All Activity
- Past hour
-
iuaFSIUNfyaUYF731 started following Kaspersky Plus quits unexpectedly
-
Is there any update on the "MR17" update? I certainly have many, many large files on the filesystems being scanned if that's the case. I've been experiencing this issue for what feels like a year or more now. Exact same symptoms as commonly reported over the last year or two. Full scan will always cause an application crash however, even when manual. System idle for many days will eventually cause a crash. Sometimes application can recover, other times application will fail to launch due to what appears to be the Kaspersky windows service locking up and cannot be restarted or stopped due to security and requires a reboot. I'm not totally comfortable submitting traces and have been watching from the sidelines.
- Today
-

Непонятки с Kaspersky Premium
andrew75 replied to Lucas Leo's topic in Kaspersky: Basic, Standard, Plus, Premium
Сами создаем проблему, сами ее решаем. Зачем было создавать тему, раз все равно советов не слушаете 🙂 -
Anthony Laptop joined the community
-
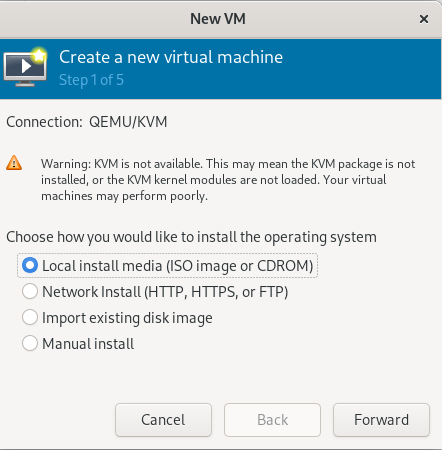
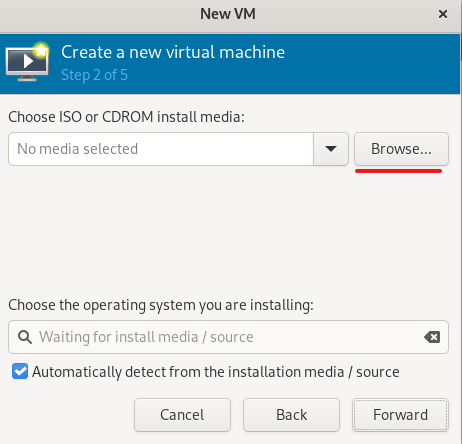
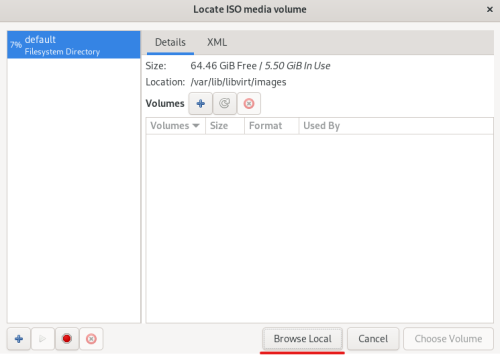
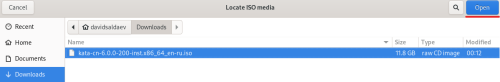
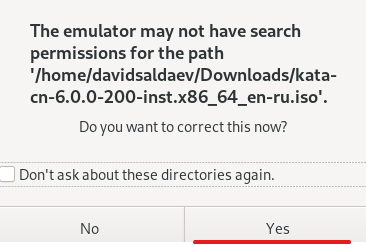
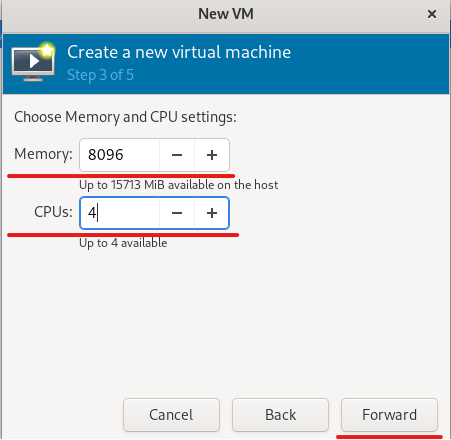
