the steps. This article is applicable to KATA 3.7.2 and KATA 4.0/4.1 In KATA 3.7, EDR stack is based on microservice architecture, it utilizes Docker Swarm. Containers have their own internal networking, which may cause issues in infrastructure, if the same networks are already used. Docker uses 4 different networks: Name Subnet bridge 172.16.0.0/16 OR 172.17.0.0/16 (depending on KATA version) docker_gwbridge 172.18.0.0/16 ingress 10.255.0.0./16 kataedr_main_1_kata_network 10.0.0.0/16 This article describes the way to change Docker network settings. You should select networks that are not used in the infrastructure, to avoid issues with routing. In most cases, there're overlaps with bridge and docker_gwbridge networks, and changing these networks' subnets resolves the issues. Step-by-step guide Change bridge and docker_gwbridge address pools All the steps must be performed as root. Networks 172.26.0.0 and 172.24.0.0 are used as an example. Default addresses for these networks are 172.16.0.0/16 and 172.18.0.0/16. Obviously, the subnets you select as replacements must not overlap. Create file /etc/docker/daemon.json with the following content: KATA 3.7: { "bip": "172.26.0.1/16" } KATA 4.0: { "shutdown-timeout": 200, "bip": "172.26.0.1/16" } Confirm the config validity (there should be no errors in the output of the following command): cat /etc/docker/daemon.json | python -m json.tool Restart docker: systemctl restart docker If docker isn't able to start after subnets' change, change, to find the cause check tail -n 100 /var/log/dockerd.log If you see a line "failed to start daemon: Error initializing network controller: Error creating default "bridge" network: Pool overlaps with other one on this address space" This indicates the subnet you have selected for bridge is already occupied, you need to select the one that is available. Disconnect the node from Swarm: docker node ls --format {{.ID}} | xargs docker node update --availability drain Ensure all containers are down (there should be no entries in the list of running containers): watch docker ps Run this command and wait until the list of containers is empty, then exit it with CTRL+C Remove docker_gwbridge: docker network disconnect -f docker_gwbridge gateway_ingress-sbox docker network rm docker_gwbridge Create new docker_gwbridge with new network settings: SUBNET=172.24.0.0/20 GATEWAY=172.24.0.1 docker network create \ --subnet=${SUBNET} \ --gateway ${GATEWAY} \ -o com.docker.network.bridge.enable_icc=false \ -o com.docker.network.bridge.name=docker_gwbridge \ docker_gwbridge Connect the node back to Swarm: docker node ls --format {{.ID}} | xargs docker node update --availability active Restart docker: systemctl restart docker Validate your success (command should complete successfully): apt-kafka-util list-topics Change ingress network subnet Sometimes 10.255.0.0/16 subnet is used for KATA CN. This might cause problems as this subnet overlaps with docker's ingress network. To change its settings, modify the script /bin/apt-init-docker-stack: locate and change the constants: INGRESS_SUBNET = '10.255.0.0/16' INGRESS_GATEWAY = '10.255.0.1' Save your changes and run apt-sedr-reset.
-
Sometimes, you may want to have Kaspersky Endpoint Agent traces which start from its very cradle. This guide is applicable to local installation. Step-by-step guide Place the attached JSON file next to endpointagent.msi file. Feel free to modify patch to traces folder inside. Install Endpoint Agent using GUI or command line: msiexec /i endpointagent.msi /qn Traces will appear as soon as the services start, even before the installation completes.
-
Problem Sometimes the problem with events receiving/transferring on KSC (including export to SIEM) may occur. The first thing that you have to check is Kaspersky Event Log. The following warnings may occur: Warning Total number of events stored in database (4010532) has exceeded the actual limit of 4000000 event(s). Starting to delete excessive events from the database... Warning 600 event(s) have been deleted from the database because the limit of 4000000 event(s) was exceeded. Warning Server is busy: event has been rejected for device '<Device_name>', most common events in the database are: 'Scheduled' (from 'KES 11.0.0.0'), 'Error sending the request to KSN' (from 'Kaspersky Security 10 for Windows Server 10.0.0.486') and 'Password-protected archive detected' (from 'KES 11.0.0.0') The same is correct for SIEM integration. Because KSC is busy, it won't provide event to SIEM immediately. You'll have to wait until load will be decreased.Events are coming from the hosts to KSC and sometimes KSC just cannot process all of them. For example, during KES update task all the hosts transfer event Scheduled and then Running. The more hosts you have, the more chance that KSC will suffer a pike load which will lead to the other events rejecting. Solution Configure events storing in all KES policies according to https://support.kaspersky.com/KSC/14/en-US/92424_1.htm Open KEL and check what the most common events in the database are. Most probably those events will be informational and not very helpful. Disable storing events you are not interested in on KSC server in all corresponding policies. Task related events can be disabled in the corresponding task properties, on the Notifications tab. There are different store events options, choose to store only task execution results. Do this for all the tasks running of which cause "server busy" event. After a while events receiving/transferring should be normalized.
-
Trusted Applications [KES for Mac]
svc_kms posted a blog entry in Kaspersky Endpoint Security's KES for Windows
The KESMac 12 and the KESMac 11.3 patch C allows adding particular processes into the trusted section named Trusted Applications. The both filesystem and network activity of which can be ignored by the product increasing performance. Please, however, note that this could be potentially risky. https://support.kaspersky.com/KESMac/11.3_adminguide/en-US/194142.htm Problem This article will describe a few ways to configure KES for Mac to exclude some of the software from the scope of the product. Solution Trusted applications In order to have an ability to exсlude an application from scanning with KES, a function of Trusted Applications available in Kaspersky Endpoint Security for Mac can be used: The Trusted applications section as seen in the policy creation wizard. Naturally, it can be configured later by modifying the policy. Update the plugin to at least version 11.3.0.33 to get the new functionality. In some specific cases it might be required to put several binaries to Trusted Applications simultaneously in order to take effect. So, a final solution might include several path-based exclusions accompanied by a few BundleID-based ones. Trusted Applications are only available for configuration via KSC policy; i.e. it is currently impossible to add application to exclusions having no KSC installed. Additionally, an appropriate application control plug-in for KESMac must be downloaded and installed on the KSC prior to using Trusted Application functionality. It can be found on the corresponding download page. Common exclusions for developers It's suggested excluding the following paths: "/Library/Developer/CommandLineTools" and "/Library/Toolchains" for the standard developers' utilities, as well as the "/Applications/Xcode.app/*" for the XCode. At the same time, in case you use alternative tools, contact Kaspersky Support to get the exact paths for further exclusions. Excluding TCP 443 from port monitoring Additionally, in case of HTTPS-connectivity issues, unchecking port 443 in Monitored ports may also help: -
KSWS spawns a lot of PR*.tmp files [Kaspersky Security for Windows Server]
svc_kms posted a blog entry in Kaspersky Endpoint Security's KES for Windows
Problem You might notice that large files named like PR*.tmp appear in C:\Windows\Temp. Cause This is known and expected behavior. When the product scans an object it creates a temporary copy, names it like PR*.tmp and places it in the temp folder.Once the scan is complete, this temporary file gets deleted. Large PR*.tmp files mean that some large objects are scanned by OAS (On-Access Scan) or ODS (On-Demand Scan). Solution In some cases there might be not enough space of drive to create large temporary file. Below are the possible solutions: Exclude large objects from OAS and ODS; In OAS and ODS settings, enable option 'Do not scan compound objects larger than' and specify required size in MB; Change the folder where KSWS temporary files are created to a drive with higher capacity. In KSWS11 this can be achieved by editing Application settings → Scalability, interface and scan settings → Scan settings → 'Folder for temporary files created during scanning'. In KSWS10 use below registry entry: [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\KasperskyLab\WSEE\10.1\Environment] "ProcessingTempPath"="d:\\Temp\\" -
How to copy files to/from KATA [KATA/KEDRE]
svc_kms posted a blog entry in Kaspersky Anti Targeted Attack & EDR Expert's KATA & KEDR Expert community articles
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. We suggest free and lightweight client, part of Putty: pscp. Step-by-step guide You can download pscp.exe for Windows from official site. Navigate to the folder with pscp.exe and start cmd or powershell there To copy files to KATA, run the following command: .\pscp.exe -scp <path to local file> admin@<kata_ip>:<remote location> .\pscp.exe -scp D:\patch.ktgz admin@10.70.244.89: \\sample command that will put patch.ktgz to /var/op/kaspersky/apt/files/ folder To copy files from KATA, run the following command: .\pscp.exe -scp admin@<kata_ip>:<filename> <path to local folder> .\pscp.exe -scp admin@10.70.244.89:collect-20200429-133436.tar.gz D:\ \\sample command for downloading collect from KATA -
Problem While running Fix vulnerabilities task, the following error can occur: 'Transaction became the database conflict victim: '1205, 'Lock wait timeout exceeded; try restarting transaction' , LastStatement='CALL vapm_arrange_task_updates(119, 0xC89EAD3312227039C9FAC933840D7936)' Solution Most possible, the reason of the problem is that you have Fix vulnerabilities task or tasks with a big number of vulnerabilities that should be fixed inside one task. For example, you scroll list of KLAs and add each KLA to be fixed in the existing task. You have to check all fix vulnerabilities tasks or delete them and create new tasks. In the tasks, it's suggested to use categories attributes (like severity level etc.) instead of the big list of vulnerabilities.
-
I need to use Split Tunnelling in Kaspersky VPN as one of my mail providers won't work with VPNs so that mail client is on the exception list not to use the VPN and works fine. The problem I have is that devices on the LAN that are accessed via a browser return a Bad Gateway error message and cant reach them. I don't want to put the browser in exception list as I want that traffic routed through the VPN. Is it possible to add IP addresses for LAN devices into the exception list so they don't get routed through the VPN? Windows 10 22H2 19045.6159 Kaspersky Small Office Security & Kaspersky VPN
-

