How to export events to Splunk
This article is about Kaspersky Security Center for Windows (KSC for Windows)
Step-by-step guide
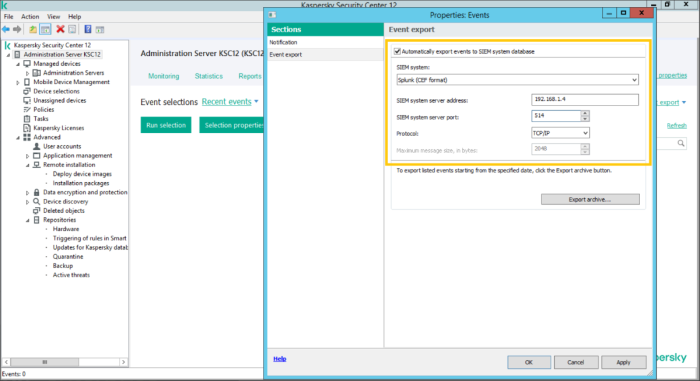
Make sure that System Management license is installed, otherwise KSC events won't be exported to SIEM. For more information please refer to SIEM integration: the most frequent error.
-
Specify Splunk Server address and port;

-
Login into Splunk Management console;

-
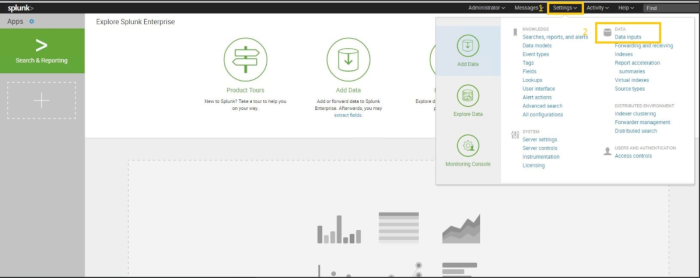
Press Settings → Configure data inputs;

-
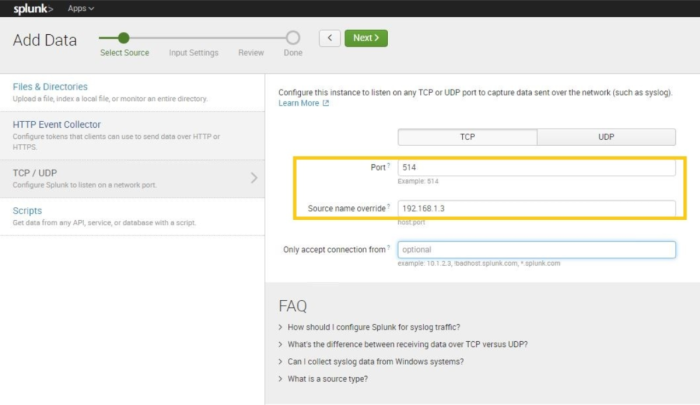
In the opened Add Data window
- select TCP;
- Specify Port you are planning to use. And a Source (KSC server address or DNS-name).

-
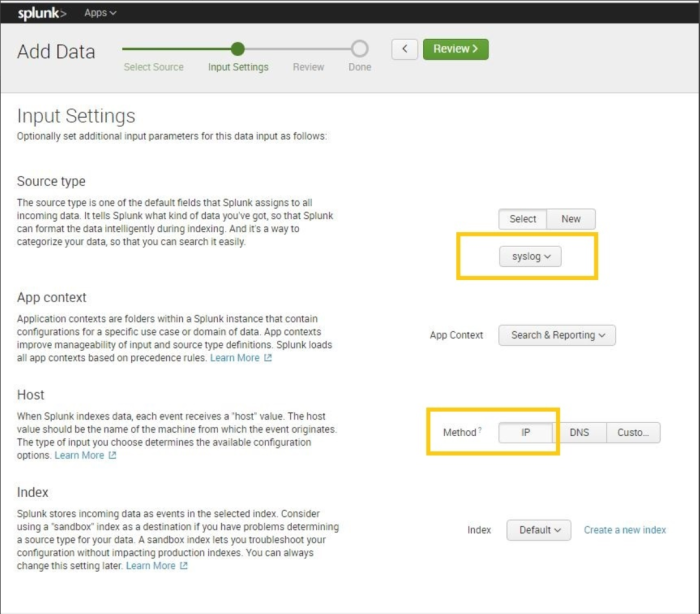
Configure Source type: choose Select and pick syslog from drop down menu. Configure Host: set IP for Method

