Deployment of a Kaspersky failover cluster [KSC for Windows]
Description and cautions
That article is describing a specific scenario: HA Cluster KSC with 4 CGWs between two different and geographical isolation DC (Data Center).
High level procedure:
- KLAdmins group: ksc, rightless / gmsa-ksc-server, gmsa-ksc-nwc; $KSC-NODE-1, $KSC-NODE-2, $SQL-SRV / sql / gmsa-sql-server
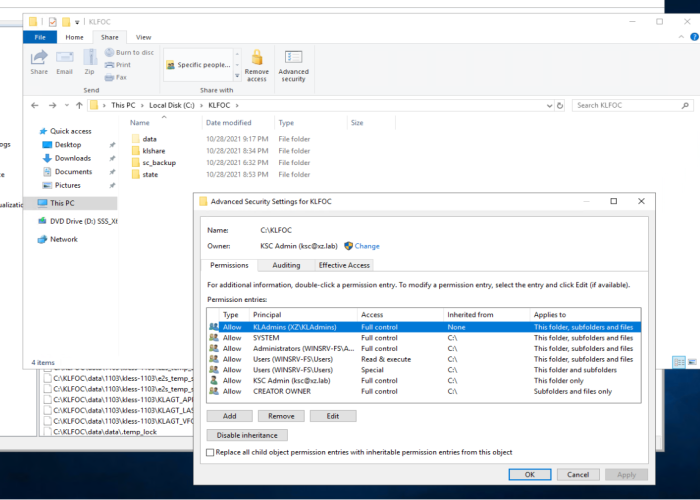
- SMB shares: data, state, sc_backup, kl-share |
- SMB Permissions NTFS ACL - - Full Control for KLAdmins
- Created MS SQL Database - KLFOC | Grand Access for admin server account
- Reboot servers
- Map network drivers - data, state
- Install KLFOC
Details
Here below is the detailed step-by-step procedure:
General terms
- HA - High availability
- DC - Data Center
- CGW - Connection Gateway
- gMSA - Group Managed Service Accounts
- WSFC - Windows Server Failover Cluster
Prerequisites
Hardware and software requirements
To deploy a Kaspersky failover cluster, you must have the following hardware:
x2 Windows Server with identical hardware and software. These servers will act as the active and passive nodes.
|
OS Windows Server 2019 |
Activated & configured OS Windows Server 2019 on 2x servers. Latest Windows updates & drivers installed. |
|
Windows Firewall |
Disabled Windows firewall on 2x KSC server nodes |
|
DNS A & PTR records for Nodes |
2x IP address for the KSC nodes |
|
Internet connectivity |
For 2x KSC server nodes 1. For downloading signatures and application updates on KSC cluster. 2. For downloading third party updates of vulnerability and patch management (if applicable). |
| Microsoft OLE DB Driver for SQL Server | Link | Introduce multi-subnet failover capabilities in this first upcoming release, and keeps up with latest TLS 1.2 standards |
| Connection with TLS 1.2 |
1. Make sure that remote SQL Server (or SQL Express) used by the Administration Server is a really 64-bit application (sqlservr.exe is a 64-bit process) 2. At the computer with Administration Server installed do the following:
3. Make sure that Administration Console successfully connects Administration Server and Kaspersky Event Log at the Administration Server computer does not contain errors like 'Generic db error: "11526 '{42000} The metadata could not be determined' |
File server that supports the CIFS/SMB protocol, version 2.0 or higher. A server that is participating in a WSFC.
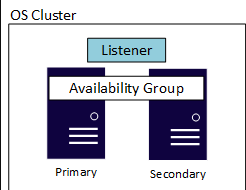
DBMS | MS SQL cluster on WSFC with Always On availability groups.