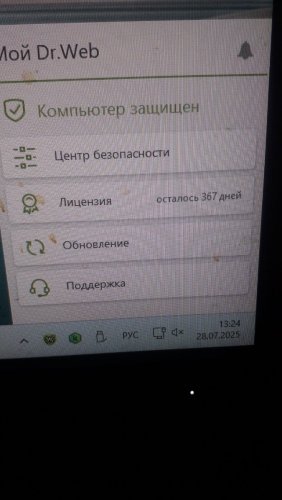
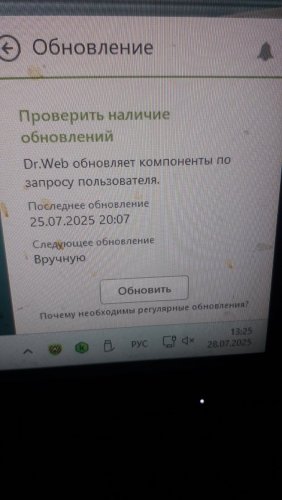
kasper prem & dr.web katana
kmscom replied to HARMONY's topic in Kaspersky: Basic, Standard, Plus, Premium
Давайте не будем превращать тему в блог @Лексей и его отношениям с Катаной. пользуйтесь и пользуйтесь. все хорошо и ладно. -
Audrinabo joined the community
-
Ошибки при обновлении антивирусных баз
olegseyo replied to olegseyo's topic in Kaspersky Security Center
PostgreSQL 14.18 В требованиях есть 14.х -