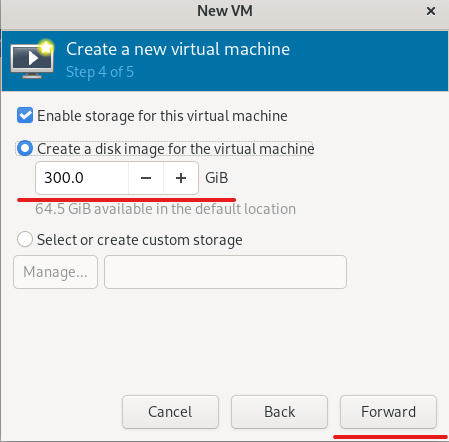
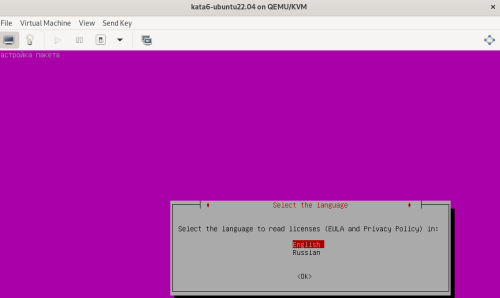
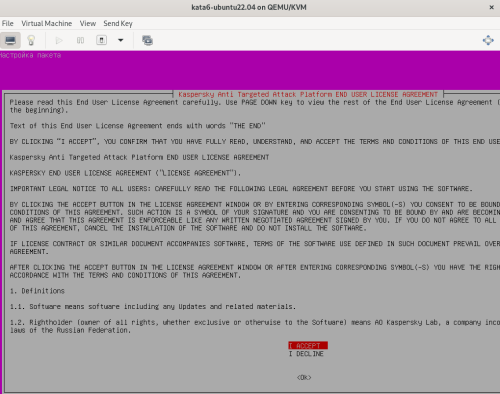
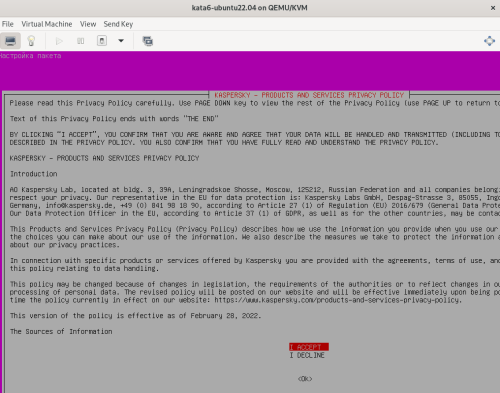
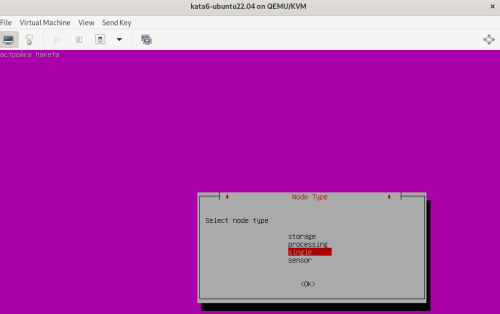
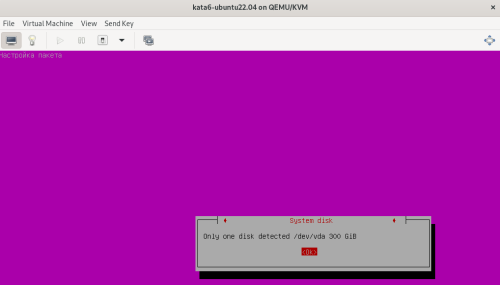
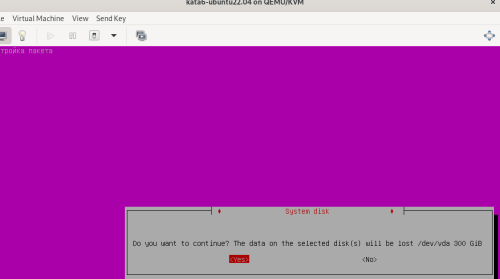
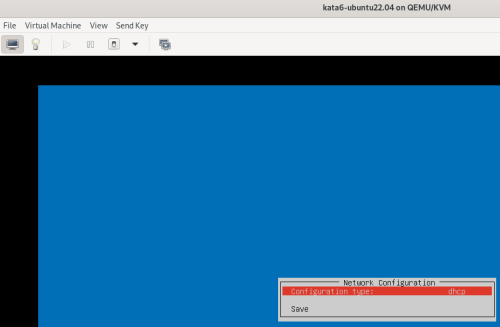
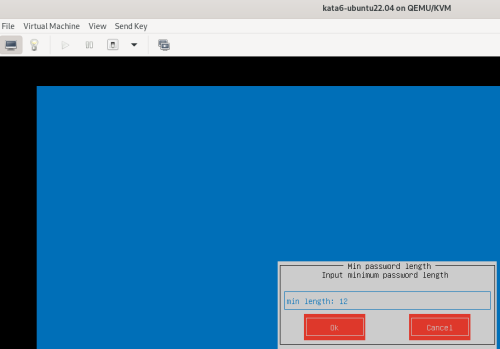
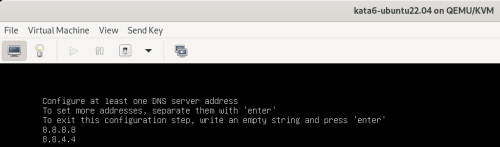
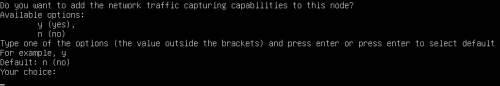
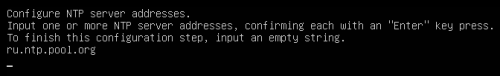
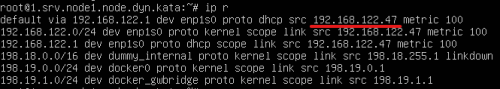
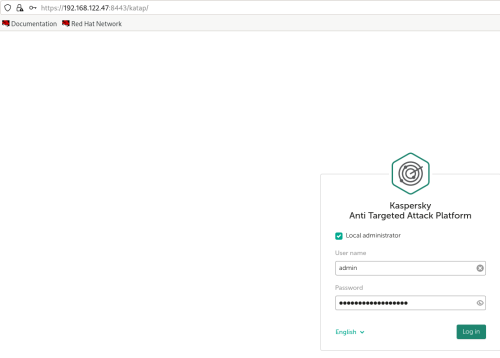
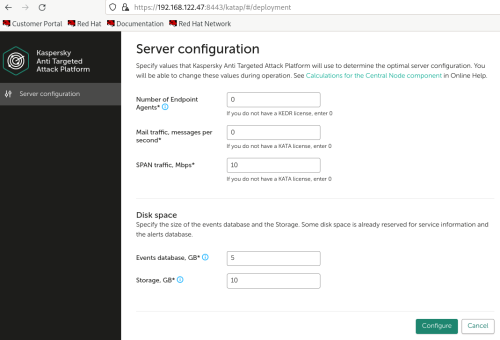
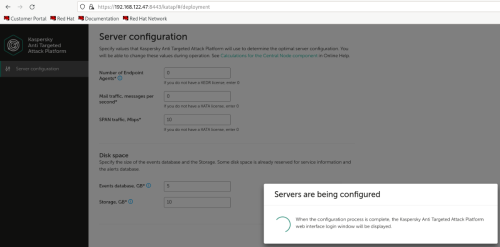
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Description Here's how to install KATA 6.0 Ubuntu edition in KVM environment - https://support.kaspersky.ru/KATA/6.0/en-US/265697.htm In the example below we use RHEL 9.3, installed as VM in VMware Workstation Pro 17.0 Step-by-step guide First, you have to install QEMU/KVM , all steps are described HERE Then install from Software application Virtual Machine Manager, here it's 4.1.0 version. After successful installation just open up Virtual Machine Manager application, and click on the icon "Create a new virtual machine" Assuming, you have KATA Ubuntu ISO locally in OS, choose option below and click "Forward" Click "Browse" and "Forward" Click "Browse Local" Locate KATA Ubuntu ISO and click "Open" Next, do the steps as shown on picture below Click "Yes" Assign resources to VM according to THIS article (ignore our settings below, it's just a demo) and click "Forward" Configure a disk (ignore our settings below, it's just a demo) and click "Forward" Name your VM, select a network and click "Finish" Now you should see installation window, proceed like you usually do with standard KATA installation on VMware In this window select ONLY "single", cause KVM supports only this type of installation Select a disk and click "OK" Wait a bit and you should see that installation starts, and now you just have to wait for next step of installation/configuration Now select subnets (usually use default ones) by pressing Enter Choose network > assign IP (static or dhcp, in our example we use dhcp) > set password length and password itself > configure DNS servers Choose if you want capture traffic via SPAN (y or n) > configure NTP servers That's it, KATA installed Now you can login to web UI and configure server, in our example IP of server is 192.168.122.47, let's login to https://192.168.122.47:8443 and voila "Configure" and wait for completion
-
Arachnoid joined the community
-
Ильмира Абдуллаева joined the community
-
Tiene Android
-

Why is renewal process so poor/shoddy?
