How to configure ICAP integration in KATA 6+ [KATA/KEDRE]
Don't forget to install 6.0.1 and 6.0.2 patch, which fixes some bugs in ICAP integration.
Description and cautions
Since we have new ICAP working modes, presented in KATA 6.0 - https://support.kaspersky.ru/KATA/6.0/en-US/247269.htm , we would like to show you, how to configure such integration on example of squid proxy server.
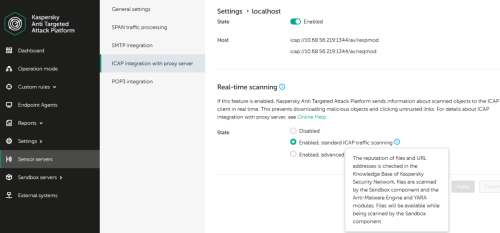
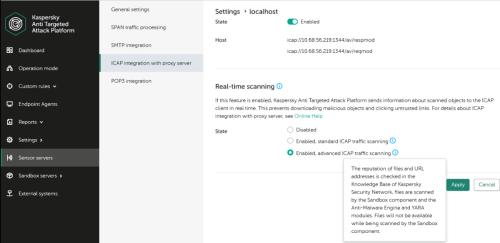
Added ICAP integration with feedback. ICAP integration with feedback can work in two modes:
- Standard scan. In standard scan mode, the object is scanned by all supported technologies. While being scanned by the Sandbox component, the object remains available. If a threat is detected, the object is blocked.
- Advanced scan. In the advanced scan mode, objects are scanned by all supported technologies. While being scanned by the Sandbox component, the object is not available. If a threat is detected, the object is blocked.
Details
Reminder - this is just an example, but working one:)
Squid configuration part
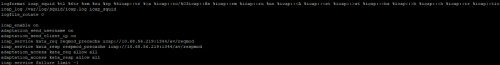
Assuming you already have squid installed with default configuration (of course, yours could be different according to your infrastructure), add following lines in the end of /etc/squid/squid.conf (surely, change the IP address to yours)
icap_enable on
adaptation_send_username on
adaptation_send_client_ip on
icap_service kata_req reqmod_precache icap://10.68.56.219:1344/av/reqmod
icap_service kata_resp respmod_precache icap://10.68.56.219:1344/av/respmod
adaptation_access kata_req allow all
adaptation_access kata_resp allow all
icap_service_failure_limit -1
|
The only thing we changed here as well is at the start of squid.conf - source subnet, in order to adapt server to our Lab
#
# Recommended minimum configuration:
#
# Example rule allowing access from your local networks.
# Adapt to list your (internal) IP networks from where browsing
# should be allowed
acl localnet src 10.68.56.0/23
|
We also recommend to add these lines below as well, so you would be able to analyze ICAP logs
logformat icap_squid %tl %6tr %rm %ru %rp %6icap::tr %>a %icap::to/%03icap::Hs %icap::rm %icap::ru %un %icap::<A %icap::<st %icap::>st %icap::<bs %icap::>h %icap::<h %icap::tr %icap::tio
icap_log /var/log/squid/icap.log icap_squid
|
ICAP logs are located at /var/log/squid/icap.log and look like
So the whole picture should look like this
Testing part
If standard scan mode is enabled, let's check on KATA side, how it looks like in /var/log/kaspersky/services/preprocessor_icap/preprocessor_icap.log
grep --color 'blocking_simple mode' | grep 'verdict'
|
- In this example we can see that from URL file was scanned with verdict: clean (whitelist)
09:41:46.697 INF 137781 server/source/file_handler_respmod.cpp:435 [sid: 0x0000004d] RESPMOD: Finish processing file in blocking_simple mode (request url: 'r3.o.lencr.org', size: 503, filename: 'baf664a8a7841e1d057f5ab0da58bcf0', uuid: 5cc2d18781924f98b6e4961494125616, md5: baf664a8a7841e1d057f5ab0da58bcf0, format: GeneralBin), processing time: 0.147ms, verdict: clean (whitelist)
