Can't enable KATA two-way authentication (client TLS) in KES policy [KATA/KEDRE]
Problem description:
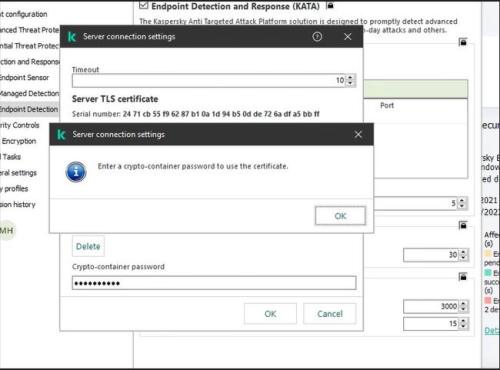
After generating the client certificate on central node and upload it to KES policy, you can get the below error:
Enter a crypto-container password to use the certificate.
Note: If you are using KEA as a standalone product with KEA policy, you can upload the client certificate properly.
Root cause:
By default, the cryptographic container is not password-protected. The cryptographic container contains only the certificate file, but not the private key file. KES policy does not apply certificate without password (only KEA does).
Solution:
Access the central node SSH under root account
1) Export you current certificate to a passwordless pem type:
#openssl pkcs12 -in mycert.pfx -out tmpmycert.pem -nodes
Enter Import Password: <Enter no password>
MAC verified OK
2) Convert the passwordless pem to a new pfx file with password:
#openssl pkcs12 -export -out mycert2.pfx -in tmpmycert.pem
Enter Export Password: <Enter password here>
Verifying - Enter Export Password: <Enter password here>
Now you can use the new mycert2.pfx file with your new password.
























0 Comments
Recommended Comments
There are no comments to display.
Please sign in to comment
You will be able to leave a comment after signing in
Sign In Now