Berny replied to Yoji's topic in Kaspersky: Basic, Standard, Plus, Premium
@Yoji You are welcome and thank you for your feedback. I hope you will be able to fix this issue, if not Kaspersky Tech Support is your best option. -
Непонятки с Kaspersky Premium
Lucas Leo replied to Lucas Leo's topic in Kaspersky: Basic, Standard, Plus, Premium
Всё нормально, друзья!!! После того, как в течение двух месяцев служба поддержки Касперского переливала из пустого в порожнее (как в старом анекдоте советских времен, когда мужик приходил в магазин купить туалетную бумагу, которой не было, а ему другой покупатель говорит - я им уже и унитаз приносил, и задницу показывал, а туалетной бумаги, как не было, так и нет), давая шаблонные неработающие рекомендации, я сделал все проще. Удалил вручную все папки и файлы с упоминанем Kaspersky из Program Files x86, Program Data, AppData, а также все ветки и ссылки реестра опять же с упоминанием Kaspersky. И заново его установил. И все работает, как часы - и сам компьютер, и Касперский Премиум. И в списке установленных программ он появился, и следов удаленного Касперского больше не появляется... И не потребовалось никаких танцев с бубнами с переустановкой винды и восстановлением системы. Вот как-то так... -
Khalilel77483 joined the community
-
Franciscoet00016 joined the community
-
Victor Manuel SG joined the community
-
Yousefeg92075 joined the community
-
Julissaas32233 joined the community
-
Вопрос в следующем: в подписке, можно подключить три устройства, одно моё, другие для родителей, родители тыкают во всё подряд и плохо разбираются в компах, можно ли ограничить второстепенных пользователей в правах на изменение в настройках и лицензиях, чтобы они не могли на ровне со мной добавлять устройства, управлять лицензией и т.д. Надо что бы мой первый аккаунт был "Admin", а другие "User" (а лучше "Lamer").