|
|
SQL Server Failover Cluster Installation | |
| Listener DNS Name | Specifies the DNS host name of the availability group listener. The DNS name is a string must be unique in the domain and in NetBIOS | |
| Microsoft OLE DB Driver for SQL Server | Link | Introduce multi-subnet failover capabilities in this first upcoming release, and keeps up with latest TLS 1.2 standards | |
|
Pre-created Database on MS SQL cluster |
(DB name should be one word without special characters) | |
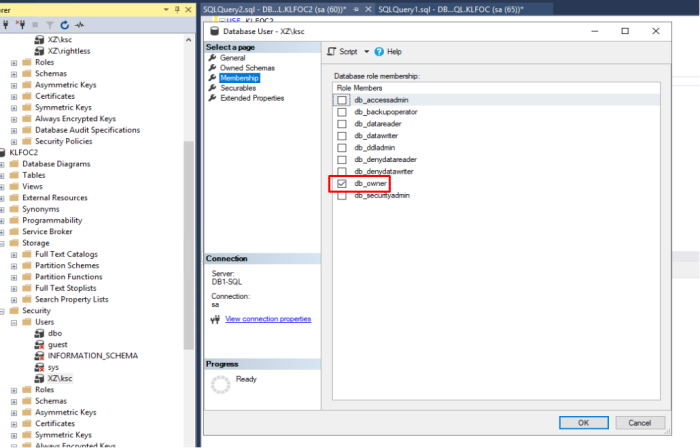
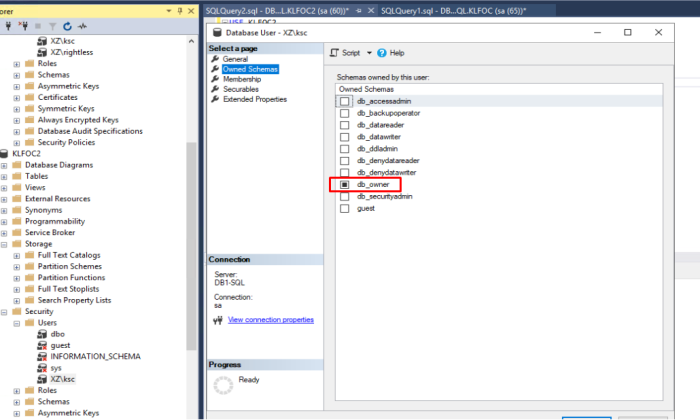
| Grand permission "DB Owner" for account under which the services of Kaspersky Security Center will run. |
Switch conditions
The failover cluster switches protection management of the client devices from the active node to the passive node with CGs in LAN or DMZ network if any of the following events occurs on the active node:
- The active node\LAN-CGW\DMZ-CGW is broken due to a software or hardware failure.
- The active node was temporarily stopped for maintenance activities.
- At least one of the Kaspersky Security Center services (or processes) failed or was deliberately terminated by user. The Kaspersky Security Center services are the following ones: kladminserver, klnagent, klactprx, and klwebsrv.
- The network connection between the active node and the storage on the file server was interrupted or terminated.
Deployment of a Kaspersky failover cluster
Creating an account for Kaspersky Security Center services
Create a new domain group, name it 'KLAdmins', and then grant the local administrator's permissions to the group on both nodes and on the file server. Then create two new domain user accounts, name them 'ksc' and 'rightless', and add the accounts to the KLAdmins domain group.
Add the user account, under which Kaspersky Security Center will be installed, to the KLAdmins domain group.
|
Domain accounts |
Account for installer running - Local admin |
|
gMSA service account |
1. gMSA service account will be used to run tKaspersky Security Center 13 Administration Server services.
2. gMSA service account must have Dbo role permission on the pre-created Kaspersky database running MS SQL cluster. Dbo schema must be used by default. For more details on required permissions to be assigned https://support.kaspersky.com/KSC/12/en-US/156275.htm 3. Assign domain admin permission for KSC installation process only. |
|
KLAdmins - Global security group: |
|
File server preparation
Prepare the file server to work as a component of the Kaspersky failover cluster. Make sure that the file server meets the hardware and software requirements, create two shared folders for Kaspersky Security Center data, and configure permissions to access the shared folders.
| Step | Description | |
|---|---|---|
| 1 |
Make sure that the file server meets the hardware and software requirements. |
|
| 2 |
Make sure that the file server and both nodes (active and passive) are included in the same domain or the file server is the domain controller. |
|
| 3 |
On the file server, create Shared folders: data, state, klshare and SC_Backup on fileserver. One of them is used to keep information about the failover cluster state. The other one is used to store the data and settings of Kaspersky Security Center. |
|
| 4 |
Grant full access permissions (both share permissions and NTFS permissions) to the created shared folders for the following user accounts and groups:
|
Preparation of active and passive nodes
Prepare two computers with identical hardware and software to work as the active and passive nodes.