-
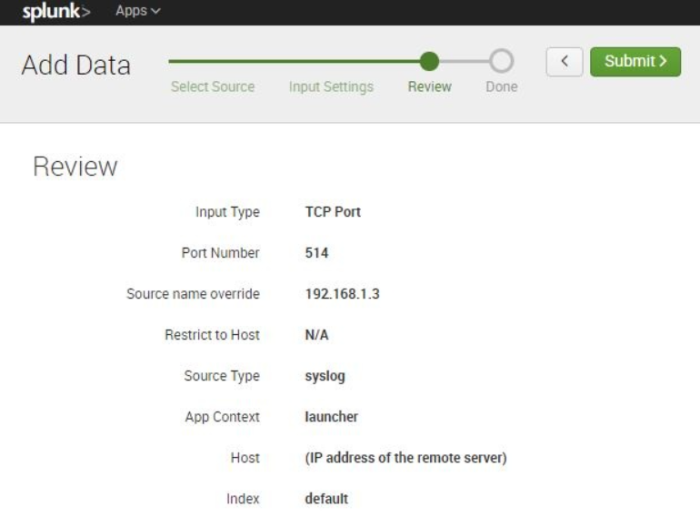
Check the settings on a result screen;

-
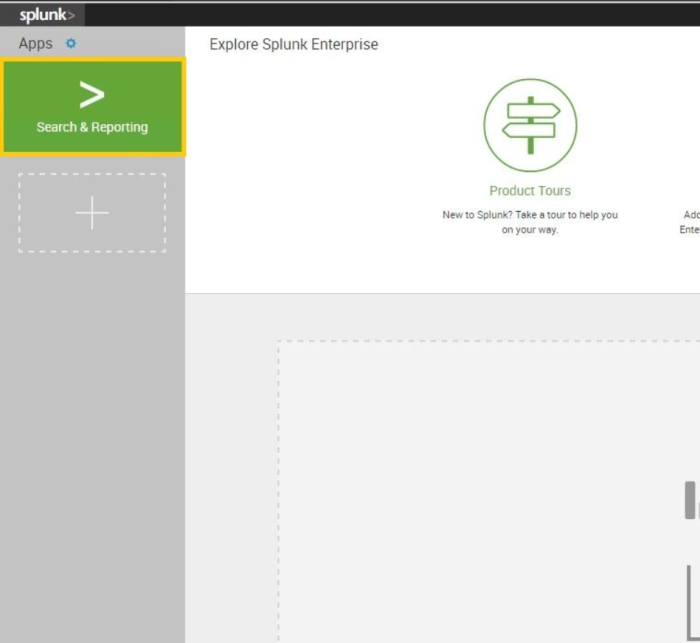
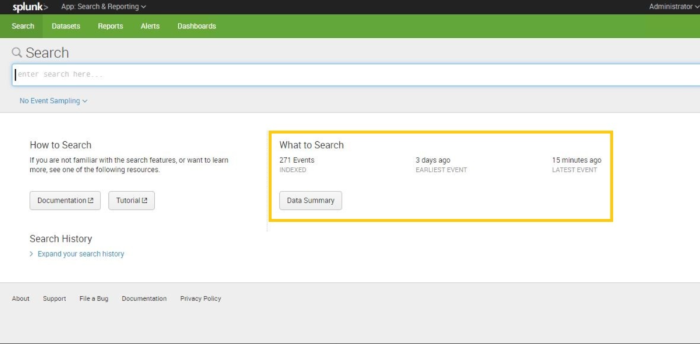
Open Splunk home page and press Search & Reporting;

-
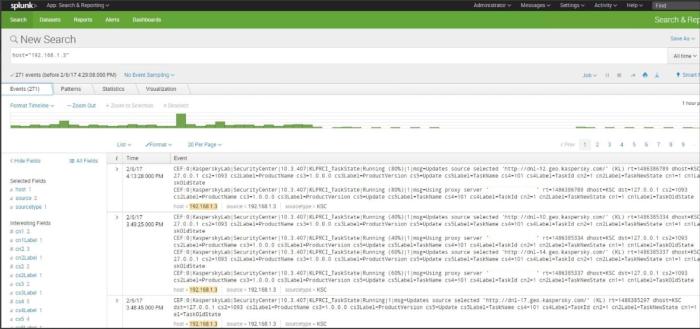
Make sure that KSC event were indexed by Splunk correctly as expected;

-
Right now you are able to see raw KSC events.

























0 Comments
Recommended Comments
There are no comments to display.
Please sign in to comment
You will be able to leave a comment after signing in
Sign In Now