-
Renan Corassa started following Deploy Kavremover through KSC
-

Deploy Kavremover through KSC
Renan Corassa replied to Hichem Bouslama's topic in Kaspersky Endpoint Security for Business
Unfortunately it is not possible. Locally only.- 1 reply
-
- 1
-

-
Headshot80 joined the community
-
No success so far unfortunately although your help is very appreciated and I did all things exactly as suggested, seem logical of course and would have been the things done by myself (or very near to it), I just wanted to avoid a complete uninstall, new download etc. but did it Uninstalled successfully, I did not see a single Kaspersky file after this (the uninstall routine suggested to keep the subscription data but I removed them too because maybe exactly this caused problems, could not be wrong in my opinion) I did NOT try to open the UI immediately after the new installation (finished successfully without any errors or so) but did a shutdown and restart instead, cannot be wrong in my opinion either because the software should know/check if it exists on the pc and ask for the license or something similar even after 2, 5 or 20 restarts or not.. After shutdown/restart I had to try to open the software/UI of course, you said "The new application has to synchronize/connect with (your) MyKaspersky account to *pick-up* the License key".. - "You must sign into the Kaspersky application - using the same email address that was used to buy the Kaspersky Standard subscription. Don't try an add an Activation code & OR a License key - anywhere!!" BUT I only got this window asking for an activation code again unfortunately which is a real mystery to me because I did not make a single mistake in installing etc. so I am on a dead end again and do not have any ideas anymore to solve this, seems to me that the software thinks that I do not have a valid license or so maybe but I never did anything other as buying the software legally and install it, all other things would be very silly with an av program anyway (and all is shown as valid in my account with expiration data, license number etc.) So how to continue, would the support give me an activation code in this situation, maybe ? Not sure if this would work anyway or if things are messed up already in hidden areas of the registry or so (not by me but by Kaspersky suspecting wrong things maybe etc.) I will definitely not make a complete os reinstall with creating images and all things necessary, I did never expect that installing/activating Kaspersky would be so difficult, I really would like to use it but am not far from giving up and I think the only solution (if any) would be trying an activation code By the way I used Emsisoft Ant-Malware last years without any problems but the license expired and only Windows 10 and higher get program updates anymore (completely removed from the pc before installing Kaspersky of course), it would have been possible to get antivirus definitions for the longer future with Emsisoft and Windows 7 just using an older program version but a) I considered 40 euros yearly for a single pc license rather expensive and b) heard good things about Kaspersky of course and just wanted to try it but see above, this German security nonsense is irrelevant to me although I live in this not so wonderful country, still using Windows 7 may seem strange but I have my reasons for it and do not need other versions for the things I do and I checked that Kaspersky is okay with 7 before buying of course so I really think that this is not the reason for this strange activation problem but what else.. So how to continue, asking the support for an activation code and try it ? I do not know if you are in the official Kaspersky support or just a helpful person so if you still have another idea I am happy with it but there should be a realistic chance or rather high probability for solving the problem by it, does not make much sense to try this uninstall/new install thing 10 times when chances are very low for a solution by this By the way I cannot imagine that I am the only person with this problem or what about this...
-

No more licences for KAV
Berny replied to Zewkia Araaisa's topic in Kaspersky: Basic, Standard, Plus, Premium
@Zewkia Araaisa Welcome. Please check this -

App Lock requesting password to often
Berny replied to matiasbsm's topic in Kaspersky: Basic, Standard, Plus, Premium
@matiasbsm Welcome. Please continue here Thank you.- 1 reply
-
- 1
-

-
Übernahme der Lizenz bei Rechnerwechsel
Dr.Mabuse replied to Peter Frömbgen's topic in Für Privatanwender
Hallo, ich habe 2 Laptop und 3 Android geschützt da ich eine 5 Platz Lizenz habe. Zeige ich das so an wie Du steht da... 3 von 5 Geräten geschützt. Hä ? 🤔 In MyKaspersky werden alle 5 als geschützt angezeigt. -
harlan4096 started following App Lock requesting password to often
-
Servus Leut, ich habe es jetzt so gemacht. Kaspersky VPN und Secure deinstalliert. Kaspersky VPN und Secure neu installiert. Allem zugestimmt was notwendig ist. Unten auf ICH HABE EIN ABONEMENT geklickt. Lizenzschlüssel eingegeben. Meldung ( Sinngemäß ) : Achtung ! Ihr Code ist schon in MyKaspersky aktiviert ignoriert bzw bestätigt. MyKaspersky angemeldet auf dem Android. Meldung: Gut gemacht ! Sie haben nun 365 Tage Schutz. Das wars 👍😁
-
matiasbsm started following App Lock e o excesso de solicitações. and App Lock requesting password to often
-
Good afternoon. I would like to know if there is any configuration to prevent APP Lock from requesting the password or fingerprint every time an application is opened, so that it is required only once when unlocking the phone or after a certain period of time (for example, every 5 minutes). It is extremely irritating to have to unlock the app repeatedly, even if you have used it in the last 10 seconds. Navigating between two apps with the lock activated makes the experience very slow. Other locking apps already have this function available. Is this configuration available? If not, where can I contact to suggest this improvement? Thank you
-
Boa tarde. Gostaria de saber se há alguma configuração para evitar que o APP Lock solicite a senha ou impressão digital toda vez que abrir um aplicativo, de modo que seja exigido apenas uma vez ao desbloquear o celular ou após um intervalo de tempo determinado (por exemplo, a cada 5 minutos). É bastante irritante ter que desbloquear o aplicativo repetidamente, mesmo após o uso recente. Alternar entre dois aplicativos com bloqueio ativado torna a experiência muito lenta. Outros aplicativos de bloqueio já possuem essa função disponível. Existe essa configuração disponível? Se não, onde posso entrar em contato para sugerir essa melhoria? Obrigado.
