
rqueizan
-
Posts
14 -
Joined
-
Last visited
Posts posted by rqueizan
-
-
More detailed scenario:
I don't want anyone to have permission to run any EXE files from the D:\Download folder and its subfolders.
Otherwise, they can copy, cut, create, delete freely.This is my real goal!
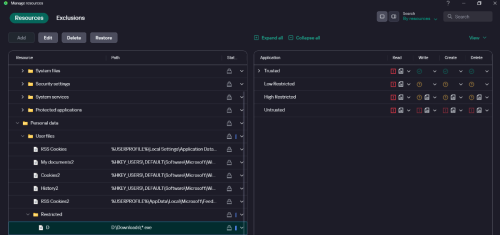
In the absence of an execute permission, I denied all read permission on the folder, regardless of the level of trust.
This certainly blocks execution, and doesn't interfere with copying files.
It only bothers me that the rule actually applies every time someone accesses the file list of the folder in question.My ultimate goal is to restrict the execution of any executable (exe, msi, bat, ps1, com) on the entire D disk.
And only allow it to run on a certain folder on disk D.But I consider that the launch of the event by simply listing the files in a folder is so bulky, I think that by putting the whole disk, it could be chaos, perhaps a high consumption of CPU and RAM resources. An anticipatory speculation on my part.
-
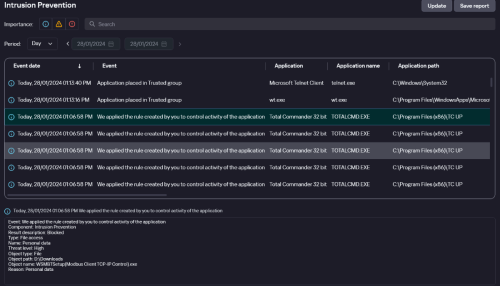
There is a problem with this form of blocking.
It will notify you every time a program accesses to list files, not necessarily by running it.
The rule applies when the restricted folder is listed by a file explorer such as Total Commander or Windows Explorer itself.I think it would be best to add a new column, explicitly involving the execution of a program.
-
1 hour ago, harlan4096 said:
Read also may mean just "Access" to the file/folder or in general to the resource...
Initially, I thought Read refers to the action of reading.
That's why I find it a bit confusing to block an execution by blocking the Read option.
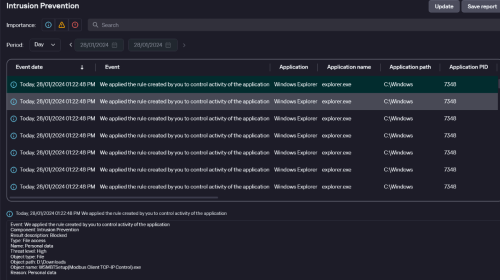
In addition, it allows me to cut the file from the folder, and paste it back in.
To cut a file, you need Read and Write. -
This way it works, more aggressive than I'd like, but it solves in the worst-case scenario.
It would be interesting if in addition to Read, Write, Create and Delete it allowed Run independently. Suggestion.The way shown in the image, it allows me to take it out of that folder, and put it back in.
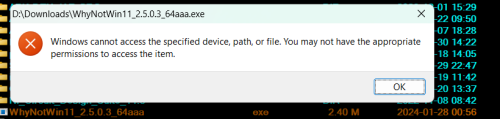
Prevents the icon from being displayed.
But it definitely blocks execution.-
 1
1
-
-
Is it possible to block the execution of any executable (exe, bat, ps1) of disk D from Kaspersky Premium 21.15.8.493(a)?
Windows 11 Enterprise 22H2, Build 22621.3085
My goal is to allow the execution of everything that is on disk C, and some folders on disk D, the rest that is restricted.
-

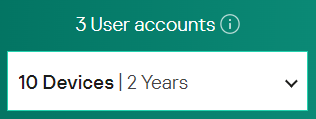
X = 3, Y = 10, Z = 2
What does "X User Accounts" mean?
That I can create X "my.kaspersky.com" accounts, and put the same license on these accounts?
Y Devices: I interpret that it is the number of devices (PC, Mac, iPhone, iPad and Android) that I can protect, each one of them counts as one and they are not related to each other.
Z Years: Number of years of validity of the license from the first activation.
Am I correct or have I misunderstood something?-
 1
1
-
-
I solved the problem.
