Bobhond
Members-
Posts
7 -
Joined
-
Last visited
Everything posted by Bobhond
-
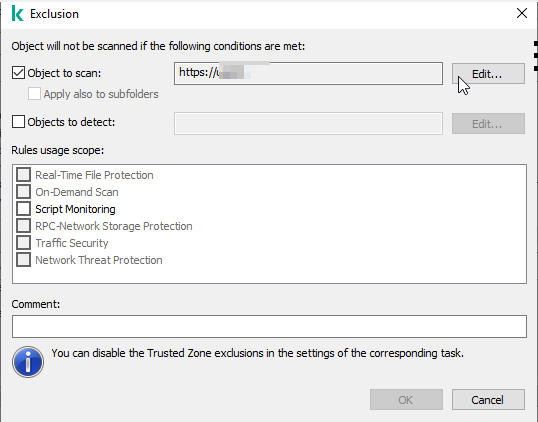
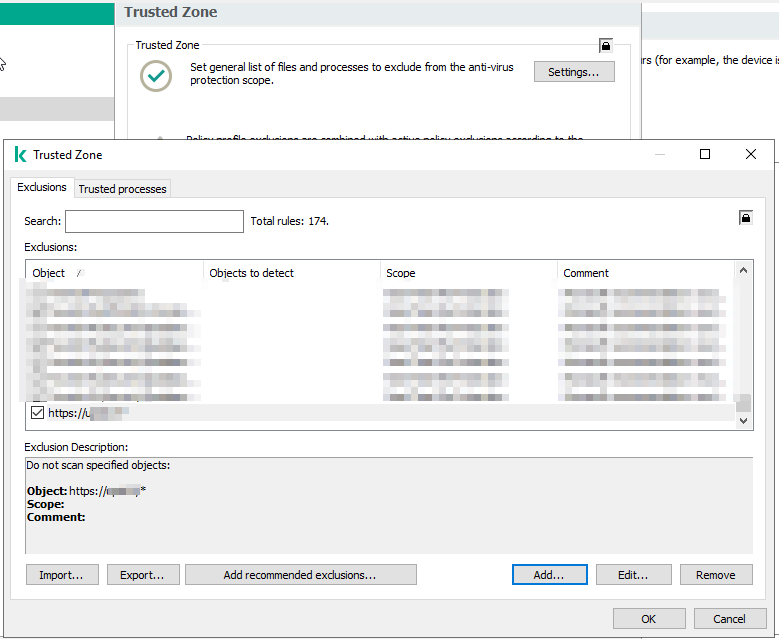
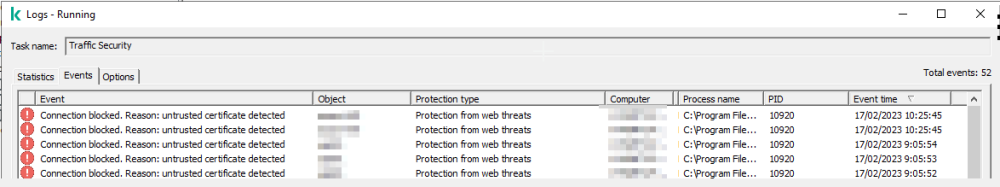
Hi! We are using Kaspersky Security for Windows Server (11.0.0.480, KSC 13.2) and are currently trying to figure out how to create a policy profile for our management servers which excludes self signed certificates. Currently, all internal websites (like web portal for switches, ...) with a self signed certificate return the same error in the browser: We know that this is caused by the component "Traffic Security" and that we can exclude these internal websites in the policy. But the server policy is applied to ALL servers, therefore we want to exclude these self signed sites only on our management servers. We want to create a policy profile with all our internal websites in a trusted zone, would this be the correct way to handle this? What do we have to enter in "object to detect" in order to exclude ALL self signed certificates from traffic security? Can someone please inform me? Kind regards
-
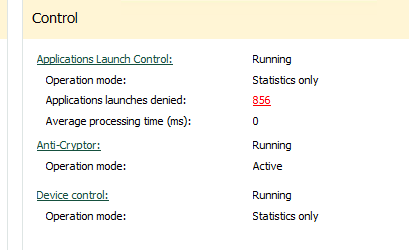
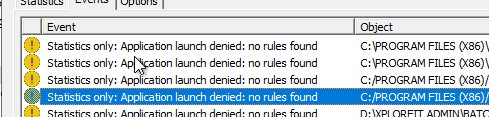
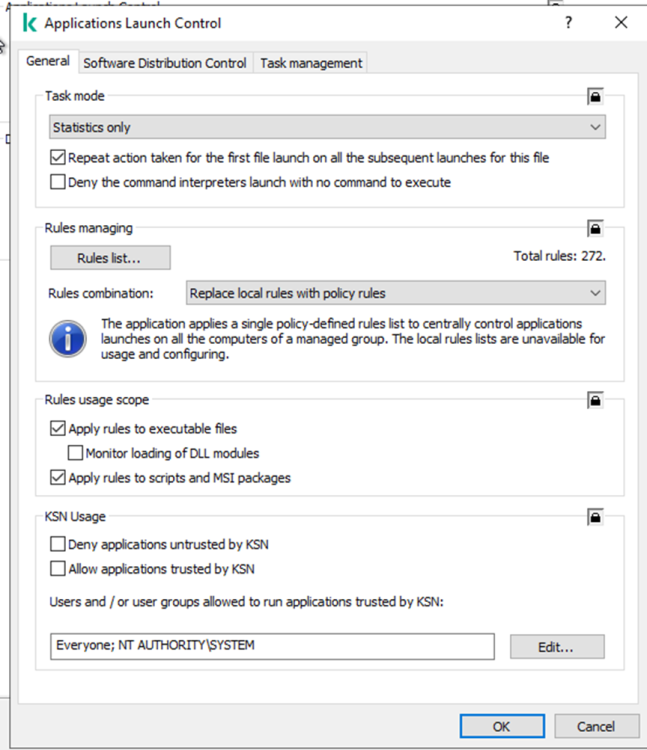
Hi, I noticed that "Applications Launch Control" in task mode "Statistics only" does block (deny) applications from starting. I believed that "Statistics Only" wouldn't block anything but in this case the opposite seems to be true. Whenever I see that an application is being blocked I add it to the "Rules list..." under "Rules managing" after which the application runs without any problems. The events all say that there are no rules found for applications that are being blocked. Does this have something to do with the option "Replace local rules with policy rules" under "Rules managing"? Can someone please point out why task mode "Statistics only" does block applications in "Applications Launch Control? KSC: 13.2 Kaspersky Security for Windows Server: 11.0.0.480 Best regards
-
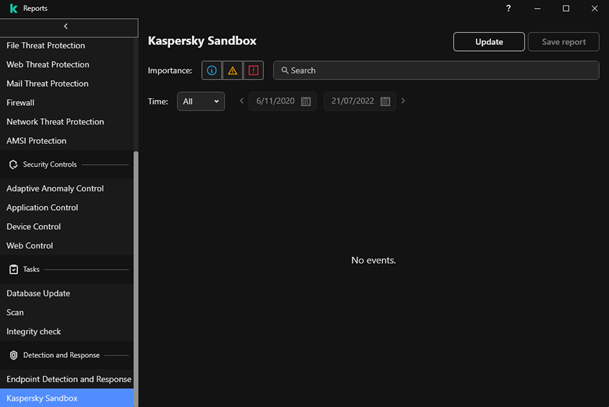