-
Hallo, beantwortet irgendwie meine Frage nicht.
-
harlan4096 started following No more licences for KAV
-
Получение serial number на rpi4 в KasperskyOS CE
barkov_a replied to Yura Beznos's topic in KasperskyOS, Разработка
Добрый день. Для текущего релиза 1.1.1.40 нельзя получить серийный номер. Мы можем рассмотреть добавление данной функциональности, но не могли бы вы, пожалуйста, предоставить краткое обоснование необходимости. -
Zewkia Araaisa started following No more licences for KAV
-
No more licences for KAV
Zewkia Araaisa replied to Zewkia Araaisa's topic in Kaspersky: Basic, Standard, Plus, Premium
Just found out from local "dealer" in my country, that there are no more licences for KAV and they are offering only for Kaspersky standard/plus/premium, among other Kaspersky products, which are not KAV and KIS. -
Little rant about licence price
-
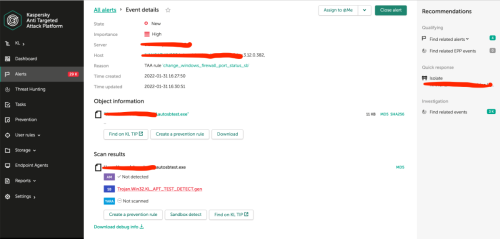
Advice and Solutions (Forum Knowledgebase) Disclaimer. Read before using materials. Problem Sometimes it's necessary to check KATA detects, for example IDS, IOA, Sandbox detects. Step-by-step guide IDS detects (SPAN) To check IDS detects (SPAN) you can use tcpreplay utility on server configured to receive SPAN traffic. KATA 4.0/4.1 tcpreplay package for such versions could be found here https://rhel.pkgs.org/7/epel-x86_64/tcpreplay-4.4.4-1.el7.x86_64.rpm.html KATA 5.+ and tcpreplay tcpreplay package is not installed by default, so you should install it manually, using step-by-step guide below: 1) Download this package from HERE 2) Place downloaded file tcpreplay_4.3.2-1build1_amd64.deb to your KATA node. For example, use scp: [user@host]$ scp <your-path>/tcpreplay_4.3.2-1build1_amd64.deb admin@<kata-ip>:/tmp 3) Run installation on your KATA node with the next command: [admin@katahost]$ sudo dpkg -i /tmp/tcpreplay_4.3.2-1build1_amd64.deb Success! Now you can use tcpreplay on your KATA 5.+ or any other UBUNTU system! Before using tcpreplay you should enable tx capture for span: KATA 3.7.* In technical support mode from user root run following commands : systemctl stop apt-preprocessor.service systemctl stop suricata.service rmmod pf_ring Edit file /etc/modprobe.d/pf_ring.conf: change line: options pf_ring enable_tx_capture=0 min_num_slots=16384 # tx capture is disabled to: options pf_ring enable_tx_capture=1 min_num_slots=16384 # tx capture is enabled save file. Start pfring and related services back: modprobe pf_ring systemctl start suricata.service systemctl start apt-preprocessor.service KATA 4.0/4.1 Edit file /etc/modprobe.d/pf_ring.conf: change line: options pf_ring enable_tx_capture=0 min_num_slots=16384 # tx capture is disabled to: options pf_ring enable_tx_capture=1 min_num_slots=16384 # tx capture is enabled save file. In technical support mode from user root run following commands: systemctl stop docker rmmod pf_ring modprobe pf_ring systemctl start docker tx capture for span is now enabled KATA 5.0/5.1/6.0 - see https://forum.kaspersky.com/topic/how-to-enable-tx-capturing-in-kata-katakedre-37514/ Eicar traffic detect: Upload EICAR-Test-File_TCP.pcap sample to server with SPAN interface, then execute command from root shell: tcpreplay -i ens34 EICAR-Test-File_TCP.pcap # ens34 in this example is SPAN interface Nmap traffic detect: Scenario is the same as for Eicar detect, only .pcap file differs (# tcpreplay HackTool.Nmap.HTTP.C&C.pcap). After testing detects from span we strongly recommend to disable tx capture back again by the same way as described above for