I removed the license from the antivirus, and adding the new license successfully activated.
The remove license icon visually looks like a shopping basket.
That's why I never touched it and didn't know it was to remove the license. -
I already wrote to support.
If you encounter any problem please contact Kaspersky Technical Support→ https://support.kaspersky.com/b2c#contacts
→ Contact us → Product help → E-mail → Contact Support
Form
→ Request Type ?
→ Select "Activation and license issues"
I already wrote to support.
-
@rqueizan Welcome.
This guide it is outdated, or that option it is not available for me.
-
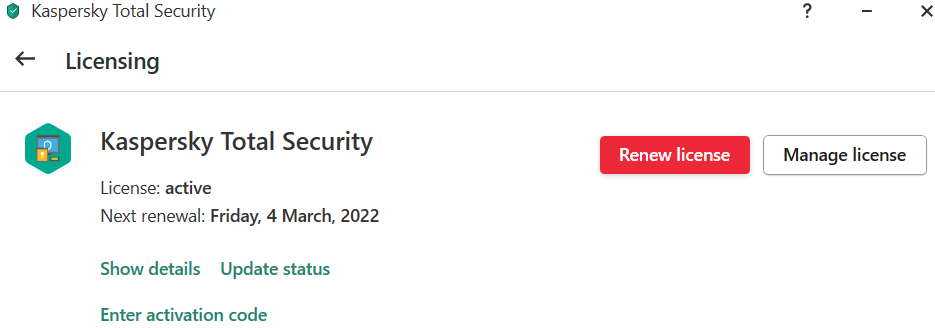
Yes, but I need cancel the subscription, not renew.


-
I thought maybe by canceling the subscription I could activate the new one.
-
How can I cancel a subscription that is about to expire?
When it expires it is automatically deleted? -
Windows 11 Enterprise, Build 22000.527
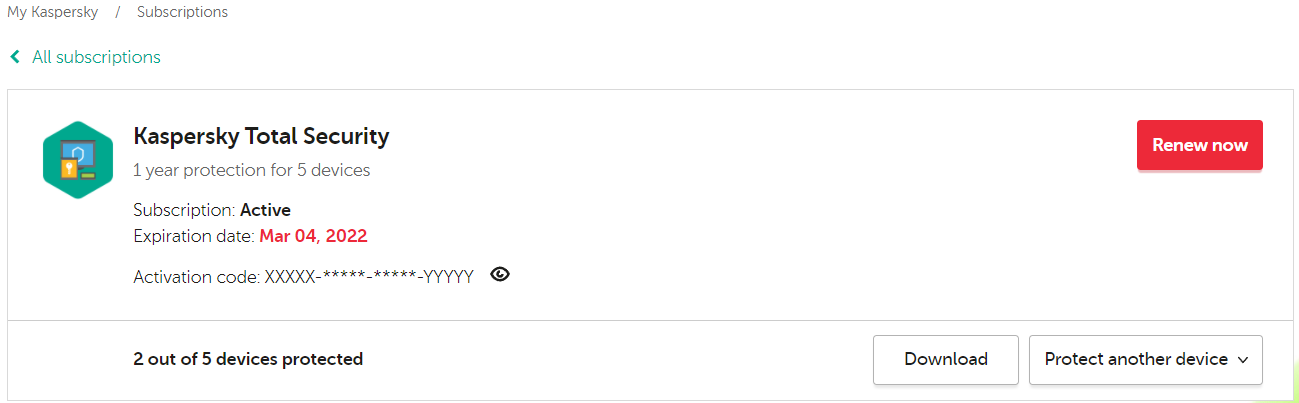
Kaspersky Total Security 21.3.10.391 (h)I want to leave 2 computers from a subscription and protect them with a newer one.
It gives me an error to add the license directly from the KTS, at least without removing the old one.
From the subscription management page it only lets me download the installer.
Prevent the execution of programs on unauthorized paths
in Kaspersky: Basic, Standard, Plus, Premium
Posted
On the other hand, when cutting a file from disk C to disk D. Technically you have to do a read on disk C, write to disk D, delete the original file on disk C.
If I blocked the read permission, I theoretically shouldn't be able to copy or cut it, since I'm not allowed to read it, right?
If an execute permission exists, the execution goes beyond a read, as it needs to be loaded into memory to execute. This would initially involve a disk read and a RAM write.
It could block execution without restricting the read, allowing the file to be copied and cut.