To prepare nodes for a Kaspersky failover cluster:
- Make sure that you have two computers that meet the hardware and software requirements. These computers will act as the active and passive nodes of the failover cluster.
- Make sure that the file server and both nodes are included in the same domain.
- Do one of the following:
|
Skip this step and configurarion CGWs after installation KLFOC
|
|
|
- Restart both nodes and the file server.
- Map the two shared folders, that you created during the file server preparation step, to each of the nodes. You must map the shared folders as network drives. When mapping the folders, you can select any vacant drive letters. To access the shared folders, use the credentials of the user account that you created before.
The nodes are prepared.
Database Management System (DBMS) installation
Select any of the supported DBMS, and then install the DBMS on a dedicated computer. For best practice, will use HA configuration of DBMS\SQL.
-
MS SQL cluster on WSFC with Always On availability groups.
MS SQL cluster
SQL Server Failover Cluster Installation Listener DNS Name Specifies the DNS host name of the availability group listener. The DNS name is a string must be unique in the domain and in NetBIOS Microsoft OLE DB Driver for SQL Server | Link Introduce multi-subnet failover capabilities in this first upcoming release, and keeps up with latest TLS 1.2 standards DB - KLFOC Create Database with specified name and grand permission "DB Owner" for account under which the services of Kaspersky Security Center will run.
- DB - KLFOC - Create Database with specified name and grand permission "DB Owner" for account under which the services of Kaspersky Security Center will run.
- Pre-created Database on MS SQL cluster (DB name should be one word without special characters)
Kaspersky Security Center installation
Install Kaspersky Security Center in the failover cluster mode on both nodes. You must first install Kaspersky Security Center on the active node, and then install it on the passive one.
- How-to instructions: Installing Kaspersky Security Center on the Kaspersky failover cluster nodes
Specifying the Administration Server certificate
If necessary, you can assign a special certificate for Administration Server by using the command-line utility klsetsrvcert.