Ошибки при обновлении антивирусных баз
durtuno replied to olegseyo's topic in Kaspersky Security Center
Тогда указывайте и наименование и версию БД, возможно, что несовместимость. Ну, и конфиг БД сразу приведите, может там не рекомендуемые параметры или ещё чего. -

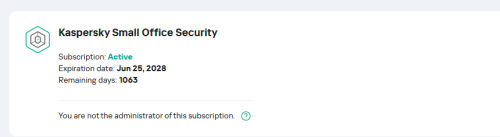
Kaspersky Small Office Lince only allows you to use the free VPN version
Caos replied to TI 2 jeringasr's topic in Kaspersky Small Office Security & Management Console
Are you the administrator of this suscription? Also, you can open a support ticket using my Kaspersky. Regards -
kasper prem & dr.web katana
Лексей replied to HARMONY's topic in Kaspersky: Basic, Standard, Plus, Premium
- Today
-
Ошибки при обновлении антивирусных баз
olegseyo replied to olegseyo's topic in Kaspersky Security Center
У меня вроде пока что пробная лицензия, или про лицензию чего идет речь? -
Kaspersky Small Office Lince only allows you to use the free VPN version
TI 2 jeringasr replied to TI 2 jeringasr's topic in Kaspersky Small Office Security & Management Console
-

Ошибки при обновлении антивирусных баз
durtuno replied to olegseyo's topic in Kaspersky Security Center
Ну как бы тут, в выводе, про проверку лицензии идёт речь? Нет? Как у Вас с оной обстоят дела? Добавили? Успешно? -
Kaspersky Premium is just Kaspersky Plus with some additional services: https://support.kaspersky.com/help/Kaspersky/Win21.22/en-US/152975.htm
-
I was actually planning to migrate to Kaspersky Premium. What do you advise?
-

Kaspersky Small Office Lince only allows you to use the free VPN version
Caos replied to TI 2 jeringasr's topic in Kaspersky Small Office Security & Management Console
Hello, Please, open a support ticket en KSOS Portal or web. Regards