- File from URL with verdict: clean (cached)
09:40:14.476 INF 137778 server/source/file_handler_respmod.cpp:435 [sid: 0x0000004a] RESPMOD: Finish processing file in blocking_simple mode (request url: 'detectportal.firefox.com/success.txt?ipv6', size: 8, filename: 'success.txt', uuid: 25f155a67eff4a4a90b33dbbb4f3367c, md5: ae780585f49b94ce1444eb7d28906123, format: GeneralTxt), processing time: 0.124ms, verdict: clean (cached)
- URL with verdict: good (KSN)
09:42:37.334 INF 137780 server/source/file_handler_reqmod.cpp:187 [sid: 0x0000004c] REQMOD: Finish processing url in blocking_simple mode ('box.kaspersky.com'), processing time: 3ms, verdict: good (KSN)
- File from URL verdict: clean (scanned)
09:35:14.691 INF 137770 server/source/file_handler_respmod.cpp:435 [sid: 0x00000042] RESPMOD: Finish processing file in blocking_simple mode (request url: 'detectportal.firefox.com/success.txt?ipv4', size: 8, filename: 'success.txt', uuid: 4c87c81cf3d543ceb6694d917329d2b8, md5: ae780585f49b94ce1444eb7d28906123, format: GeneralTxt), processing time: 124.894ms, verdict: clean (scanned)
- URL with verdict: bad (KSN)
10:05:18.354 INF 137802 server/source/file_handler_reqmod.cpp:187 [sid: 0x00000062] REQMOD: Finish processing url in blocking_simple mode ('kaspersky.com/test/wmuf'), processing time: 146ms, verdict: bad (KSN)
If advanced scan mode is enabled, let's check on KATA side, how it looks like in /var/log/kaspersky/services/preprocessor_icap/preprocessor_icap.log
grep --color 'blocking_advanced mode' | grep 'verdict'
|
Picture is pretty the same, but from browser side you will see that object is blocked/inaccessible
10:54:01.341 INF 139635 server/source/file_handler_reqmod.cpp:187 [sid: 0x0000000e] REQMOD: Finish processing url in blocking_advanced mode ('bug.qainfo.ru/test_cloud/wmuf'), processing time: 27ms, verdict: bad (KSN)
10:54:20.467 INF 139635 server/source/file_handler_reqmod.cpp:187 [sid: 0x0000000e] REQMOD: Finish processing url in blocking_advanced mode ('secure.eicar.org:443'), processing time: 0ms, verdict: good (KSN)
10:50:45.303 INF 139632 server/source/file_handler_respmod.cpp:435 [sid: 0x0000000b] RESPMOD: Finish processing file in blocking_advanced mode (request url: 'ocsp2.globalsign.com/gsorganizationvalsha2g3', size: 1461, filename: 'gsorganizationvalsha2g3', uuid: f88dd52252da4fdf8aaabc3aafdbdb0a, md5: 9a3ec48893b2952f013e03311b878e18, format: GeneralBin), processing time: 0.346ms, verdict: clean (whitelist)
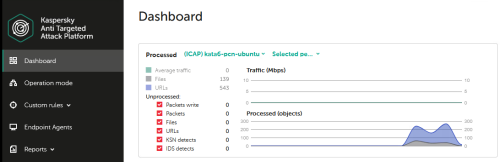
During tests at KATA web UI you should see activity on ICAP dashboard
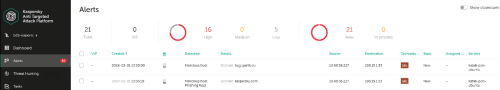
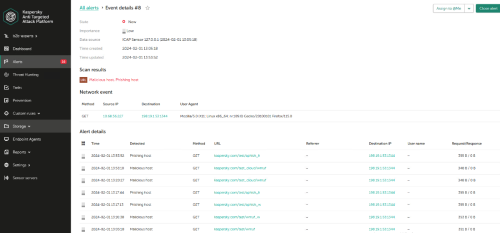
and under Security office we can see two alerts, generated after our tests (10.68.56.227 is squid IP address)
In real world, of course, you will see other detects as well, for instance, on infected objects and malicious URLs.
























0 Comments
Recommended Comments
There are no comments to display.
Please sign in to comment
You will be able to leave a comment after signing in
Sign In Now