Hi, We have a sandbox that seems to be running fine. I can see that files were uploaded and checked but I can’t see (or can’t seem to find) which files where uploaded. Where can I find the names of the files that have been send to the sandbox? How can I see if these were real threats? I know that I can view reports of the sandbox on the clients themselves but isn’t there a more efficient way (in security center maybe)? Kaspersky Sandbox: 1.0.0.364 KCS: 13.2 Endpoint Agent: 3.12.0.382 Thanks for reading!
-
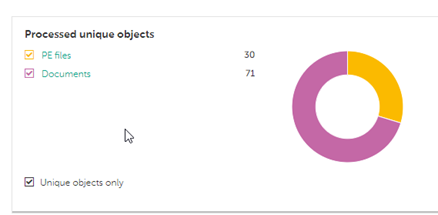
Hi Diego! Thanks a lot for replying! You are correct in assuming that we use an older version of KES: 11.6 (13.0 Administration Server). I didn’t know that the endpoint agent was going to be integrated in KES, that actually makes it easier to manage. We should definitely look into upgrading. I think I used a misnomer in my question, by policy I meant the locks next to the different options: There’s only “Kaspersky Sandbox integration settings” “under policy”. The IP of the server was added but the lock itself is not locked. That’s why I assume that the sandbox is currently doing nothing. So I guess all these need to be locked? Our screenshot of our sandbox traffic is way less spectacular (filtered on the month of January).
-
Hi, Several months ago a vendor installed a hardware kaspersky sandbox in our environment and configured the policies. At least I thought so because after several months there is still no data about processed objects. Under the properties of the Endpoint Agent I can see that the integration settings are under policy and that there is an active trusted connection with the sandbox. The policy underneath it “list of kaspersky sandbox servers” however is not enforced, although the IP-address of the sandbox is added. The same applies to the “Advanced settings” and “Threat Response”, non of the policies are enforced. So, I assume that the setup of our sandbox is incomplete, is this correct? Do all policies under “Kaspersky Sandbox integration” have to be enabled for the sandbox to work correctly? We have a Kaspersky Endpoint Detection and Resepone Optimum Add-on together with “Kaspersky Sandbox, Node European Edition”. Bobhond