enabling. AM Engine Use EICAR's - https://www.eicar.com/ Email - send the EICAR via SMTP to KATA 25 port. (SMTP processing needs to be Enabled of course). ProTip: you may use local swaks mail client on CN to skip elaborate mail setups. swaks examples swaks --server 127.0.0.1 --port 25 --from antony@test.org --to cleopatra@test.org --attach eicar.com swaks --server 127.0.0.1 --port 25 --from antony@test.org --to cleopatra@test.org --body "link_to_EICAR_here" Endpoint - put an EICAR file to the endpoint and fetch it using GetFile task, queue for scanning. YARA detects By default, no YARA rules are supplied with the product. For test purposes one can use a test rule from YARA docs https://yara.readthedocs.io/en/v4.1.0/writingrules.html rule ExampleRule { strings: $my_text_string = "text here" $my_hex_string = { E2 34 A1 C8 23 FB } condition: $my_text_string or $my_hex_string } The rule will mark any analyzed object containing $my_text_string or $my_hex_string. IoA detects To check IoA detect (IoA detects can be checked only if you have KEDR license): Copy .bat file from attached archive Test_IOA.rar(not_infected) to any folder on host with installed EDR and start it. After some time(KATA need several minutes to transmit and process telemetry from EDR) check alerts in KATA. Alert should have type ioa_test_detect. For testing IoA detects on host more than once, .bat file should be placed to different locations on this host. On the host with installed KEA run command below in the cmd.exe shell: wmic.exe sfdguninstallkasperskyblabla There can be something else instead of sdfg and blabla, important part of command is uninstallkaspersky Command execution will fail with error, but it's not important. After some time new IoA detect should appear in KATA web-interface. IoC detects One can use the custom rule for testing - Ioctest.zip (infected123) - it is triggered for "c:\windows\system32\calc.exe" Automatic sandboxing in EDR To check automatic sandboxing: Unpack the archive with sample, use default password for samples: autosbtest.zip NB! Do not change MD5 of the sample. Run the sample on EDR-protected host and wait for automatic SB detect: Sandbox detect To check sandbox detect we can use file SA_sleep.exe from archive no_am_detection sample.rar. Password is inside text document in archive. Go to KATA senior security officer web-interface. Choose Storage → Upload and upload SA_sleep.exe from attached archive for KATA checking. Kata should enqueue it to sandbox , then a bit later verdict from SB should be Suspicious Activity. If SA_sleep.exe produces Not detected verdict then please use test_sb.bat from the test_sb.rar URL reputation Firstly, confirm K(P)SN is configured and works properly. MD5 used in this example should return UnTrusted status: Check KSN on KATA command for KATA 4.+ and 5.0: docker exec -it `docker ps | grep ksn_proxy| awk '{print $1}'` /opt/kaspersky/apt-ksn_proxy/sbin/ksn_client --ip 127.0.0.1 --hash 9C642C5B111EE85A6BCCFFC7AF896A51 for KATA 5.1: docker exec -it $(docker ps | grep ksn_proxy| awk '{print $1}') /opt/kaspersky/apt-ksn-proxy/sbin/ksn_client --ip 127.0.0.1 --hash 9C642C5B111EE85A6BCCFFC7AF896A51 Secondly, For traffic: access http://bug.qainfo.ru/TesT/Aphish_w/index For email (SMTP processing needs to be Enabled), send the link above via e-mail. For quick and dirty test: swaks examples swaks --server 127.0.0.1 --port 25 --from fisherman@test.org --to cleopatra@test.org --body "http://bug.qainfo.ru/TesT/Aphish_w/index"
-
и у меня уже нет