To replace the certificate you must create a new one (for example, by means of the organization's PKI) in PKCS#12 format and pass it to the klsetsrvcert utility
klsetsrvcert.exe --stp klfoc -t C -i "C:\KLFOC\new-cert.pfx -p "<password>" -l "new-cert-change.log" -o "NoCA"
|
When the certificate is replaced, all Network Agents that were previously connected to Administration Server through SSL lose their connection and return "Administration Server authentication error". To specify the new certificate and restore the connection, you can use the klmover utility.
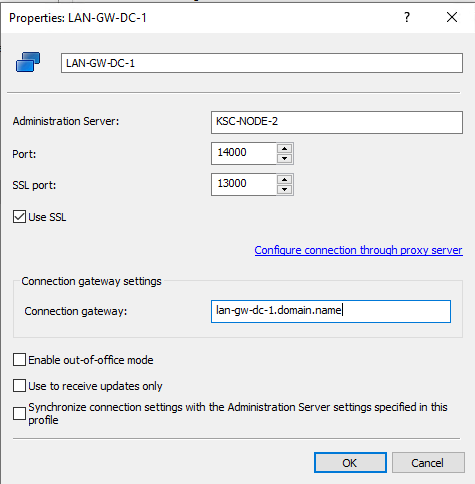
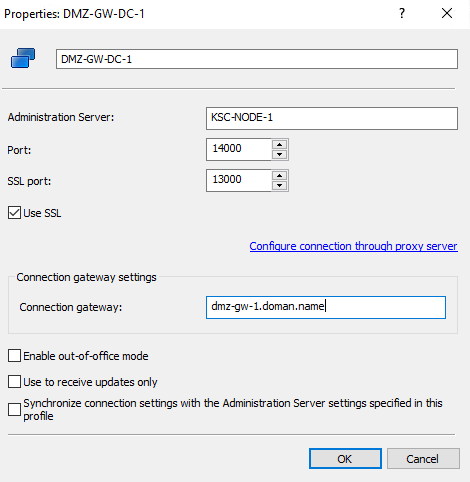
Settings LAN\DMZ Gateways
-
Assigning Workstations (LAN-GW) to act as a distribution point
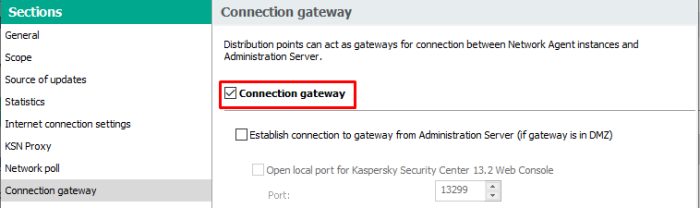
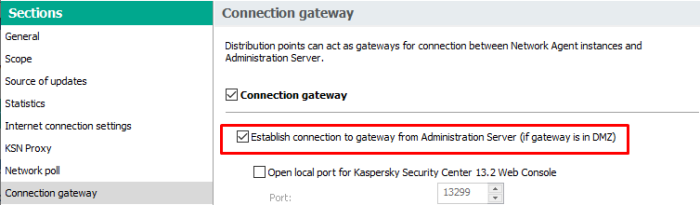
- Enable feature "Connection Gateway"
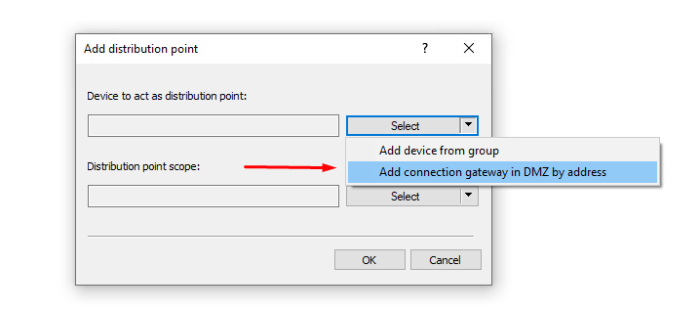
- Adding a connection gateways in the DMZ as a distribution point
- Install external gateways with the setting that this is a connection gateway in the DMZ
- On the KSC, add a distribution point as a connection gateway in the DMZ
- KSC initiates a connection to gateway and the gateway will appear as a distribution point
- Open the properties and set the checkbox in the Connection gateway section
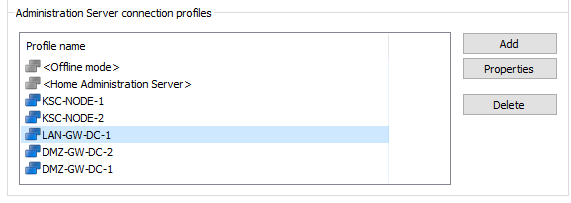
- Create group for GW and add workstations with installed DPs and GWs
Configuration for Network Agent Policy
- Create 2 groups for workstations DC-1 and DC-2 and group for GW
-
For both groups create policies:
- Network Agent DC-1
- Network Agent DC-2
Testing the failover cluster
Check that you configured the failover cluster correctly and that it works properly.
For example, you can stop one of the Kaspersky Security Center services on the active node: kladminserver, klnagent, ksnproxy, klactprx, or klwebsrv. After the service is stopped, the protection management must be automatically switched to the passive node.
Troubleshooting
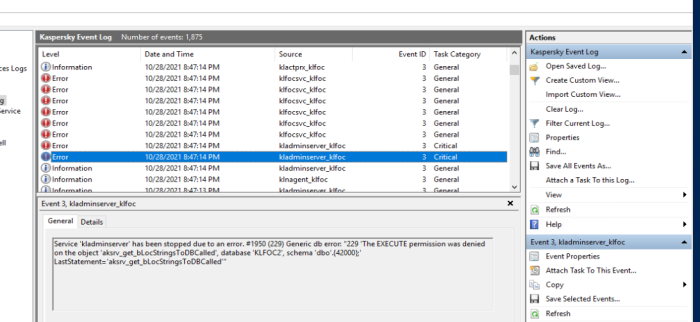
DB Error
Check permissions for gMSA account
KLBACKUP
Run klbackup utulity with --stp klfoc
klbackup --stp klfoc
|
























0 Comments
Recommended Comments
There are no comments to display.
Please sign in to comment
You will be able to leave a comment after signing in
Sign In Now